- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
IPSEC VPN implementations
- LIVEcommunity
- Discussions
- General Topics
- IPSEC VPN implementations
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-25-2012 03:22 AM
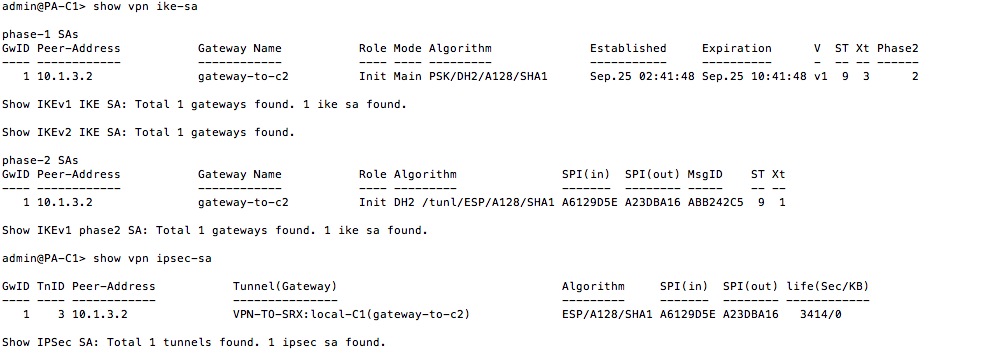
Hi this is one the sample output that i captured when i established a VPN tunnel between 2 PA firewalls.
As far as my knowledge goes Ike SA's are bi directional and IPSEC SA's are uni directional correct me if i am wrong.
But here i see 2 SA's in Phase 1 , but all i establised was only 1 VPN tunnel .
Can some throw some light on this please . Thanks
I have few other questions like :
1. Can we implement policy based VPN's in Palo Alto or everything is Route based ?
2. Do we mandatorily need to specify proxy id even though both sides i am running route based vpn and both side PA firewalls?
3. IKE SA's are bidirectional and IPSEC SA are unidirectional , but i see 2 IKE SA for the same VPN tunnel.
4. Can we implement HUB and Spoke VPN's on PA firewalls , the reason why i ask this i assume we have to assign an ip address for the tunnel interface and configure as multi point in case of juniper i could not see such option here on PA firewall.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-25-2012 03:51 AM
Hi Srikanth,
To answer your questions above:-
1. Palo Alto firewall is a route based VPN firewall.
2. It is not mandatory to use proxy ids when establishing the tunnel between two PA devices.
3. The two 2 IKE SA that you see the for the VPN tunnel are ike phase 1 and ike phase 2 negotiation process after which the tunnel is established.
4. Configuring Hub and spoke route based VPN:- https://live.paloaltonetworks.com/docs/DOC-1608
Did I answer your questions?
Regards
Parth
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-25-2012 03:45 AM
Hi Srikanth,
I am attaching the vpn output from the old thread thread .
When you execute a command, >show vpn ike-sa , it shows the negotiation process of phase 1 and phase 2 both
Check to see phase-1 SA's and phase-2 SA's.
In phase-1 SA you will see the ike crypto algorithms that you had set under Network > Network Profiles> Ike Crypto
In phase-2 SA you will see the ipsec crypto algorithms that you had set under Network > Network Profiles> Ipsec Crypto
>show vpn ipsec-sa , will show you the tunnel that has been set up between the two peers along with the tunnel name and algorithms it negotiated with the peer once the phase 1 and phase 2 negotiations complete.
Here is the link to the document on how to trouble shoot vpn connectivity issues.
https://live.paloaltonetworks.com/docs/DOC-3671
Let me know if this helps.
Regards
Parth
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-25-2012 03:51 AM
Hi Srikanth,
To answer your questions above:-
1. Palo Alto firewall is a route based VPN firewall.
2. It is not mandatory to use proxy ids when establishing the tunnel between two PA devices.
3. The two 2 IKE SA that you see the for the VPN tunnel are ike phase 1 and ike phase 2 negotiation process after which the tunnel is established.
4. Configuring Hub and spoke route based VPN:- https://live.paloaltonetworks.com/docs/DOC-1608
Did I answer your questions?
Regards
Parth
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-25-2012 12:35 PM
1. Cant one combine PBF (policy based forwarding) with a route-based vpn tunnel as nexthop?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-27-2012 02:16 AM
Traffic sourcing from a particular zone in the pbf policy can be forced to egress out the tunnel interface.
Monitoring traffic is sourced from the forwarding egress interface defined in the PBF policy
Regards
Parth
- 1 accepted solution
- 3976 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Connectivity with Panorama in VM-Series in the Public Cloud
- Performance impact of using higher DH group for site-to-site VPNs in Next-Generation Firewall Discussions
- GlobalProtect VPN Client windows 11 crash in GlobalProtect Discussions
- Request Advice – BGP Failover Route-Based IPsec VPN With WatchGuard (WG) in Next-Generation Firewall Discussions
- How to monitor IPSEC tunnels of PRISMA? in Prisma SD-WAN Discussions



