- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Need clarification on URL Filtering logs
- LIVEcommunity
- Discussions
- Network Security
- Next-Generation Firewall Discussions
- Need clarification on URL Filtering logs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-15-2024 11:51 PM
Hi everyone,
Please help me get through this.
We have configured PA-450 firewall and everything is working fine as expected.
But, We have used the option URL category in the security policy without an URL filtering profile for all user group. Which is working fine but I cant see any URL user activity report.
But we need block URL summary report.
Then I found out that we need block or alert action in order to get URL logs.
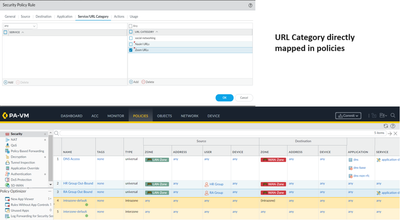
Current Scenario
=================
(Its not the real configuration setup from the firewall, just a prototype)
The above screenshot is the current scenario of the security policies which has URL category directly mapped in polices.
There are no Block URL user activity report generated.
Please observe the below workaround.
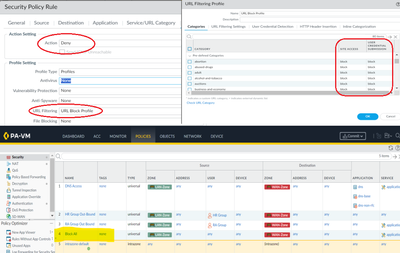
Workaround
============
Please observe the above screenshot.
Above we have all the URL category mapped allow policies which generates no logs.
What if I create a security policy with a URL profile which blocks all the category at the bottom.
All the allowed traffic will hit on the above rules for all user groups and other traffics will hit on the bottom block rule and generates the Block URL user activity summary ... right ?
Please correct me if I am wrong.
NOTE: We don't want to use URL Filtering Profile. Instead we need the carry on with current scenario.
Please help me with this doubt.
Thanks in advance 🙂
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-16-2024 06:54 AM
correct
the log is generated from the url decoder action, which is only triggered if you let the 'base' traffic (tcp connection) pass which is achieved by setting the security rule to allow
Advantage of this approach is also that users will receive a nice block page in their browser versus a failed connection with no context
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-16-2024 12:38 AM
you'll need to set that 'block all' rule to allow since a deny rule will not put packets into l7 for inspection, so you wont hit the url filtering block action, and get no logs
Dare i ask why you're not using url filtering to allow url categories? 😉
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-16-2024 01:58 AM
Hi @reaper
Thank you for your reply,
So if we configure the last Block Rule and set all the predefined URL category to "Block" and rule as "Allow"
We will get the URL user activity summary right ?
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-16-2024 06:54 AM
correct
the log is generated from the url decoder action, which is only triggered if you let the 'base' traffic (tcp connection) pass which is achieved by setting the security rule to allow
Advantage of this approach is also that users will receive a nice block page in their browser versus a failed connection with no context
PANgurus - Strata & Prisma Access specialist
- 1 accepted solution
- 2350 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Not able to log XFF (Actual Client IP) in PaloAlto Logs even when we enable XFF and URL filtering profile in Palo's in Next-Generation Firewall Discussions
- Header Fields for Syslog for Rapid7 in Next-Generation Firewall Discussions
- Clarification on System Log Subtypes Categorized as Security Events in Next-Generation Firewall Discussions
- Does Panorama Forward These Events to External SIEMs via Syslog by Default? in Panorama Discussions
- URL filtering - allows blocked traffic in Next-Generation Firewall Discussions