- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Panorama can't show up traffic log
- LIVEcommunity
- Discussions
- Network Security
- Panorama Discussions
- Panorama can't show up traffic log
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Panorama can't show up traffic log
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-13-2022 04:25 PM
We have two panorama and HA.
Today our active panorama was broken caused by VM datastore issue .
Secondary Panorama taken active role , but We can't see any traffic log at the Monitor tab.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-13-2022 04:32 PM
jkim3@lvnv-now-mgt-pan(secondary-active)> show log-collector all
Serial CID Hostname Connected Config Status SW Version IPv4 - IPv6
---------------------------------------------------------------------------------------------------------
000710xxxxx 2 esca-now-mgt-pan no Out of Sync 10.1.3-h1 10.53.9.54 - unknown
Redistribution status: none
Last commit-all: none, current ring version 3
SearchEngine status: Active
md5sum updated at 2022/01/13 14:01:27
Certificate Status:
Certificate subject Name: 0e070ba7-7aec-4663-ab53-7a2ea571fec6
Certificate expiry at:
Connected at:
Custom certificate Used:
Last masterkey push status: Unknown
Last masterkey push timestamp: none
Serial CID Hostname Connected Config Status SW Version IPv4 - IPv6
---------------------------------------------------------------------------------------------------------
00071xxxxx 5 lvnv-now-mgt-pan yes In Sync 10.1.3-h1 10.93.9.54 - unknown
Redistribution status: none
Last commit-all: commit succeeded, current ring version 3
SearchEngine status: Inactive
md5sum updated at ?
Certificate Status:
Certificate subject Name:
Certificate expiry at: none
Connected at: none
Custom certificate Used: no
Last masterkey push status: Unknown
Last masterkey push timestamp: none
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-13-2022 04:42 PM
Thank you for the post @JeffKim
Are your managed Firewalls configured to use both Panorama's IP addresses under: Device > Setup > Panorama Settings > Panorama Servers ?
Is your secondary Panorama using the same time/time zone as managed Firewalls?
Could you confirm that logs are coming by: show logging-status device <Firewall S/N>
Kind Regards
Pavel
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-13-2022 05:02 PM
1. Yes
2.Yes
3.
Log Collector
'Log Collection log forwarding agent' is active and connected to 10.93.9.54
config Not Available Not Available 0 0 0
system 2022/01/13 14:28:19 2022/01/13 16:46:25 2971756 2971746 4015
threat 2022/01/13 14:27:25 2022/01/13 16:46:25 1766377018 1766377008 2448368
traffic 2022/01/13 14:36:52 2022/01/13 16:48:07 1534220641 1534210553 11715931
hipmatch Not Available Not Available 0 0 0
gtp-tunnel Not Available Not Available 0 0 0
userid 2022/01/13 14:21:37 2022/01/13 16:46:25 169621989 169621979 569726
iptag Not Available Not Available 0 0 0
auth Not Available Not Available 0 0 0
sctp Not Available Not Available 0 0 0
globalprotect 2022/01/13 14:20:13 2022/01/13 16:46:25 3114386 3114376 24217
~
~
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-31-2022 02:39 AM
What was the solution? We probably have the same problem.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-31-2022 06:43 AM
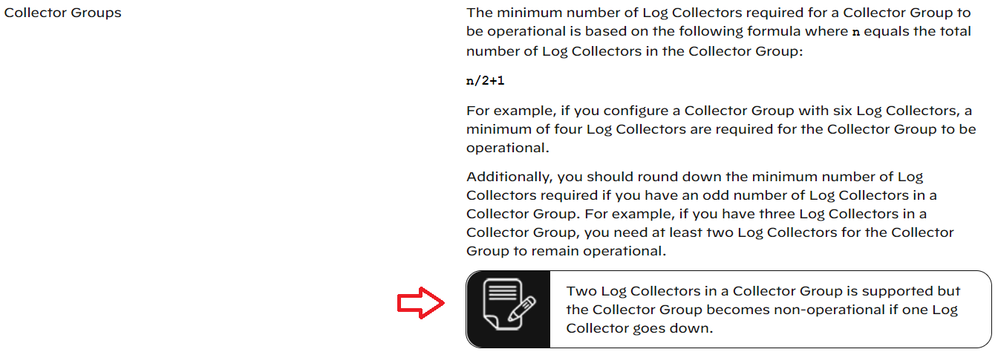
the minimum master node is n/2 + 1.
we need 3 log collectors to avoid this issue.
we still use two log collectors.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-31-2022 02:55 PM
Sorry to step in, the requirement for n/2 + 1 was introduced with PAN-OS 10 and later:
The behavior with one faulty log collector is therefore expected.
Kind Regards
Pavel
- 6664 Views
- 7 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- GRPC status UNAVAILABLE in intelligent offload in VM-Series in the Private Cloud
- Not able to log XFF (Actual Client IP) in PaloAlto Logs even when we enable XFF and URL filtering profile in Palo's in Next-Generation Firewall Discussions
- Cannot Access Primary in HA Pair – Need Failover & Recovery Advice" in Next-Generation Firewall Discussions
- Unable to reach Palo Alto - Global Protect Portal. in GlobalProtect Discussions
- ION Security Stack in Advanced SD-WAN for NGFW Discussions