- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
High Alert wininfo.exe
- LIVEcommunity
- Discussions
- Security Operations
- Cortex XDR Discussions
- Re: High Alert wininfo.exe
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
High Alert wininfo.exe
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-17-2021 01:11 AM
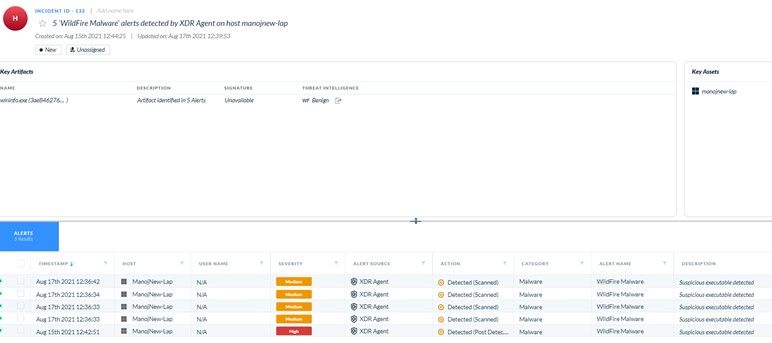
received alert from Traps regarding malware detection of the maximum system due to file “Wininfo.exe”.
Please find a snapshot of one system and suggest how to fix this. Is there any impact?
|
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-19-2021 02:59 AM
No, Still it's receiving a high number of alerts.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-19-2021 08:48 AM
Hi @Mohammed_Yasin, there are several variables to unpack in this scenario. I suggest to investigate if any changes were recently made to the endpoint's assigned malware profile (E.g. Portable Executable and DLL examination - action mode) or the WildFire verdict (E.g. Malware to Benign). The"Detected (Post Detected)" alert action indicates the verdict for the process bas been changed, and the process was executed in the past but still running. It also appears the process is not signed, which may be one of reason for the initial alert.
In terms of impact, we want to ensure that we are investigating the alert/agent holistically, and the investigation of the impact will be more effective with Support. I recommend to create a support case, if you have not already raised one, so we can have our engineering investigate this issue holistically. You may leverage either one of the following two workflows to retrieve support logs from the endpoint: retrieve support logs from an endpoint via the XDR Action Center, or you can right-click on the endpoint from the Endpoint Administration page, and navigate to the Endpoint Control field in order to retrieve the support file. The status of the file retrieval action will be in the Action Center in both workflows. I hope this information provides you with a path forward.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-19-2021 10:14 AM
@Mohammed_Yasin have a client that generated a lot of Alerts for this file last week during the regular scheduled Malware scans.
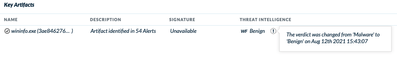
I take it you have Lenovo Laptops? It would appear for a bit of time, last week, Wildfire Global Verdict had it listed as Malicious, but that verdict was short time later changed to Benign as it was reflected in Cortex Hub Console
I had reviewed other OSINT and found this indicative that this indeed should be benign. https://www.virustotal.com/gui/file/3ae8462769a4d5012b66af226a196bb12571c72a231b66f07afcc838e878045c...
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-25-2021 01:33 PM
Hi Mohammed, I had this same alert. It was part of the Lenovo update software. We started getting blasted with alerts, ending up with over 700 alerts. I opened a case and our result was: "On August 12th the Research team changed that verdict twice keeping it finally as Benign.
Based on the last data that you provided, those alerts were Post Detected, meaning that since there was a verdict flip, all endpoints containing that hash will trigger an alert."
This is a benign file. We created an exception and an exclusion to allow the process and stop the alerting. Adding the hash did not stop the alerting. I hope that helps!
- 6050 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Cortex Pop-ups Triggered for StoreDesktopExtension.exe Despite Being Blocklisted in Cortex XSIAM Discussions
- How to Configure XQL to detect logs not reporting rule in Cortex XSIAM Discussions
- Playbook Task - Filters and Transformers help needed in Cortex XSOAR Discussions
- Limitations Observed with XQL Custom Widgets and Issue Visibility in Cortex XDR Discussions
- Playbook to enrich dataset data into alert context in Cortex XDR Discussions