- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
User ID (with Windows Agent) not working
- LIVEcommunity
- Discussions
- Network Security
- Next-Generation Firewall Discussions
- User ID (with Windows Agent) not working
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-01-2023 11:28 PM
Hi,
we set up User ID based on these docs:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClRyCAK
Konfiguration and installation is working:
- the agent installed on server 2019 DC is getting infos
- the firewall (PA-220 9.1) is getting infos from the agent
- the users are displayed in monitoring
but:
- we can not select users in security policies
- we can manually add users in the policies - then the policies never matches.
Any ideas?
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-03-2023 01:24 PM
Hello @FloriReus
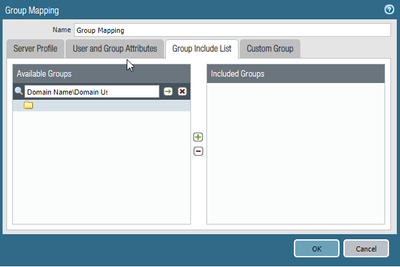
based on what you described, the only thing coming to my mind is missing inclusion of "Domain Users" group under: Device > User Identification > Group Mapping > [Name] > Group Include List > add: "Domain Name\Domain Users". This should cover all AD users. Could you make sure this is in the place?
Kind Regards
Pavel
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-03-2023 01:24 PM
Hello @FloriReus
based on what you described, the only thing coming to my mind is missing inclusion of "Domain Users" group under: Device > User Identification > Group Mapping > [Name] > Group Include List > add: "Domain Name\Domain Users". This should cover all AD users. Could you make sure this is in the place?
Kind Regards
Pavel
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-03-2023 08:03 PM - edited 03-03-2023 08:12 PM
Hi @FloriReus ,
The security policy drop down only shows groups. You need to manually type in users. https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClXWCA0 (It will also show previously typed in users.)
Could you add the user in the security policy exactly how you see it in the Monitoring tab, lan\user1, and let us know if that works?
Thanks,
Tom
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-06-2023 01:31 AM
Ah, thank you!
I already got this hint.
This brought me to a next issue - I can not add groups as the firewall can not read the DC. There is just no group in the list to add. (it seems reachable in general, if I shut it off I get a real error).
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-06-2023 01:33 AM
I tried this already (see attached screenshots). seems not top work.
but thanks for the link!
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-06-2023 04:07 AM
Hello @FloriReus
thank you for reply.
To make sure there is no mis-understanding please replace: "Domain Name" with your organization's real AD domain name.
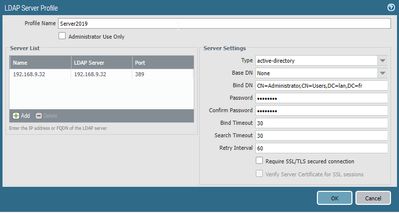
Regarding the issue you described, when you configure LDAP profile under: Device > Server Profiles > LDAP > [LDAP Profile Name], make sure that under Server Settings you configure Base DN that covers your entire domain. You can find that information from Windows CMD by issuing: dsquery *
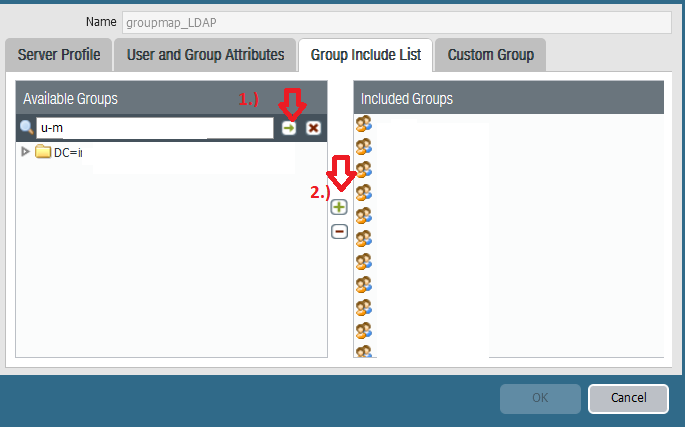
The Base DN is first returned entry on the top. The Base DN is the starting point an LDAP server uses when searching for users authentication within your Active Directory and if this is configured correctly this is what you will see under "Available Groups" in Group Mapping Settings. You should be able to type AD group name and press search button, then "+" button to add it to include list:
Kind Regards
Pavel
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-06-2023 04:33 AM
yes, you are right!
I missed the baseDN; now it's working!
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-06-2023 08:27 PM
Hello @FloriReus
thank you for getting back to me. Based on your screen shot, there are 2 additional things I would suggest:
- Enable LDAPS by selecting: "Require SSL/TLS secured connection" if possible to secure LDAP traffic.
- Add an additional LDAP server for redundancy to avoid single point of failure.
Kind Regards
Pavel
- 1 accepted solution
- 5415 Views
- 7 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- GP Login Lifetime? in GlobalProtect Discussions
- GlobalProtect Agent constantly 'Not Responding'. in GlobalProtect Discussions
- Getting 'Unidentified network' when connected to Global Protect - 6.2.8 in GlobalProtect Discussions
- Pangps service stop after system restart in windows 11. in Next-Generation Firewall Discussions
- [Let me know reason & workaround] Global Protect Agent ver6.3.3 “PanPUAC_xxx.dat” does not work (auto create or renew, failed to open). in GlobalProtect Discussions