- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
- LIVEcommunity
- Discussions
- Network Security
- VM-Series in the Public Cloud
- Who Me Too'd this topic
Who Me Too'd this topic
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-24-2017 07:20 AM
Hello,
I have some problem to configure a VPN between my Palo Alto and Azure.
I follow this tutorial : https://live.paloaltonetworks.com/t5/Configuration-Articles/How-to-Configure-VPN-Tunnel-Between-a-Pa...
So I have this configuration:
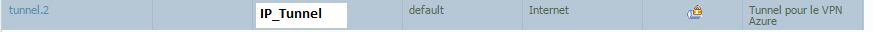
Tunnel Interface: It’s an IP in /32 include in the subnet of the Azure gateway (in /29)
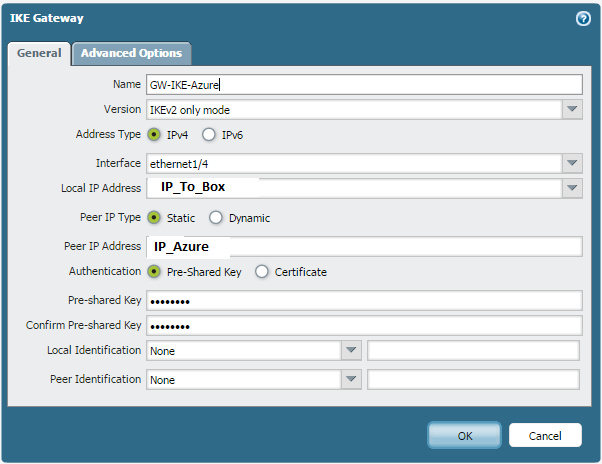
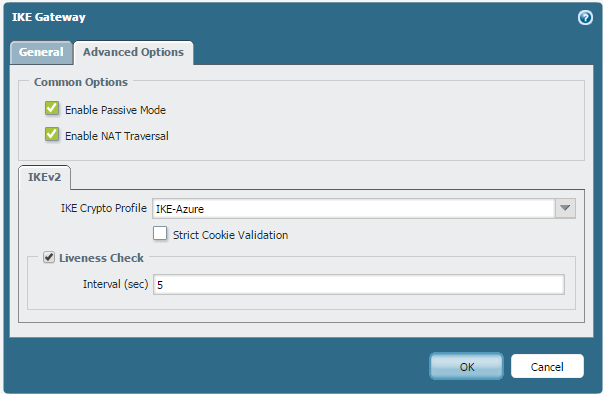
IKE Gateway: My firewall is behind NAT
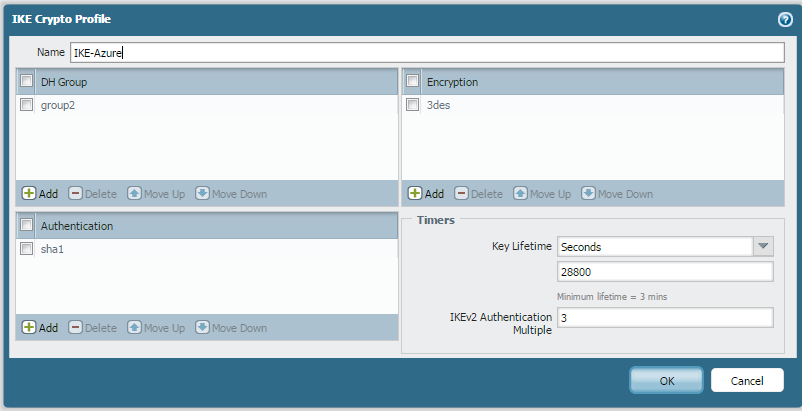
IKE Crypto Profile:
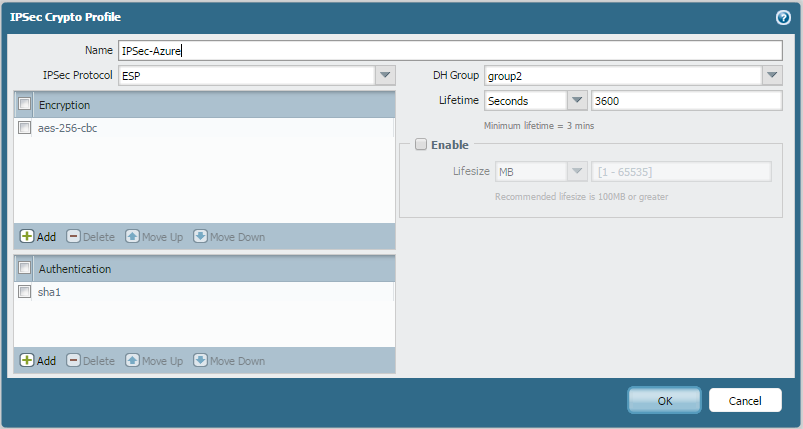
IPsec Crypto Profile:
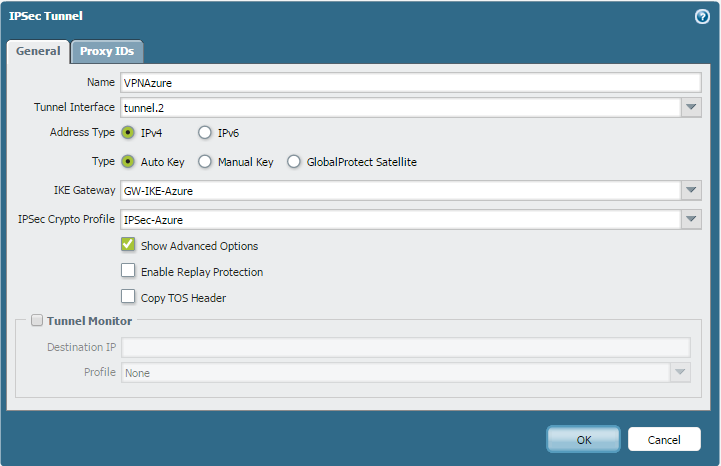
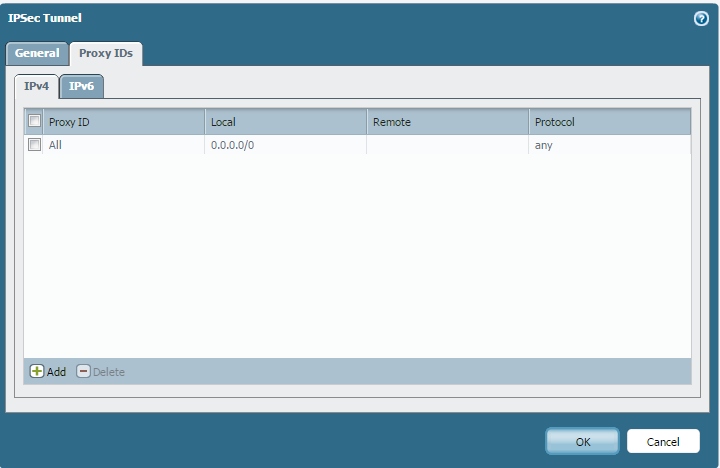
IPsec Tunnel:
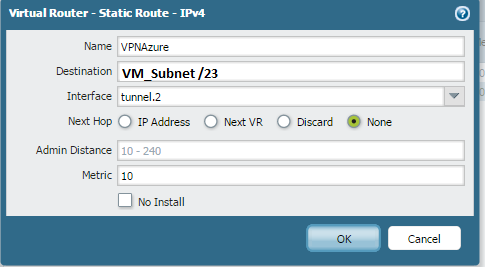
Static Route: Destination address is my server subnet
Status of the IPsec tunnels are red (so Phase 1 and Phase 2 of the negotiation don’t succeed):
To test and send data through the VPN, I try to connect in RDP to a VM in Azure. But my PC can’t access to the server.
The firewall can’t ping the public IP of Azure. With a traceroute, I can see that packets go on Internet.
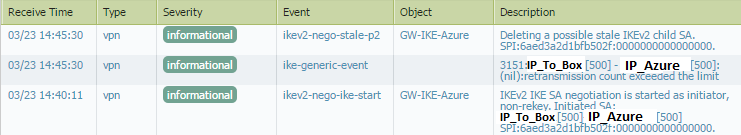
This is system logs from the firewall with “vpn” as a filter:
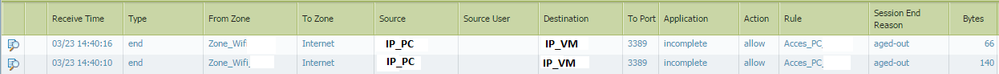
In traffic log, the application is “incomplete” with end session reason “aged-out”:
Results with some commands in the CLI:
show vpn ike-sa gateway GW-IKE-Azure = “IKE gateway GW-IKE-Azure not found”
test vpn ike-sa gateway GW-IKE-Azure = “Initiate IKE SA: Total 1 gateways found. 1 ike sa found”
show session all filter application ike = “No Active Sessions”
debug ike pcap on
view-pcap no-dns-lookup yes no-port-lookup yes debug-pcap ikemgr.pcap =
The Azure configuration is:
The connection is configured as Site-to-Site connection
The address range is in /23 with 2 subnet: one in /24 (for VMs) and the second in /29 (for the subnet gateway).
I have a VM subnet with one server install.
Have you got any idea to solve the problem?
Thank you in advance for your help.