- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
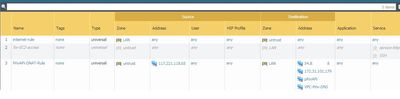
PA firewall traffic to AWS API gateway
- LIVEcommunity
- Discussions
- Network Security
- VM-Series in the Public Cloud
- Re: PA firewall traffic to AWS API gateway
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
PA firewall traffic to AWS API gateway
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-07-2020 06:19 AM
Planning to secure AWS infra using a VM firewall Palo Alto. Main AWS components are API Gateway & Lambda.
Traffic from external network (public) comes to API gateway and to lambda. Is it possible to route incoming traffic via PA firewall to API gateway.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-07-2020 09:26 AM
The way I have solved this in the past is to configured the API Gateway with a private endpoint in the firewall VPC. Configure the the firewall pool behind a Public ALB to serve as you front end with your desired app cert. Use a source and destination NAT rule to forward that traffic through the firewalls to the API GW endpoint FQDN.
One nuance, if you intend to decrypt the traffic on the way through use a SSL Forward Proxy decryption profile rather than the more intuitive Inbound Decrypt profile. The API gateway does not allow you to load a custom cert when using a private endpoint. By flipping the profile, you can get around the SSL handshake errors. The ALB will ignore the self signed cert warning.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-08-2020 02:50 AM
Thank you @jmeurer
I was exploring around the method you said, could not get it done. Could you please help with the steps you followed?
Create Private APi
Private endpoint
......
Finally how was it linked with Palo Alto/Firewall DNAT.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-08-2020 06:15 AM
I used this guide.
https://docs.aws.amazon.com/apigateway/latest/developerguide/apigateway-private-apis.html
When the private endpoint is created, it will have a zone redundant FQDN assigned to it. You use that FDQN as our destination in the NAT rule.
You do also need a source nat on the same rule to ensure the proper return path from the api GW to the firewall. That would typically be your trust side interface address.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-10-2020 08:59 AM
@jmeurer your reply is helping. I tried the following;
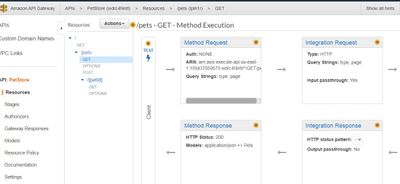
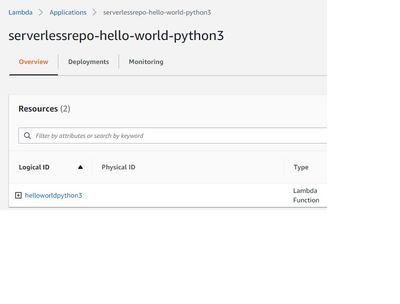
1. Create a sample lambda function of pet store - http://petstore-demo-endpoint.execute-api.com/petstore/pets
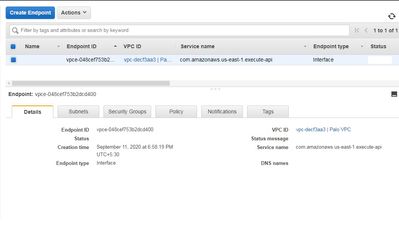
2. Created VPC endpoint
3. Created private REST API and attached endpoint
4. Created DNAT in PA with destination as VPC endpoint
**PA LAN and VPC endpoint are in same subnet
Now I called the URL http://PAWANIP/petstore/pets
Tried diff URLs, patterns, https nothing worked. Is there anything wrong in the method done.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-10-2020 09:29 AM
Did you add a source translation to the NAT rule with the firewall's interface address? Otherwise the endpoint will try to respond directly to the original client IP.
If you spin up a bastion host in the VPC, can you access the end point? It could an SG on the endpoint not allowing the traffic in.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-10-2020 10:38 AM
Thank you @jmeurer
I did create an SNAT from internal to external with external interface IP.
DNAT from PA to an EC2 in AWS is working
I checked SG of API gateway, endpoint, lamda. It's all full allow.
Are the steps I followed correct?
Is the URL I used to call lambda correct?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-10-2020 11:07 AM
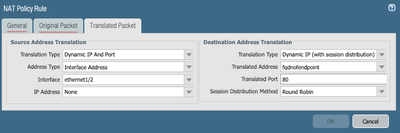
That SNAT flow does not sound correct. The NAT rule that Destination Nats the traffic to Endpoint, should also have source translation set to the internal interface.
Would you mind posting screen shots of the nat rule.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-11-2020 07:02 AM
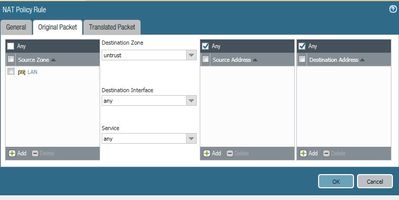
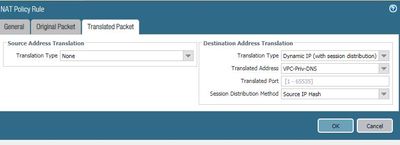
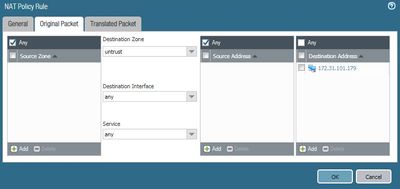
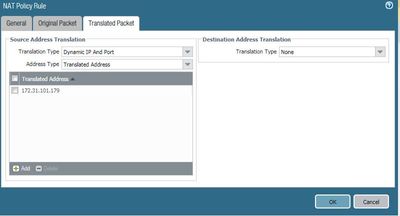
Assuming your IP specified it the Untrust IP and Eth1/2 is your Trust side interface, your NAT rule translated tab should look like this. This indicates that we are sending the traffic on to the API Endpoint and setting the source IP to be the internal interface of the firewall so that they endpoint knows where to respond to.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-16-2020 06:57 AM
Thanks,
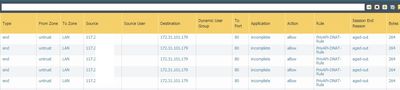
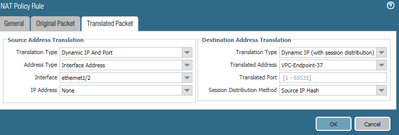
It seems the luck has not turned yet. This is my NAT statement.
i used this doc to create private API and endpoint
https://aws.amazon.com/premiumsupport/knowledge-center/api-gateway-private-cross-account-vpce/
If i try https://PAWANPublicIP/test/ nothing loads
I tried creating new APi with this doc (change i created a private API)
https://docs.aws.amazon.com/apigateway/latest/developerguide/api-gateway-create-api-as-simple-proxy-for-lambda.html
If i try https://PAWANPublicIP/test/helloworld?name=John&city=Seattle nothing loads
No idea why is this happening, still trying the luck
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-16-2020 07:22 AM
Watch your security groups on the endpoint. Also, check the firewall to ensure the Virtual Router has routes to the endpoint subnets. Have you tried deploying a bastion into the Trust side subnet to test the endpoint directly? We need to determine if the issue is the firewall routing or the endpoint itself.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-19-2020 05:42 AM
Thank you @jmeurer
hard word paid off, now am able to load the lamda function result, although it's showing {"message":"Forbidden"}
so happy at-least traffic reaching APiGW.
If you have any idea why forbidden error, please share.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-19-2020 06:13 AM
Good news. Message forbidden could be a result of a iam policy on the gateway. You may need to assign a role to firewall so that it has permission to access the gateway. It could also just be a formatting error in the api call.
if you deployed a bastion host into the firewall subnet, does it have the same response?
- 19144 Views
- 22 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- How does the Azure Virtual Network discovers that there is Palo Alto Gateway Interface in VM-Series in the Public Cloud
- Log forwarding from Cloud NGFW in Azure to Log Analytics Workspace for Sentinel in VM-Series in the Public Cloud
- Not able to log XFF (Actual Client IP) in PaloAlto Logs even when we enable XFF and URL filtering profile in Palo's in Next-Generation Firewall Discussions
- Issue with allowing AnyDesk on a no-internet policy in Next-Generation Firewall Discussions
- Request Advice – BGP Failover Route-Based IPsec VPN With WatchGuard (WG) in Next-Generation Firewall Discussions