- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Using XML API to query policy post rules
- LIVEcommunity
- Community Legacy Content
- Automation / API
- Automation/API Discussions
- Using XML API to query policy post rules
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-14-2021 08:46 AM - edited 07-15-2021 07:58 AM
Trying to find the correct syntax for querying Panorama for policy post rules by matching IP address (source or destination IP) using the PanOS XML API.
I have looked at:
- our XML API Browser page (i.e. https://<mypanoramahostname>/api),
- the online docs (https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-panorama-api/),
- A documented Postman collection(https://documenter.getpostman.com/view/2937330/7LgDQwG), and
- this LIVEcommunity site.
Still not finding what I am looking for. Is it me, or is API not sufficiently well documented? Can anyone point me to where I can find documentation for each PanOS XML API endpoint, preferably with syntax examples for all possible endpoint parameters?
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-23-2021 02:07 AM
Hi @julio.toledo, the API structure for this feature will match what you see in the GUI, where there are indeed mandatory fields (the red boxes) like destination ports, and protocol is a drop-down between TCP/UDP/ICMP:
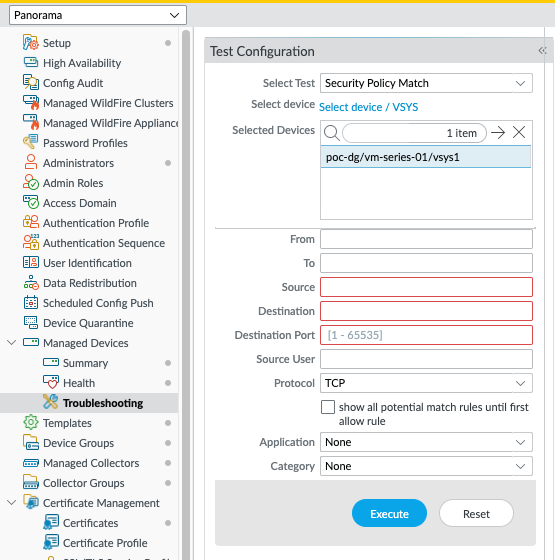
I think this feature is designed to give people a way to test if specific traffic will theoretically pass through the firewall, rather than the very broad and almost audit-type requirement which you have. If you talk with your allocated Systems Engineer or reseller (if you're unsure who they are, send me a direct message on here and I will assist) then they will be able to discuss your requirements and potentially raise a feature request.
Other options to fulfil your requirements would involve an approach of systematically checking the live configurations of your firewall estate, by exporting the Panorama running config and walking through the XML data in your programming language of choice.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-19-2021 10:13 AM
Hi @julio.toledo, I believe you're trying to use the "test policy match" feature via API? If so, I did something similar a couple of weeks ago. I did NAT rules, but you could easily change the API call below to use security rules instead.
https://{{panorama-host}}/api?key={{key}}&type=op&cmd=<request-batch><op-command><device><entry name="{{fw1-serial}}"><vsys><list><member>vsys1</member></list></vsys></entry><entry name="{{fw2-serial}}"><vsys><list><member>vsys1</member></list></vsys></entry></device><test><nat-policy-match><from>Management</from><to>External</to><source>172.31.10.50</source><destination>8.8.8.8</destination><destination-port>443</destination-port><protocol>6</protocol></nat-policy-match></test></op-command></request-batch>
I find the easiest way to find API calls is to debug the GUI, or debug the CLI.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-19-2021 11:28 AM - edited 07-19-2021 11:31 AM
Thanks @JimmyHolland. Yes, I am trying to query security rules via API, either aggregate rules from all devices or from a particular device. However I am not a network or firewall engineer, so things like PanOS CLI commands and Panorama schema (objects, properties, etc.) are new to me.
I find it hard to understand that there is no online reference to the Panorama schema and how it maps to either CLI commands and/or API requests. Reverse engineering it by debugging the GUI or the CLI seems rather backwards, don't you agree?
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-19-2021 12:44 PM
Hi @julio.toledo, I understand learning the PAN-OS schema must be a challenge if you are new to PAN-OS and firewalls/network-security/networking. There is no exhaustive list of XML API endpoints to the full extent, which is why the debug approach usually works best, especially as the CLI/GUI are themselves clients of the XML API. The newer REST API is improving this situation, however, and continues to gain coverage with each release of PAN-OS, so that's something to keep an eye on.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-22-2021 09:23 AM
Thanks @JimmyHolland I figured out how to structure a 'security-policy-match', however it's requiring arguments that make the query far too specific/narrow. It seems that both 'protocol' and 'destination-port' are required, and neither one allows 'any' or '*' or even a range of values (integers only).
Is there a way to match policies across:
- all PAN-OS devices (without having to explicitly enumerate them)
- all destination-ports (i.e. "any")
- all IP protocols ( i.e. "any", or at least {6,17} ).
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-23-2021 02:07 AM
Hi @julio.toledo, the API structure for this feature will match what you see in the GUI, where there are indeed mandatory fields (the red boxes) like destination ports, and protocol is a drop-down between TCP/UDP/ICMP:

I think this feature is designed to give people a way to test if specific traffic will theoretically pass through the firewall, rather than the very broad and almost audit-type requirement which you have. If you talk with your allocated Systems Engineer or reseller (if you're unsure who they are, send me a direct message on here and I will assist) then they will be able to discuss your requirements and potentially raise a feature request.
Other options to fulfil your requirements would involve an approach of systematically checking the live configurations of your firewall estate, by exporting the Panorama running config and walking through the XML data in your programming language of choice.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-23-2021 08:49 AM
Ding, ding, ding! We have a winner. So what I am looking to accomplish is audit/research level work.
On a competitor's product (which shall remain nameless) I am able to issue the following simple, single-line CLI command (on a device-by-device basis) and get back an exhaustive std output of every member rule matching the IP that I'm searching for --either as source or as destination:
show access-list | include {{ lookupIP }}This is exactly the kind of functionality that I'm looking for from Panorama/PAN-OS.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-03-2021 02:30 AM
Thanks for confirming @julio.toledo. Per DM, we've connected you with your SE in order to discuss this topic in more detail.
- 1 accepted solution
- 97444 Views
- 7 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Bootstrapping in AWS using Terraform - question on content files in Automation/API Discussions
- With XML API, How does "Require audit comment on policies" check work? ( Panorama -> Management tab) in Automation/API Discussions
- XML API: Panorama: How to Create/Get/Update the field "Audit Comment" of a Security Policy rule? in Automation/API Discussions
- Moving BGP policy rules in Automation/API Discussions
- Get a full list of security rules with IPS Profiles in Automation/API Discussions



