- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Palo in AWS to Azure VPN Gateway
- LIVEcommunity
- Discussions
- Network Security
- VM-Series in the Public Cloud
- Re: Palo in AWS to Azure VPN Gateway
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Palo in AWS to Azure VPN Gateway
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-06-2022 03:24 PM - edited 05-06-2022 03:26 PM
Hi All, I am trying to setup a site-to-to site VPN between Palo (v9.0.1) and Azure VPN gateway.
I have a question and an issue that I am trying to resolve...
NAT-T should be enabled in the gateway settings since AWS NATs everything?
This is the error I keep getting...
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-16-2022 01:53 AM
Hi @PaulZharyuk ,
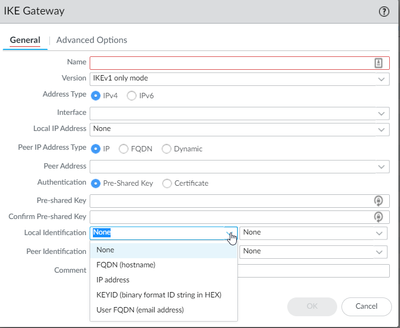
You need to put the private IP addresses as IKE peer ID when defining the IKE Gateway.
If you don't define anything (leave the default of none), firewalls will use IP addresses as peer identifiers. But when behind NAT device will send the private address as local peer (because that is assigned on its interface), while the remote peer will expect to see the public IP (because you have defind the public IP as remote peer).
For that reason when behind NAT, in addition to NAT-T you need to change IKE peer identification to use the private addresses.
P.S. I hope you have upgraded your firewall as 9.0 is out of support since March.
- 3092 Views
- 1 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Palo Alto to Azure vpn tunnel fails at random in Next-Generation Firewall Discussions
- How does the Azure Virtual Network discovers that there is Palo Alto Gateway Interface in VM-Series in the Public Cloud
- PA Global Protect in GlobalProtect Discussions
- Palo Alto VM migration on Azure in VM-Series in the Public Cloud
- Unable to reach Palo Alto - Global Protect Portal. in GlobalProtect Discussions