
- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Palo Alto Networks unveils our new IoT Security Solution that can help keep your network secure as you implement safer cybersecurity measures across your entire platform. Read the IoT overview and find answers on LIVEcommunity.
As technology advances, so do cyberattacks. And the latest targets that seem to be the most unprotected are IoT devices—everything from security cameras to smart appliances. Palo Alto Networks has been able to keep up with the changing times while helping to secure our digital way of life more by protecting all of the IoT devices on your networks.
Again, the IoT Security subscription is supported on PAN-OS 8.1+. Additionally, PAN-OS 10.0 provides automated enforcement using new Device-ID capability.
 |
 |
 |
 |
 |
|---|---|---|---|---|
| 1. Understand IoT Assets | 2. Assess Risk | 3 Apply Risk Reduction Policies | 4. Prevent Known Threats | 5. Detect & Respond to Unknown Threats |
|
Combining Machine Learning with Palo Alto Networks App-ID to provide the deepest IoT visibility and normal behaviors |
Learn device vulnerabilities, risk level, and risky behaviors |
Automated policy recommendations that allow trusted behavior |
Actively detects and prevents known IoT attacks with Machine Learning and Threat Intelligence from Palo Alto Networks subscriptions |
Continuously detects and responds to zero-day attacks using threat modeling, anomaly detection, and crowdsourcing |
|
On IoT SaaS App |
On IoT SaaS App |
Both IoT SaaS App and |
On Next-Generation Firewall |
On IoT SaaS App |
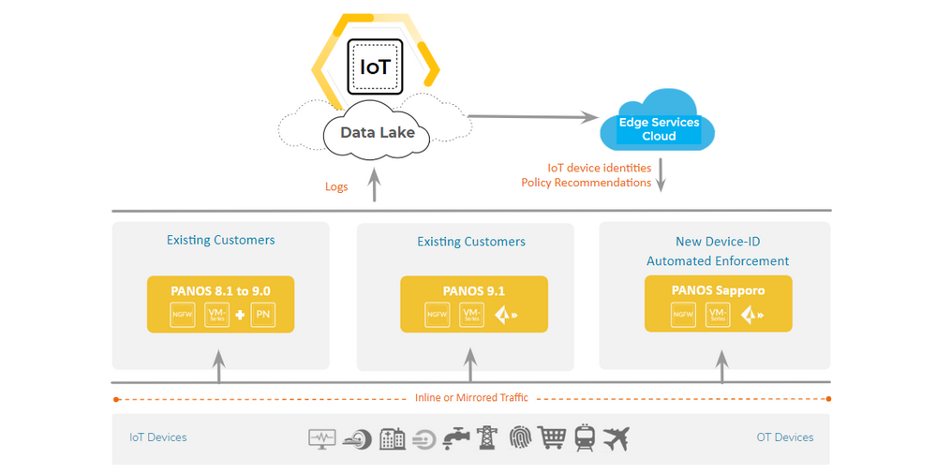
Deployment Considerations, Next-Generation Firewall placement and collecting the right metadata (EALs and session logs), and DHCP
Please see the following video that walks you through Onboarding IoT Security




For the IoT Security resource list, please see the following Knowledge Base article:
IoT Security Resource List On Configuring And Troubleshooting
Keep coming back, we will have more information on IoT available in July.
Thanks for taking time to read my blog.
If you enjoyed this, please hit the Like (thumbs up) button, don't forget to subscribe to the LIVEcommunity Blog.
As always, we welcome all comments and feedback in the comments section below.
Stay Secure,
Joe Delio
End of line
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
| Subject | Likes |
|---|---|
| 2 Likes | |
| 1 Like | |
| 1 Like | |
| 1 Like | |
| 1 Like |
| User | Likes Count |
|---|---|
| 3 | |
| 2 | |
| 1 | |
| 1 | |
| 1 |




