- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Unable to push tempalte to new firewall
- LIVEcommunity
- Discussions
- Network Security
- Panorama Discussions
- Unable to push tempalte to new firewall
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Unable to push tempalte to new firewall
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-24-2024 06:17 AM
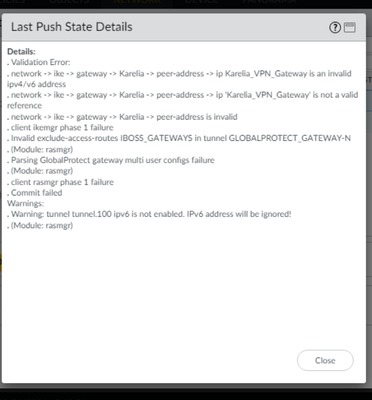
I have setup a couple of new firewalls and I am unable to push the template from panorama. Also device group has not yet been pushed.
Should I deploy template or device group first?
See the errors below..
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-24-2024 12:52 PM
Seemed to not be giving that error anymore.. but now seeing the below. Do I need to remove or disable something in the new firewall?
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-28-2024 10:54 PM - edited 04-28-2024 11:06 PM
Hi!
Here is my notes about HA pair FW`s adding to Panorama.
Follow these steps it will be work.
Adding HA Fw`s to Panorama.
- Connect firewalls to the Panorama:
Panorama:
a. Panorama -> Managed Devices -> Summary -> Add
Enter device S/N. Enable Associate Devices checkbox. Generate Auth Key and copy it.
b. Commit to Panorama.
Firewall:
a. Device -> Setup -> Panorama Settings
Write the IP addresses of the Panorama SRVs. Paste created before Auth Key.
b. Commit.
- Check connected device status in Panorama:
Panorama -> Managed Devices -> Summary (the status should be connected)
- Disable config sync in firewalls:
Device -> HA -> General -> Setup
Commit
- Import firewall config to Panorama:
Panorama -> Setup -> Operations -> Import device configuration to Panorama
(The same steps for both firewalls)
Commit to Panorama
- Leave just 1 Template Stack for HA devices:
Panorama -> Templates - Remove HA config from each template:
Device -> HA -> Template -> Remove all
(The same steps for both firwalls)
Commit to Panorama - Export or push device config bundle:
Panorama -> Setup -> Operations -> Export or push device config bundle
(The same steps for both firewalls)
Commit -> Push to device - Leave just 1 Device Group for HA devices:
Panorama -> Managed Devices -> Summary
Commit and Push - Enable config sync on firewalls:
Device -> HA -> General -> Setup
Commit
- Plan the transition to Panorama Mgmt
- Disable config sync
- Add HA Firewalls to Panorama
- Verify that the device state for each firewall is connected
- Import each Firewall config into Panorama
- Add the HA firewall pair into the same device group and template stack
- Push the device group and template stack configuration changes to your managed firewalls
- Enable config sync
-----------------------------------------------
Migrate a Firewall HA Pair to Panorama Management and Reuse Existing Configuration
- Disable configuration synchronization between the HA peers on each peer.
- Add HA firewalls to Panorama mgmt.:
a. Create a device registration auth key
Panorama -> Device Registration Auth Key and Add a new auth key
Copy Auth key and close.
b. Add firewalls to a Panorama mgmt. server.
Select Panorama -> Managed Devices -> Summary and Add a new firewall.
Enter the firewall SN
(No Need) Select Associate Devices to associate the fw with a device group.
Enter the device registration auth key created before.
Click ok.
c. (No Need) Associate firewall with a device group.
DISABLE Auto Push on 1st connect
Click OK to add device.
d. Configura the fw to communicate with Panorama.
Login to the fw.
Configure the Panorama setings.
Device -> Setup -> Management and edi Panorama settings.
Enter primary and secondary Panorama addresses and Auth key.
Click OK and commit your changes.
e. Auth using custom cert???
f. Commit to Panorama and commit your changes.
g. Verify that the firewalls is connected to Panorama.
Panorama -> Managed Devices -> Summary.
Device state should be shown as “Connected”. - Import each firewall config into Panorama.
a. Panorama -> Setup -> Operations and click Import device configuration to Panorama and select the device.
b. Edit template name.
c. Commit to Panorama.
d. Panorama -> Setup -> Operations and Export or push device config bundle. Select the device, select ok and Push & Commit the configuration.
e. Launch the Web Interface of the firewall HA peer and ensure that the configuration pushed in the previous step committed successfully. If not, Commit the changes locally on the firewall.
f. Repeat Step 1-6 above on the second firewall. The process creates a device group and template stack per each firewall.
Rashadat Seyidzada
Azerbaijan, Baku
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-28-2024 11:27 PM
Hi! I hope these steps will help you.
Notes from my configurations.
ADDING HA FW`s to Panorama
- Connect firewalls to the Panorama:
Panorama:
a. Panorama -> Managed Devices -> Summary -> Add
Enter device S/N. Enable Associate Devices checkbox. Generate Auth Key and copy it.
b. Commit to Panorama.
Firewall:
a. Device -> Setup -> Panorama Settings
Write the IP addresses of the Panorama SRVs. Paste created before Auth Key.
b. Commit.
- Check connected device status in Panorama:
Panorama -> Managed Devices -> Summary (the status should be connected)
- Disable config sync in firewalls:
Device -> HA -> General -> Setup
Commit
- Import firewall config to Panorama:
Panorama -> Setup -> Operations -> Import device configuration to Panorama
(The same steps for both firewalls)
Commit to Panorama
- Leave just 1 Template Stack for HA devices:
Panorama -> Templates - Remove HA config from each template:
Device -> HA -> Template -> Remove all
(The same steps for both firwalls)
Commit to Panorama - Export or push device config bundle:
Panorama -> Setup -> Operations -> Export or push device config bundle
(The same steps for both firewalls)
Commit -> Push to device - Leave just 1 Device Group for HA devices:
Panorama -> Managed Devices -> Summary
Commit and Push - Enable config sync on firewalls:
Device -> HA -> General -> Setup
Commit
- Plan the transition to Panorama Mgmt
- Disable config sync
- Add HA Firewalls to Panorama
- Verify that the device state for each firewall is connected
- Import each Firewall config into Panorama
- Add the HA firewall pair into the same device group and template stack
- Push the device group and template stack configuration changes to your managed firewalls
- Enable config sync
Migrate a Firewall HA Pair to Panorama Management and Reuse Existing Configuration
- Disable configuration synchronization between the HA peers on each peer.
- Add HA firewalls to Panorama mgmt.:
a. Create a device registration auth key
Panorama -> Device Registration Auth Key and Add a new auth key
Copy Auth key and close.
b. Add firewalls to a Panorama mgmt. server.
Select Panorama -> Managed Devices -> Summary and Add a new firewall.
Enter the firewall SN
(No Need) Select Associate Devices to associate the fw with a device group.
Enter the device registration auth key created before.
Click ok.
c. (No Need) Associate firewall with a device group.
DISABLE Auto Push on 1st connect
Click OK to add device.
d. Configura the fw to communicate with Panorama.
Login to the fw.
Configure the Panorama setings.
Device -> Setup -> Management and edi Panorama settings.
Enter primary and secondary Panorama addresses and Auth key.
Click OK and commit your changes.
e. Auth using custom cert???
f. Commit to Panorama and commit your changes.
g. Verify that the firewalls is connected to Panorama.
Panorama -> Managed Devices -> Summary.
Device state should be shown as “Connected”. - Import each firewall config into Panorama.
a. Panorama -> Setup -> Operations and click Import device configuration to Panorama and select the device.
b. Edit template name.
c. Commit to Panorama.
d. Panorama -> Setup -> Operations and Export or push device config bundle. Select the device, select ok and Push & Commit the configuration.
e. Launch the Web Interface of the firewall HA peer and ensure that the configuration pushed in the previous step committed successfully. If not, Commit the changes locally on the firewall.
f. Repeat Step 1-6 above on the second firewall. The process creates a device group and template stack per each firewall.
Rashadat Seyidzada
Azerbaijan, Baku
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-29-2024 12:58 AM
Hi.
Follow these steps. I hope will help you.
ADDING HA FW`s to Panorama
- Connect firewalls to the Panorama:
Panorama:
a. Panorama -> Managed Devices -> Summary -> Add
Enter device S/N. Enable Associate Devices checkbox. Generate Auth Key and copy it.
b. Commit to Panorama.
Firewall:
a. Device -> Setup -> Panorama Settings
Write the IP addresses of the Panorama SRVs. Paste created before Auth Key.
b. Commit.
- Check connected device status in Panorama:
Panorama -> Managed Devices -> Summary (the status should be connected)
- Disable config sync in firewalls:
Device -> HA -> General -> Setup
Commit
- Import firewall config to Panorama:
Panorama -> Setup -> Operations -> Import device configuration to Panorama
(The same steps for both firewalls)
Commit to Panorama
- Leave just 1 Template Stack for HA devices:
Panorama -> Templates - Remove HA config from each template:
Device -> HA -> Template -> Remove all
(The same steps for both firwalls)
Commit to Panorama - Export or push device config bundle:
Panorama -> Setup -> Operations -> Export or push device config bundle
(The same steps for both firewalls)
Commit -> Push to device - Leave just 1 Device Group for HA devices:
Panorama -> Managed Devices -> Summary
Commit and Push - Enable config sync on firewalls:
Device -> HA -> General -> Setup
Commit
- Plan the transition to Panorama Mgmt
- Disable config sync
- Add HA Firewalls to Panorama
- Verify that the device state for each firewall is connected
- Import each Firewall config into Panorama
- Add the HA firewall pair into the same device group and template stack
- Push the device group and template stack configuration changes to your managed firewalls
- Enable config sync
Migrate a Firewall HA Pair to Panorama Management and Reuse Existing Configuration
- Disable configuration synchronization between the HA peers on each peer.
- Add HA firewalls to Panorama mgmt.:
a. Create a device registration auth key
Panorama -> Device Registration Auth Key and Add a new auth key
Copy Auth key and close.
b. Add firewalls to a Panorama mgmt. server.
Select Panorama -> Managed Devices -> Summary and Add a new firewall.
Enter the firewall SN
(No Need) Select Associate Devices to associate the fw with a device group.
Enter the device registration auth key created before.
Click ok.
c. (No Need) Associate firewall with a device group.
DISABLE Auto Push on 1st connect
Click OK to add device.
d. Configura the fw to communicate with Panorama.
Login to the fw.
Configure the Panorama setings.
Device -> Setup -> Management and edi Panorama settings.
Enter primary and secondary Panorama addresses and Auth key.
Click OK and commit your changes.
e. Auth using custom cert???
f. Commit to Panorama and commit your changes.
g. Verify that the firewalls is connected to Panorama.
Panorama -> Managed Devices -> Summary.
Device state should be shown as “Connected”. - Import each firewall config into Panorama.
a. Panorama -> Setup -> Operations and click Import device configuration to Panorama and select the device.
b. Edit template name.
c. Commit to Panorama.
d. Panorama -> Setup -> Operations and Export or push device config bundle. Select the device, select ok and Push & Commit the configuration.
e. Launch the Web Interface of the firewall HA peer and ensure that the configuration pushed in the previous step committed successfully. If not, Commit the changes locally on the firewall.
f. Repeat Step 1-6 above on the second firewall. The process creates a device group and template stack per each firewall.
Rashadat Seyidzada
Azerbaijan, Baku
- 4653 Views
- 7 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Azure to OnPrem Connectivity issue in Next-Generation Firewall Discussions
- GRPC status UNAVAILABLE in intelligent offload in VM-Series in the Private Cloud
- Cannot Access Primary in HA Pair – Need Failover & Recovery Advice" in Next-Generation Firewall Discussions
- Delete default "Internet" security zone in SCM in Strata Cloud Manager
- CIE agent not connecting to AD servers in Cloud Identity Engine Discussions