- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Site to Site VPN IPSec issue between PA and Azure
- LIVEcommunity
- Discussions
- Network Security
- VM-Series in the Public Cloud
- Site to Site VPN IPSec issue between PA and Azure
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-24-2017 07:20 AM
Hello,
I have some problem to configure a VPN between my Palo Alto and Azure.
I follow this tutorial : https://live.paloaltonetworks.com/t5/Configuration-Articles/How-to-Configure-VPN-Tunnel-Between-a-Pa...
So I have this configuration:
Tunnel Interface: It’s an IP in /32 include in the subnet of the Azure gateway (in /29)
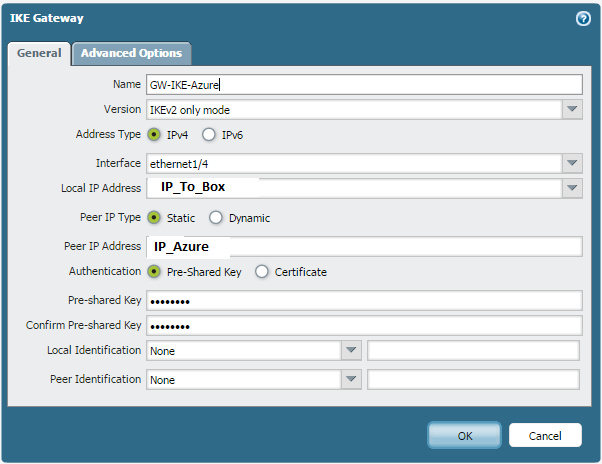
IKE Gateway: My firewall is behind NAT
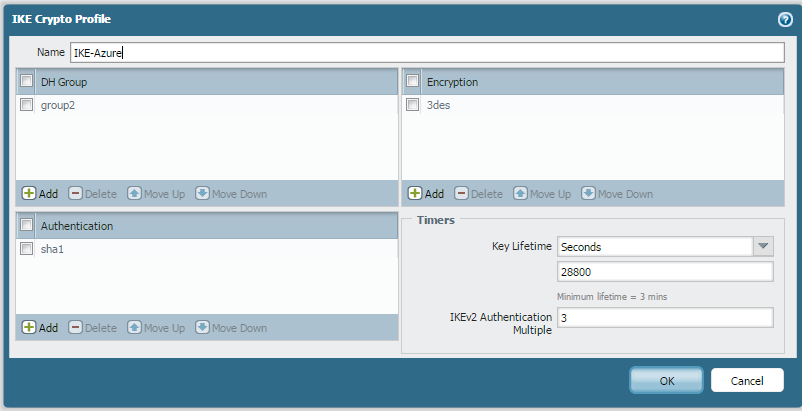
IKE Crypto Profile:
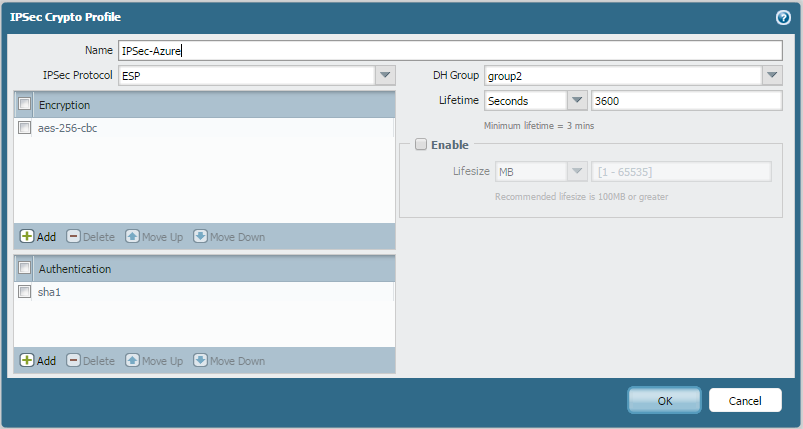
IPsec Crypto Profile:
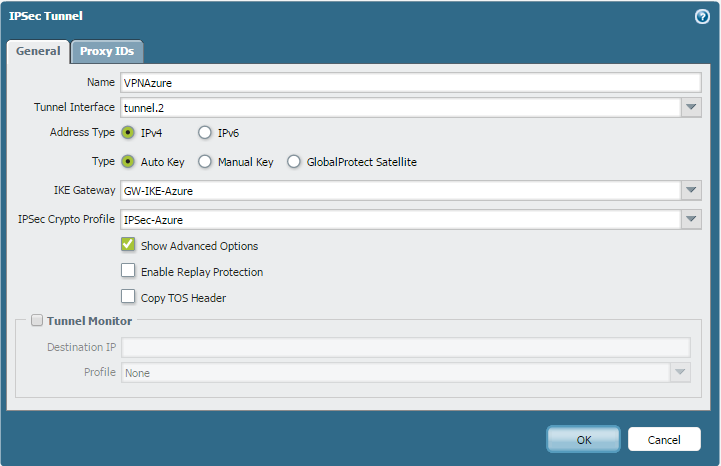
IPsec Tunnel:
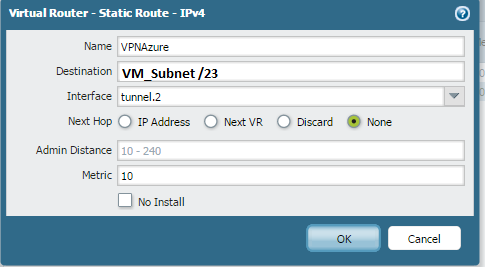
Static Route: Destination address is my server subnet
Status of the IPsec tunnels are red (so Phase 1 and Phase 2 of the negotiation don’t succeed):
To test and send data through the VPN, I try to connect in RDP to a VM in Azure. But my PC can’t access to the server.
The firewall can’t ping the public IP of Azure. With a traceroute, I can see that packets go on Internet.
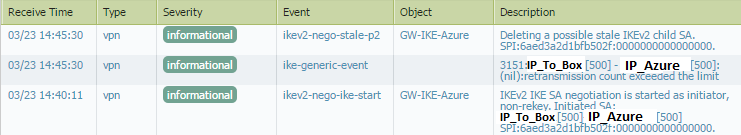
This is system logs from the firewall with “vpn” as a filter:
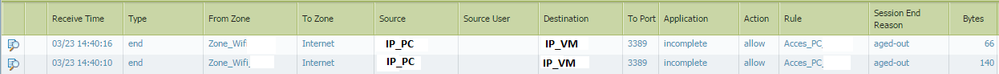
In traffic log, the application is “incomplete” with end session reason “aged-out”:
Results with some commands in the CLI:
show vpn ike-sa gateway GW-IKE-Azure = “IKE gateway GW-IKE-Azure not found”
test vpn ike-sa gateway GW-IKE-Azure = “Initiate IKE SA: Total 1 gateways found. 1 ike sa found”
show session all filter application ike = “No Active Sessions”
debug ike pcap on
view-pcap no-dns-lookup yes no-port-lookup yes debug-pcap ikemgr.pcap =
The Azure configuration is:
The connection is configured as Site-to-Site connection
The address range is in /23 with 2 subnet: one in /24 (for VMs) and the second in /29 (for the subnet gateway).
I have a VM subnet with one server install.
Have you got any idea to solve the problem?
Thank you in advance for your help.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-27-2017 03:01 PM - edited 03-27-2017 03:05 PM
Heys,
Would be nice to see a full log output:
> tail lines 200 mp-log ikemgr.log
It is been some time since my last set-up but just a quick update/tips on this:
- make sure Palo in the "passive" mode. So it will not be able to initiate a VPN but we could not make it working when its disabled.
- IKEv2 initiate 2 tunnels: IKE tunnel ( old name of IKEv1 Phase 1) and CHILD_SA (old name of IKEv1 Phase 2). Default lifetime for IKE Tunnel is 86400 or 28800 seconds (depends of the vendor) for CHILD_SA is 3600 seconds hence your tunnel will be always re-established every hour. But it takes couple seconds not minutes.
- disable no-pfs on IPSec Crypto
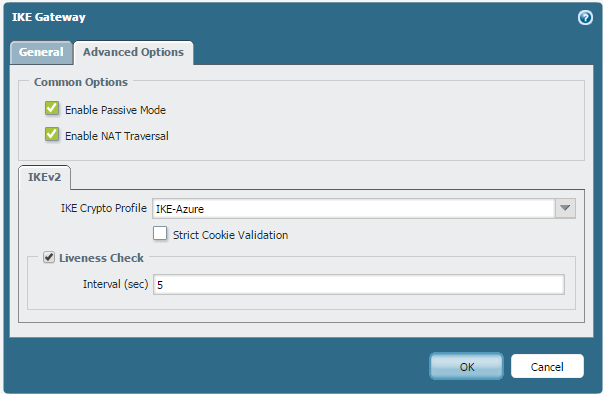
- disable "Liveness Check" on the IKE Gateway configuration.
Make sure that all other setting are compatible with Azure. Please see below:
IPsec Parameters
Although the values listed below are supported by the Azure VPN Gateway, currently there is no way for you to specify or select a specific combination from the Azure VPN Gateway. You must specify any constraints from the on-premises VPN device. In addition, you must clamp MSS at 1350.
IKE Phase 1 setup
| Property | Policy-based | Route-based and Standard or High Performance VPN gateway |
| IKE Version | IKEv1 | IKEv2 |
| Diffie-Hellman Group | Group 2 (1024 bit) | Group 2 (1024 bit) |
| Authentication Method | Pre-Shared Key | Pre-Shared Key |
| Encryption Algorithms | AES256 AES128 3DES | AES256 3DES |
| Hashing Algorithm | SHA1(SHA128) | SHA1(SHA128), SHA2(SHA256) |
| Phase 1 Security Association (SA) Lifetime (Time) | 28,800 seconds | 10,800 seconds |
IKE Phase 2 setup
| Property | Policy-based | Route-based and Standard or High Performance VPN gateway |
| IKE Version | IKEv1 | IKEv2 |
| Hashing Algorithm | SHA1(SHA128) | SHA1(SHA128) |
| Phase 2 Security Association (SA) Lifetime (Time) | 3,600 seconds | 3,600 seconds |
| Phase 2 Security Association (SA) Lifetime (Throughput) | 102,400,000 KB | - |
| IPsec SA Encryption & Authentication Offers (in the order of preference) | 1. ESP-AES256 2. ESP-AES128 3. ESP-3DES 4. N/A | See Route-based Gateway IPsec Security Association (SA) Offers(below) |
| Perfect Forward Secrecy (PFS) | No | Yes (DH Group1, 2, 5, 14, 24) |
| Dead Peer Detection | Not supported | Supported |
After doing all this tunnel still stable for the past 3 days.
You can clear the tunnel couple times to see if everything is working correctly:
> clear vpn ike-sa gateway (for IKE Tunnel)
> clear vpn ipsec-sa tunnel (for CHILD_SA)
Hope it helps!
more info here:
https://live.paloaltonetworks.com/t5/General-Topics/VPN-to-Azure-dropouts/m-p/98936#M44162
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-24-2017 01:55 PM - edited 03-24-2017 01:58 PM
Can you follow this for IKEv2 and let me know if it works:
There doesn't seem to be much difference between the two...you may need to uncheck the liveliness check and the DH group to no-pfs.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-27-2017 12:30 AM
Hello,
Thank you for your answer.
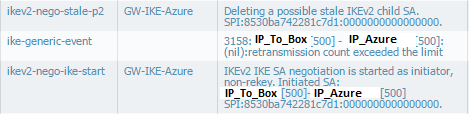
I make modifications, but it doesn't work. I have the same error message in systems logs :
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-27-2017 07:50 AM
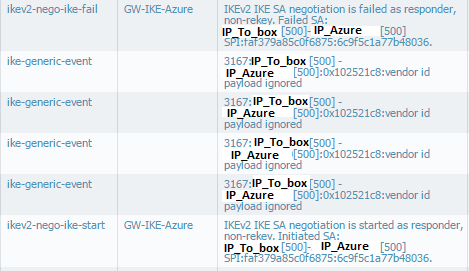
I have just had a new error message:
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-27-2017 03:01 PM - edited 03-27-2017 03:05 PM
Heys,
Would be nice to see a full log output:
> tail lines 200 mp-log ikemgr.log
It is been some time since my last set-up but just a quick update/tips on this:
- make sure Palo in the "passive" mode. So it will not be able to initiate a VPN but we could not make it working when its disabled.
- IKEv2 initiate 2 tunnels: IKE tunnel ( old name of IKEv1 Phase 1) and CHILD_SA (old name of IKEv1 Phase 2). Default lifetime for IKE Tunnel is 86400 or 28800 seconds (depends of the vendor) for CHILD_SA is 3600 seconds hence your tunnel will be always re-established every hour. But it takes couple seconds not minutes.
- disable no-pfs on IPSec Crypto
- disable "Liveness Check" on the IKE Gateway configuration.
Make sure that all other setting are compatible with Azure. Please see below:
IPsec Parameters
Although the values listed below are supported by the Azure VPN Gateway, currently there is no way for you to specify or select a specific combination from the Azure VPN Gateway. You must specify any constraints from the on-premises VPN device. In addition, you must clamp MSS at 1350.
IKE Phase 1 setup
| Property | Policy-based | Route-based and Standard or High Performance VPN gateway |
| IKE Version | IKEv1 | IKEv2 |
| Diffie-Hellman Group | Group 2 (1024 bit) | Group 2 (1024 bit) |
| Authentication Method | Pre-Shared Key | Pre-Shared Key |
| Encryption Algorithms | AES256 AES128 3DES | AES256 3DES |
| Hashing Algorithm | SHA1(SHA128) | SHA1(SHA128), SHA2(SHA256) |
| Phase 1 Security Association (SA) Lifetime (Time) | 28,800 seconds | 10,800 seconds |
IKE Phase 2 setup
| Property | Policy-based | Route-based and Standard or High Performance VPN gateway |
| IKE Version | IKEv1 | IKEv2 |
| Hashing Algorithm | SHA1(SHA128) | SHA1(SHA128) |
| Phase 2 Security Association (SA) Lifetime (Time) | 3,600 seconds | 3,600 seconds |
| Phase 2 Security Association (SA) Lifetime (Throughput) | 102,400,000 KB | - |
| IPsec SA Encryption & Authentication Offers (in the order of preference) | 1. ESP-AES256 2. ESP-AES128 3. ESP-3DES 4. N/A | See Route-based Gateway IPsec Security Association (SA) Offers(below) |
| Perfect Forward Secrecy (PFS) | No | Yes (DH Group1, 2, 5, 14, 24) |
| Dead Peer Detection | Not supported | Supported |
After doing all this tunnel still stable for the past 3 days.
You can clear the tunnel couple times to see if everything is working correctly:
> clear vpn ike-sa gateway (for IKE Tunnel)
> clear vpn ipsec-sa tunnel (for CHILD_SA)
Hope it helps!
more info here:
https://live.paloaltonetworks.com/t5/General-Topics/VPN-to-Azure-dropouts/m-p/98936#M44162
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-02-2017 07:35 AM
Hi all,
I need your help to configure a vpn between PA3020 and Azure with dynamic gateway.
I have a problem "ike-nego-p1-fail " --> ( description contains 'IKE phase-1 negotiation is failed as initiator, main mode. Failed SA: X.X.X.X[500]-X.X.X.X[500] cookie:6a4facbf0c032fc8:0000000000000000. Due to timeout.' )
and ( eventid eq ike-nego-p1-delete ) --> and and ( description contains 'IKE phase-1 SA is deleted SA: SA: X.X.X.X[500]-X.X.X.X[500] cookie:6a4facbf0c032fc8:0000000000000000.' )
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-02-2017 02:57 PM
Hi,
My guess is that you need an alternative authentication method in the IKE gateway setup: Local Identification portion.
You can use email or fqdn and as long as they match on both sides it doesn't matter what it is...
The guess is here that NAT is breaking IKE
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-11-2017 06:14 AM
Make sure you have Layer 3 communication between the peer. Before setting up the tunnel, please ping the remote peer ip. If Layer 3 is good, make sure your policy is allowing ike, IPSec etc application on the untrust interface (zone).
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2017 04:40 PM
Hi, I got question regarding 96415 fixed in 7.1.6. However, I am still seeing the issue in 7.1.6.
What should I do, should I upgrade to 8.0.0+Please assist. Thank you.
96415
Fixed an issue where the firewall failed to pass traffic in strongSwan and Azure IPSec tunnels while using IKEv2 because it did not send a Delete payload during a Phase 2 Child SA re-keying. With this fix, the firewall correctly sends a Delete payload during re-keying if it is the node that initiated the re-keying.
- 1 accepted solution
- 35801 Views
- 8 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Palo Alto to Azure vpn tunnel fails at random in Next-Generation Firewall Discussions
- "More runtime stats" not loading when Advanced routing is enabled in Next-Generation Firewall Discussions
- Important Notice: Downgrade of Firewalls with Expired AIOps Premium Licenses in AIOps for NGFW Discussions
- GloablProtect + Explicit Proxy blocks WSL traffic. in GlobalProtect Discussions
- Palo Alto Unable to Download Software Updates in Next-Generation Firewall Discussions