- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Public IPs with NAT in IPSEC
- LIVEcommunity
- Discussions
- Network Security
- VM-Series in the Public Cloud
- Public IPs with NAT in IPSEC
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Public IPs with NAT in IPSEC
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-03-2021 07:52 AM
I've got a rather bizarre setup that I'm trying to integrate with a new customer using a vm-series 300 in AWS. I have setup and established an IPSEC tunnel (that even comes up when we attempt to send traffic over the tunnel). Where it gets complicated is that their expectation is that we NAT all traffic using public IPs and send the traffic through the tunnel (I should mention that the other side is a Cisco ASA device).
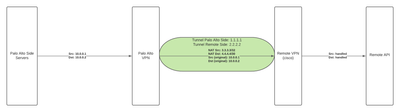
I've attached a fairly simple diagram of the setup that's been proposed by the customer on the other side ( IP addresses changed for safety). To sum it up quickly:
* we have a tunnel established between 1.1.1.1 and 2.2.2.2, this tunnel comes up when I attempt to send traffic through it
* I've routed both 3.3.3.3/32 (our side of the nat translation) and 4.4.4.4/30 (their side of the nat translation) into the tunnel interface
* when i attempt to send traffic through the tunnel over port 443 (ex: curl https://10.0.0.2) from our server the tunnel comes up
* i can also see in the traffic monitor that the NAT policy appears to be applying (I can see the 10.x addresses NAT'd to the 3.3.3.3 and 4.4.4.4) addresses respectively.
The customer is reporting that no traffic is coming through on their side. When I try to use the packet capture tool on our side and filter based on interface (tunnel.1 in this case), then try to send traffic, I don't see any packets. Is there anyway to verify that traffic is indeed flowing over the tunnel?
I could also have done something really wrong here, but I'd expect that if the tunnel comes up, some traffic is attempting to be sent.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-03-2021 10:16 AM - edited 11-03-2021 10:20 AM
Hi @birdperson ,
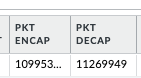
Yes, you can see encaps and decaps from Network > IPSec Tunnels > Tunnel Info next to your VPN.
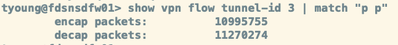
You can also see them on the CLI with the command 'show vpn flow tunnel-id <tunnel-id> | match "p p"'. This doc is an excellent VPN troubleshooting reference -> https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClivCAC.
Thanks,
Tom
- 2890 Views
- 1 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Palo Alto Networks PA- 450 Next‑Generation Firewall to maintain uninterrupted BSNL SIP trunk services in the event of a primary internet link failure. in Next-Generation Firewall Discussions
- GRPC status UNAVAILABLE in intelligent offload in VM-Series in the Private Cloud
- Connectivity with Panorama in VM-Series in the Public Cloud
- Which AWS Instance Type Meets VM-300 Requirements? Documentation Seems Inconsistent in VM-Series in the Public Cloud
- How does the Azure Virtual Network discovers that there is Palo Alto Gateway Interface in VM-Series in the Public Cloud