- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
The allow security policy configured with the app-ID "netbackup" and an "application-default" as a service doesn't work correctly.
- LIVEcommunity
- Discussions
- Network Security
- Next-Generation Firewall Discussions
- Re: The allow security policy configured with the app-ID "netbackup" and an "application-default" as a service doesn't work correc
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
The allow security policy configured with the app-ID "netbackup" and an "application-default" as a service doesn't work correctly.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-19-2023 04:39 AM
Dear and valuable Live Community Members,
I have a problem understanding the below-described behavior in regard to the security policy used in the firewall:
We have a firewall policy configured to allow NetBackup traffic, but if we configure it by setting the "Application" tab to "netbackup", it often doesn't work (the behavior is random). And if we configure the policy specifying the TCP ports used by netbackup, it works correctly.
As you can see below we have now two allow policies to make it work:
-----------------------------------------------------------------------------------------------------------------------
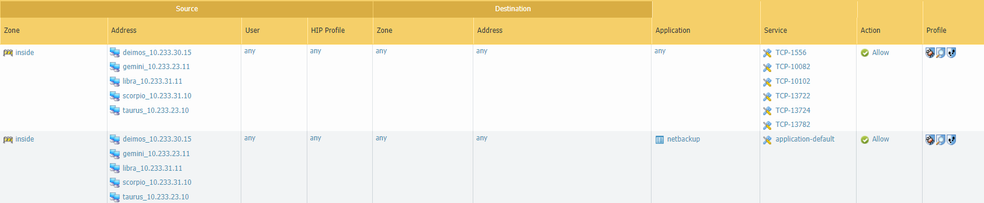
1) The security policy that specifies the ports used by the application (Application - Any; Service TCP/1556,13724,13782,13722,10102,10082) - it works fine
2) The security policy configured with the app ID "netbackup" and an "application-default" as a service - doesn't work correctly
I could verify the list of standard ports and as per the KB Tips & Tricks: What Does Application-default Under Service Mean? I was sure that we will need only one policy and that the 2nd policy should be enough for this.
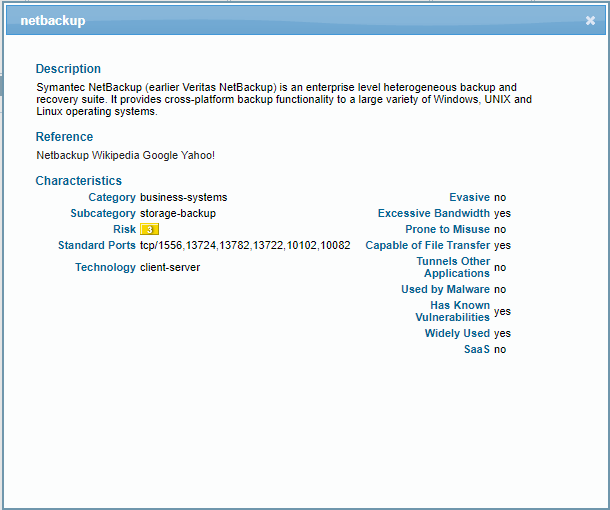
Could you please help me to understand why the "Application" field, is not working as expected with the application-default?
I hope someone could help me out and let me know if there is something that needs to be corrected (configuration-wise) if that's maybe a bug or an expected behavior...
I would kindly like to ask you for some help and advice on this one.
Thank you in advance!
Cheers!
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-20-2023 02:03 AM
Hi A_Adamski,
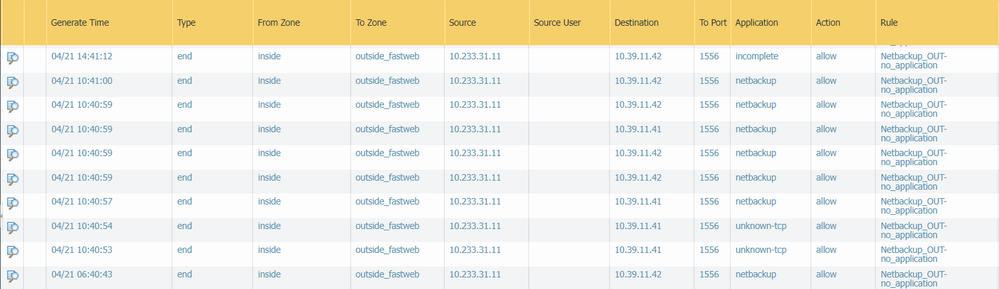
I agree with you, you should only need 2nd rule as it contains all ports you included in screenshot.
that is a weird problem, two question if you don't mind.
1) what is your application version on the dash board - is it Application Version 8699-7991 (04/19/23) ?
2) when you look at the logs for the first rule, which application(s) do you see in the logs?
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-24-2023 05:14 AM
Hello Y-AlwaysMe,
1) The Application Version is now 8697-7981 (04/14/23), but it as issue we've got in the past with the 8693-7959 (end of March)
2) The firewall seams to be recognizing the application correctly
Is there anything I might be miing out and should verify/correct, or should I ask PA TAC for some support on this one?
Thank you in advance!
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-24-2023 05:48 AM - edited 04-24-2023 05:59 AM
Hi A_Adamski,
Thank you for information. I suspect the problem will potentially be the unknown-tcp, when you enable Bytes Sent & Bytes Received and look the unknown-tcp between the src and dst IP addresses, I am guessing there will be actual data that is eq or more than 200 bytes in the sent and received columns, which could potentially explain why it would randomly stop working as most packets are normal TCP/1556 packets, and then every now and then unknown-tcp will be sent and it will stop working against the application rule.
Because the application rule you allowed only contains netbackup and you did not define unknown-tcp in your application rule.
I personally think there are two options use the L4 service-port based rule or look at custom application / app override - see that article by Reaper.
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000Clc6CAC
- 2889 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- GloablProtect + Explicit Proxy blocks WSL traffic. in GlobalProtect Discussions
- Conditional Advertisement / BGP Failover with Dual ISP — How to Remove ISP1 Routes on Internet Loss? in Next-Generation Firewall Discussions
- Connectivity with Panorama in VM-Series in the Public Cloud
- Syncing Specific Entra ID Groups to Cloud Identity Engine in GlobalProtect Discussions
- Max number of units (aeX.Y subinterfaces) supported under a single AE interface? in Next-Generation Firewall Discussions