- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Evaluation 8.x Configuration Guide Baseline Prevention Mode
- LIVEcommunity
- Articles
- General Articles
- Evaluation 8.x Configuration Guide Baseline Prevention Mode
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
on 09-13-2019 04:04 AM - edited on 06-03-2025 03:27 AM by kiwi
The purpose of this document is to guide the user through all the steps required to configure a Palo Alto Networks unit for POC testing. There are three installation scenarios for you to choose from TAP, Vwire, or Layer 3.
The configuration is designed to produce maximum logging, using real traffic that is either mirrored or seen over from your production network. The recommended TAP installation will in turn produce the most comprehensive Security Lifecycle Review (SLR) reports possible with maximum visibility.
NOTE: If your evaluation unit came directly from a partner/reseller, distributor, or Palo Alto Networks some of these configurations might already pre-configured. Typically, units shipped from partners are already licensed and registered to the partner who sent it. Below are links to information that will help you decide on the best evaluation for you.
Overview:
TAP - Tap Mode Deployments
Vwire - Virtual Wire Deployments
Layer 3 - Layer 3 Interfaces
- 1. Create Support Portal User Account
- 2. Activate Evaluation Device
- 3. Establish Management IP
- 4. Tap Mode Evaluation Setup (Recommended)
- a. DEVICE Tab configuration
- b. NETWORK Tab configuration (For Vwire mode, jump to page 29)
- 5. Basic Security Policy (firewall rule) Setup
- 6. Security Profiles Setup: Baseline Prevention Config
- 7. User-ID Setup
- a. Setup and connect to your LDAP Server
- b. Group Mapping Setup
- c. Agentless User-ID Setup
- 8. TAP Mode Evaluation Final Check
- 9. Vwire Evaluation Setup
- 10. Vwire Basic Security Policy (firewall rule) Setup
- 11. Layer 3 Evaluation Setup
1. Create Support Portal User Account
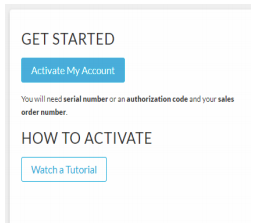
Go to https://support.paloaltonetworks.com
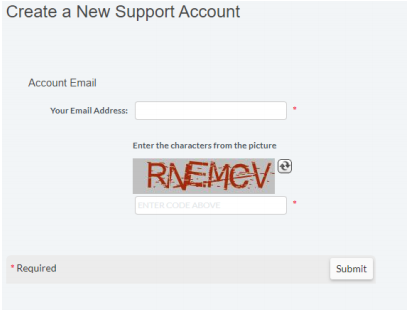
- Click Activate My Account.
- Enter your email address and the CAPTCHA code.
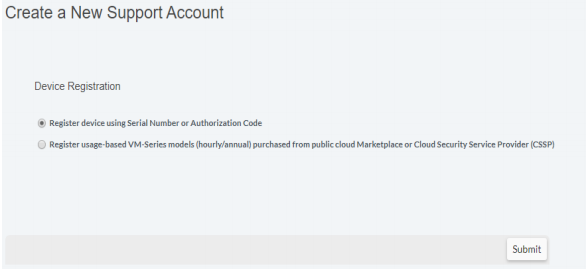
- Select Register device using Serial Number or Authorization Code.
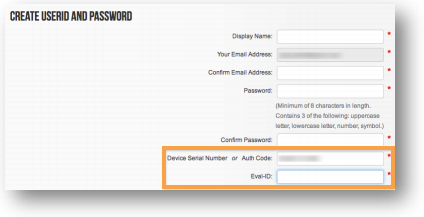
- Complete the New User Registration form.
- The Display Name must be unique. Your display name is used to uniquely identify yourself in the Palo Alto Networks Support Community. It is searchable and viewable by public search engines. For your privacy, please do not use your email address or full name as the display name.
- Enter the Device Serial Number and Eval-ID. This data can be found in your Eval email. When you enter the Device Serial Number (a long string of digits usually starting with 00) and click <Tab> the next field will change and ask for your Eval-ID. The Eval-ID will be in the format EXXXX with numbers following it, no spaces.
The End User Agreement must be accepted to create a user account.
You will receive an email that contains a link to activate your user account. Click on the activation link, log in to the Customer Support Portal (https://support.paloaltonetworks.com). Setup the two security questions, and you will be taken to the Account Home tab.
2. Activate Evaluation Device
If you are evaluating our physical appliance, use step 3.1.
- Go to Assets and select Devices.
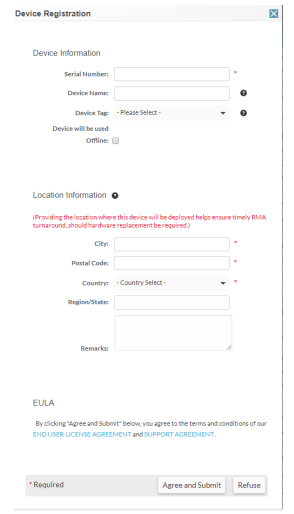
- Select Register New Device and choose Register Device using Serial Number or Authorization Code on the next window then submit.
- Enter the Serial Number and the other required fields. Click Agree and Submit when you're done.
The device is now registered, and you should see a confirmation on this page.
3. Establish Management IP
Connect a serial cable to the CONSOLE port on the firewall, using 9600-8-N-1 on a console emulator, such as Putty. Set Putty for Serial. This will likely require you to use a USB to serial adapter to convert the 9-pin serial to USB, as the firewall ships with a 9-pin to RJ45 console cable. Determine an open IP address on the network that the firewall management interface can use and ensure this IP has access to the Internet using https and is accessible from your desktop.
On new hardware models (PA-220, PA-820, or PA-850), you may use the built-in micro-USB port to console in. Download and install the Microchip driver for Windows. (Not required for Windows 10.) Additional information on the micro USB console port found here.
NOTE: As an alternate approach to using the console port, you can plug a laptop into the MGT port, put a 192.168.1.x IP on their Ethernet NIC and browse to https://192.168.1.1 to login and change the IP in the GUI. Once this change is committed, you will lose your connection to the console (assuming you assigned it outside of that network). Then simply revert to your previous IP, and login to the newly set IP.
Log in using the defaults:
- Username: admin
- Password: admin
From the console, execute the following commands:
> configure (brings you into EDIT mode) # set deviceconfig system ip-address x.x.x.x netmask x.x.x.x # set deviceconfig system dns-setting servers primary x.x.x.x default-gateway x.x.x.x # commit # exit (brings you out of EDIT mode)
You should see the commit process occur and return to a prompt. If you get any formatting errors that keep you from setting the DNS, configure the IP and netmask. DNS can be configured later inside the web interface.
- Connect an ethernet cable from MGT port to switch, so the MGT IP you just set can be browsed and has Internet access.
- Attempt to browse to the IP you just set, using https (https://x.x.x.x)
- Accept the certificate error and log in to the web interface using default admin login and password.
4. Tap Mode Evaluation Setup (Recommended)
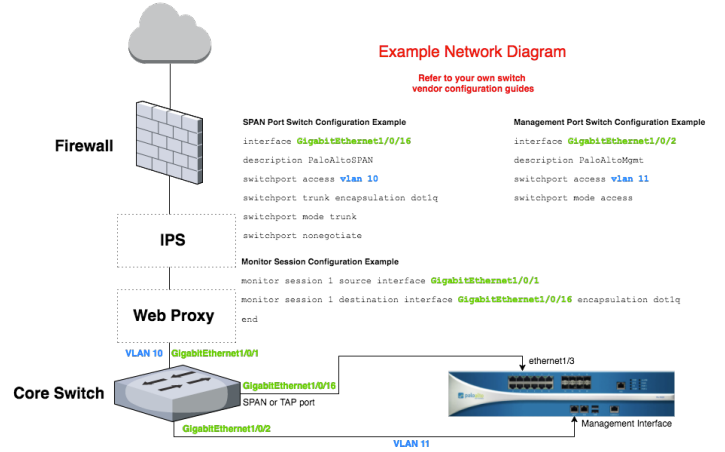
Ensure that the evaluation unit is on the inside of the network (behind any existing firewall, IPS, web proxy, etc) and is receiving mirrored or spanned traffic from the core switch. By default, the TAP interface on the evaluation unit is ethernet1/3. Also, ensure that the Management Interface is connected and has external (https) access as well as being internally accessible.
a. DEVICE Tab configuration
Use the web interface to perform the initial setup by browsing (https://x.x.x.x) to the IP you assigned.
- Device Tab > Setup > Interfaces sub-tab > Management (interface name):
These apply to the management interface only. These are the same settings previously configured through the CLI. Verify they are correct and/or configure the IP Address, Netmask, and Default Gateway, then click OK.
- In PAN-OS 7 or 7.1, the path is Device Tab > Setup > Management > Management Interface Settings > Edit button (gear icon).
- In PAN-OS 7 or 7.1, the path is Device Tab > Setup > Management > Management Interface Settings > Edit button (gear icon).
- Device Tab > Setup > Management > General Settings > Edit button:
Insert your AD Domain suffix, correct the Time Zone, and set the correct Time and Date for your local geographic area. Then click OK. Clock changes may require you to log back in by using refresh or browsing to (https://x.x.x.x) again, due to cookie expiration. - Device Tab > Setup > Services sub-Tab > Edit button (gear icon):
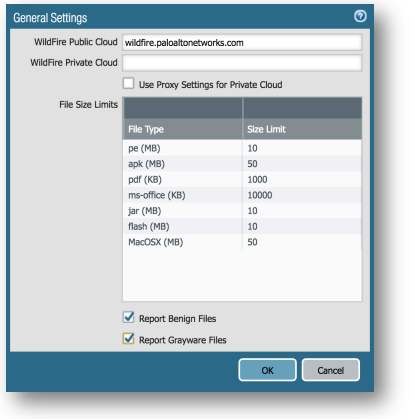
Set the Primary DNS Server to your own internal DNS server IP, then click OK. If this was done previously in the console, you will see these values present, and you may skip this step. Alternately, you may use a public DNS such as 4.2.2.2 and/or 8.8.8.8. - Device Tab > Setup > WildFire sub-Tab > General Settings > Edit button:
Set File Size Limits to their maximum values. Click each default size limit and enter the max values for each File Type (flash=10, pk=50, PDF=1000, jar=10, PE=10, ms-office=10000, MacOSX=50). Check the boxes next to Report Benign Files and Report Grayware Files), then click OK. - Commit your changes to this point by clicking Commit in top right corner. Commit again to confirm, then Close. Close moves the commit dialog to the background, but it is still running. You may click Tasks in the bottom right corner of the console to see background running and previous tasks.
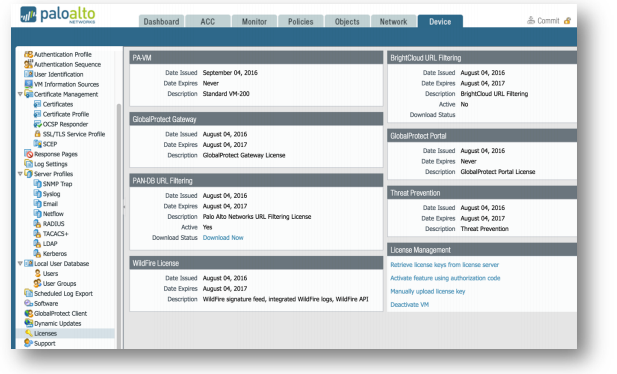
- Device Tab > Licenses:
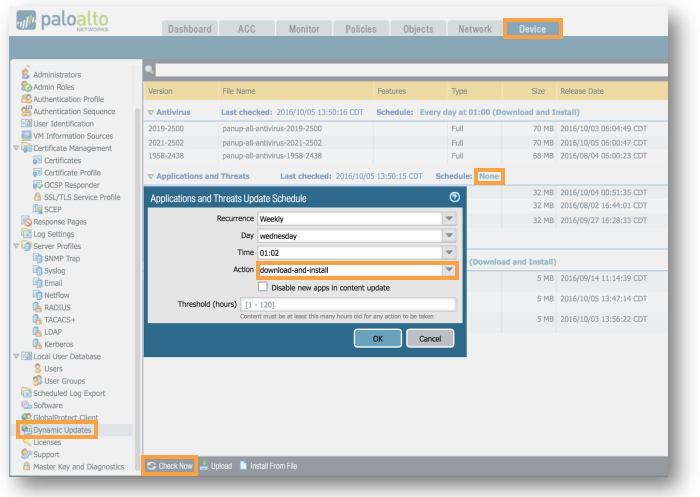
Click on Retrieve license keys from license server. If your licenses fail to appear or you get an error, the problem lies somewhere with the assigned management IP, its ability to get to the internet, and/or a misconfiguration of DNS not allowing our server name to resolve. - Device Tab > Dynamic Updates:
If Antivirus, Applications and Threats, or WildFire are not present, click Check Now at the bottom left hand corner. The first item to appear is Applications and Threats.
- Click Download, then Install after Applications and Threats are downloaded.
- Click Check Now again - this time Antivirus and any other subscriptions should appear.
- Click Download, then Install after Antivirus is downloaded.
- Click None next to Schedule for each component and set each to Download and Install. Antivirus should be set to Daily, Applications and Threats set to Weekly, and WildFire set to Every Minute (NOTE: In earlier versions of PAN-OS, the maximum frequency for the WildFire schedule is Every 15 Minutes)
b. NETWORK Tab configuration (For Vwire mode, jump to page 29)
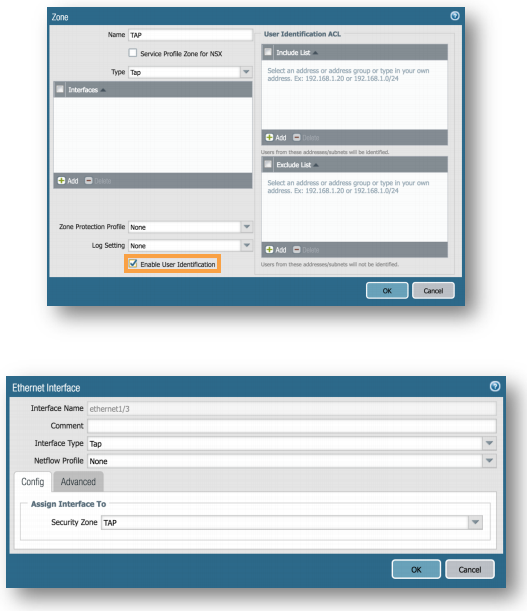
- Network Tab > Zones > Add:
Set Name to TAP, Type to Tap, and Check the box next to Enable User Identification, then click OK - Network Tab > Interfaces > ethernet1/3:
Set Interface Type to Tap and Security Zone to TAP, then click OK
5. Basic Security Policy (firewall rule) Setup
-
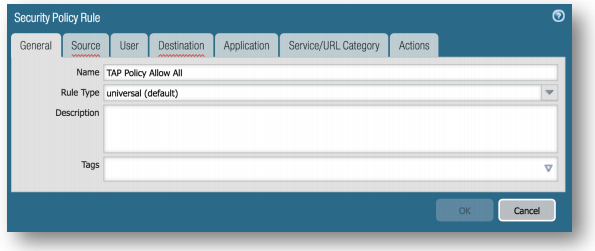
Policies Tab > Security > Add
-
General Tab, Set Name to TAP Policy Allow All or whatever label you choose
-
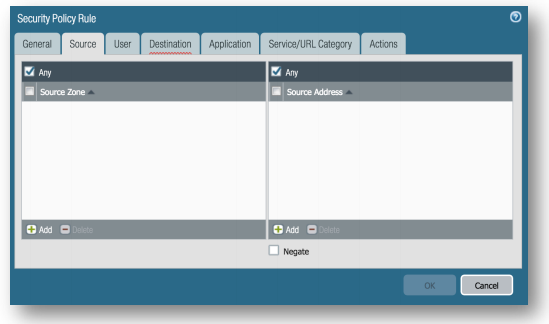
Source Tab, Select Any for Source Zone and Source Address
-
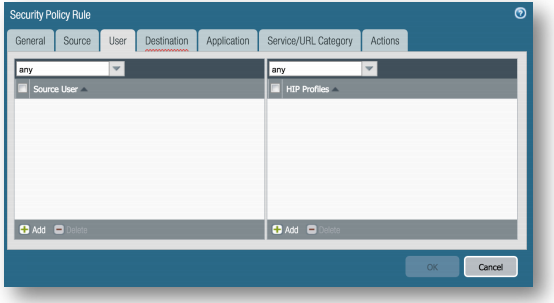
User Tab, Select Any for Source User and HIP Profiles
-
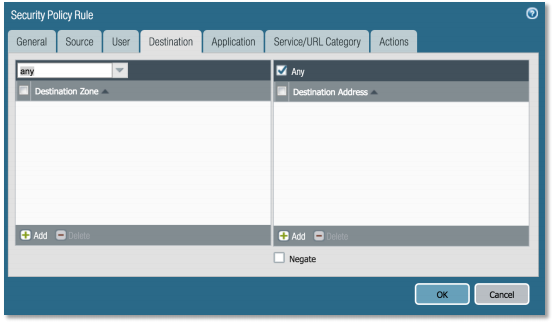
Destination Tab, Click the drop down on Destination Zone and choose any
-
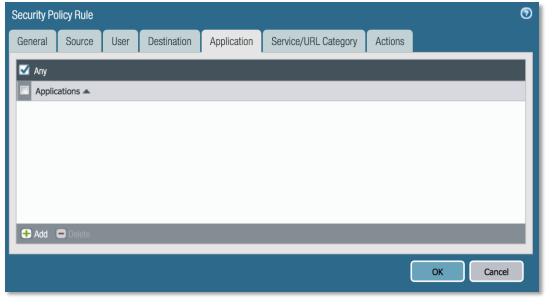
Application tab, Select Any on Applications
-
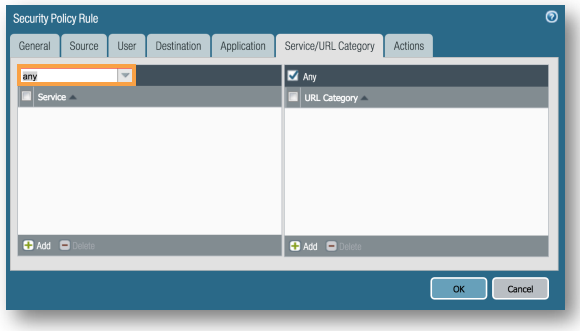
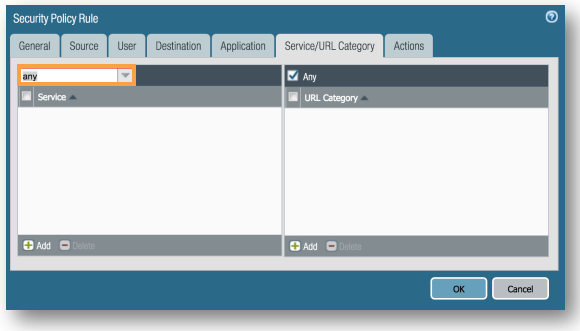
Service/URL Category tab, Click the drop down on Service select any. This will ensure that regardless of an application’s default ports, we will still log it on any/all ports we observe it on.
-
Service/URL Category tab, Select Any on URL Category.
-
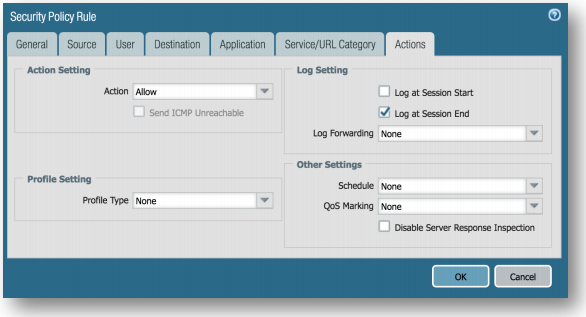
Actions tab, Select Allow for the Action. Leave all else as None for now. Click OK. You should now see this policy in your Security Policy list.
6. Security Profiles Setup: Baseline Prevention Config
To enable the threat prevention features of the next-generation firewall, you will need to create re-usable objects which will then be applied to any "Allow" rules, to have those features take effect. In a TAP mode deployment, threats would not actually be blocked but will appear in the logs based on your Security Profile ACTION settings.
When it comes to security profile Action settings, Alert = let it happen but log it, Allow = let it happen don’t even log it, and all other actions are some form of block. Drop, reset-both, block-ip, and others are all examples of a blocking setting. At a minimum, all configs should use Alert – but best practice is to block threats, not just log them. The following is a sample baseline configuration that would provide blocking and logging of threats and URL activity.
-
Objects Tab > Security Profiles > Antivirus:
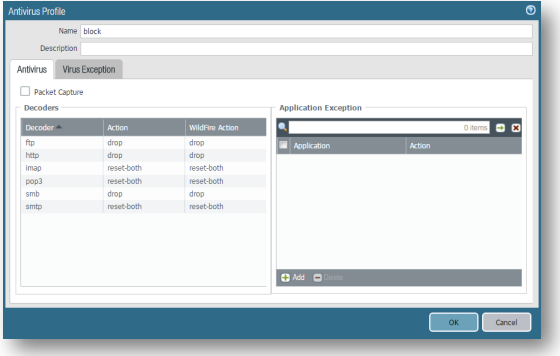
Click Add, Set Name to block and Action and WildFire Action for http, smb, and ftp to DROP. For email protocols smtp, pop3, and imap, set Action and WildFire Action to reset-both. Optional: Click the check box next to Packet Capture. Click OK. -
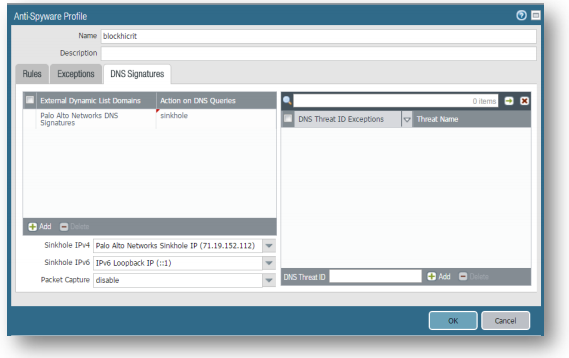
Objects Tab > Security Profiles > Anti-Spyware:
Click Add, Set Name to block. -
On the Rules tab, click Add, Set Rule Name to block, Threat Name to any, Category to any, Action to Drop, Packet Capture to single-packet, for Severity High or Critical. Click OK on the Anti-Spyware Rule window.
-
Add another rule, Set Rule Name to log, Threat Name to any, Category to any, Action to Default, Packet Capture to none, for Severity Medium, Low, and Informational. Click OK on the Anti-Spyware Rule window.
-
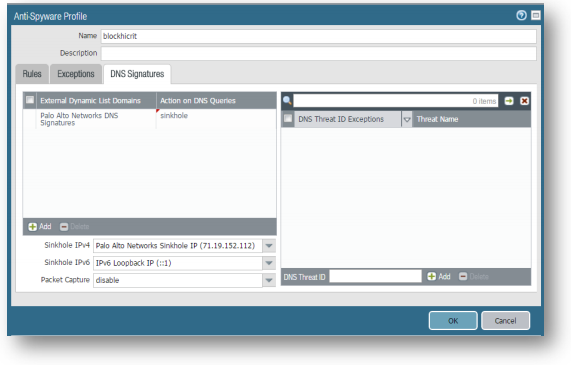
On the DNS Signatures tab, you may accept the default settings (sinkhole and Palo Alto Networks predefined sinkhole IP).
-
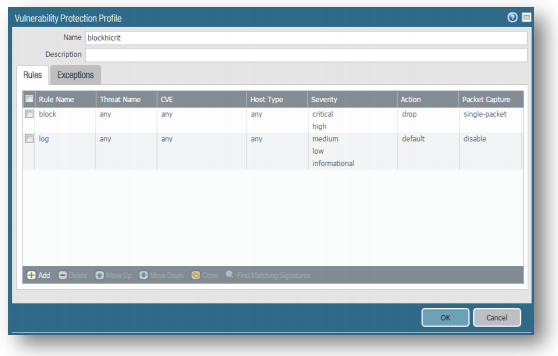
Objects Tab > Security Profiles > Vulnerability Protection:
Click Add, Set Name to blockhicrit. -
On the Rules tab, click Add, Set Rule Name to block, Action to Drop, Host Type to any, Category to any, for Severity High and Critical, Packet Capture to single-packet, CVE to any, and Vendor ID to any. Click OK on the Vulnerability Protection Rule window.
-
Add another rule, where Rule Name set to log, Action to Default, Host Type to any, Category to any, for Severity Medium, Low, and Informational. Packet Capture to none, CVE to any, and Vendor ID to any. Click OK on the Vulnerability Protection Rule window, then OK again on the Vulnerability Protection Profile window.
-
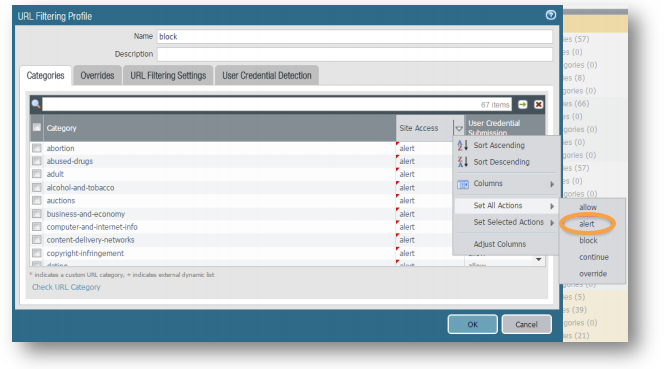
Objects Tab > Security Profiles > URL Filtering:
Click Add, Set Name to block, hover over the Site Access column, click the down arrow icon, then Set All Actions to alert. Click OK. -
Recommended to set Malware and Phishing categories to BLOCK.
-
PAN-OS 7 and 7.1 URL filtering profile does not have User Credential elements, and the web interface looks
slightly different, but it's the same process may be used.
-
-
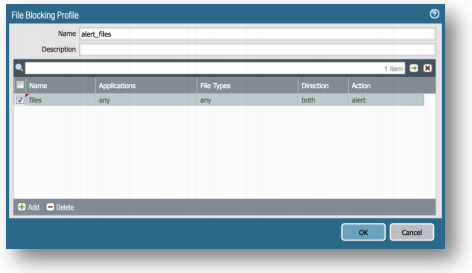
Objects Tab > Security Profiles > File Blocking:
Click Add, set Name to alert_files. Click Add inside the File Blocking Profile window and set Name to files, Applications to any, File Types to any, Direction to both, and Action to alert. -
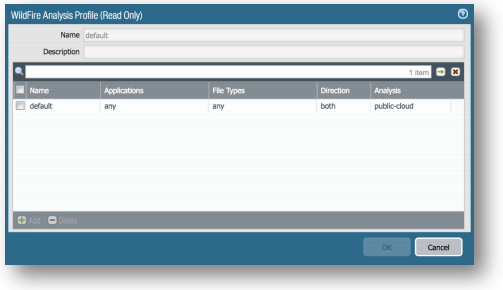
Objects Tab > Security Profiles > WildFire Analysis:
There should already have a default policy where Applications is set to any, File Types is set to any, Direction is set to both, and Analysis is set to public-cloud. If this is present, nothing else is needed to be done.
-
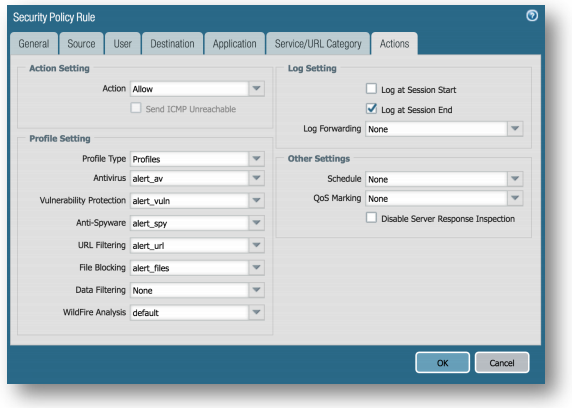
Policies Tab > Security: Click on the rule name TAP Policy Allow All to open up the rule you created previously.
-
On the Actions tab, select Profiles from the Profile drop down box. This will open up your security profile slots.
-
Set the Profile Settings to match what you named your security profiles:
-
Antivirus > block
-
Vulnerability Protection > blockhicrito Anti-Spyware > blockhicrit
-
URL Filtering > block
-
File Blocking > alert_files
-
Data Filtering > None
-
WildFire Analysis > default
-
Click OK
-
as under WildFire Submissions.
7. User-ID Setup
to create rules/polices which are specific to users or groups of users. This setup requires you to connect to your
LDAP server and scrape event logs from your Active Directory Domain Controller(s).
a. Setup and connect to your LDAP Server
-
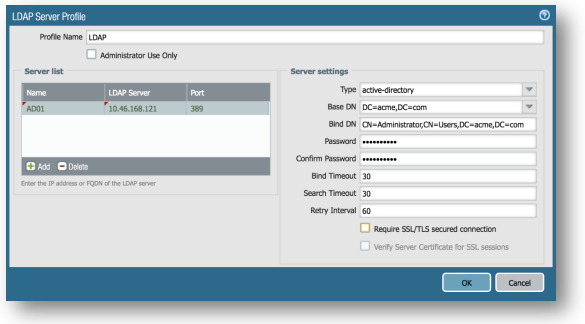
Device Tab > Server Profiles > LDAP:
Click Add. Set Profile Name to LDAP and make sure Administrator Use Only is unchecked.-
Click Add in the Server list section and set Name to an appropriate identifier (for example, AD01), LDAP Server to the IP address of your Domain Controller (for example, 10.46.168.121), and Port to 389.
-
-
Under Server settings on the right:
Set Type to active-directory, Base DN should auto-populate when you pull down the pick list. If it does not, try unchecking the "Require SSL" box and try again. -
Bind DN to the UPN or full distinguished name of an Administrator on the domain (for example, Administrator@acme.local or CN=Administrator,CN=Users,DC=acme,DC=local), and the Password and Confirm Password fields for that user.
C:\>dsquery user
To find a specific user, you can type dsquery user –name <user>:
C:\>dsquery user –name admin*
The result, which can be inserted into the Bind DN field, will look something like:
CN=administrator,CN=Users,DC=acme,DC=com
b. Group Mapping Setup
-
This step is to ensure that LDAP queries are able to be processed.
-
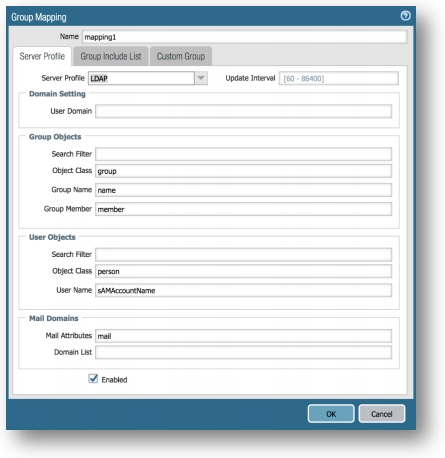
Device Tab > User Identification > Group Mapping Settings Tab > Click Add. Set Name to mapping1 and select LDAP from the Server Profile drop down box. Default values should pre-populate:
-
Group Objects
-
Object Class > group
-
Group Name > name
-
Group Member > member
-
-
User Objects
-
Object Class > person
-
User Name > sAMAccountName
-
-
Mail Domains
-
Mail Attributes > mail
-
-
Enabled is checked
-
-
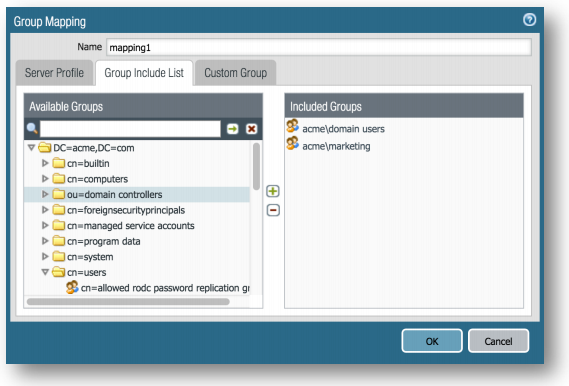
Group Include List Tab:
Double-click on the domain tree under Available Groups. If the tree does not populate, go back to step 8.1 and change the user in the Bind DN configuration. If the tree does break out, this means you are successfully querying LDAP with the credentials you entered previously. -
You may leave Included Groups List empty, meaning all groups are searched, or select the groups you want to monitor and click the green (+) icon to add them to Included Groups on the right. Click OK when finished.
c. Agentless User-ID Setup
-
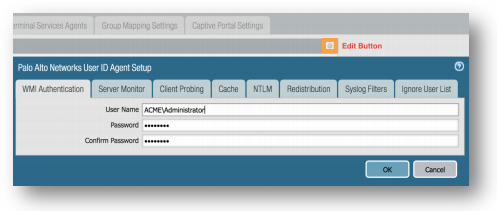
Device Tab > User Identification > User Mapping > Palo Alto Networks User ID Agent Setup:
Click the Edit button (the gear icon at the top right of the section). On the WMI Authentication tab, enter the User Name of a domain administrator in the format of DOMAIN\username (for example, ACME\Administrator) and the password for this user or service account.
-
Device Tab > User Identification > User Mapping > Server Monitoring:
If you entered your AD domain suffix previously, you may auto-discover your domain controller(s) using the Discover button.
If not, use: -
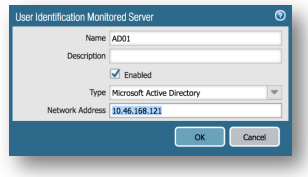
Device Tab > User Identification > User Mapping > Server Monitoring:
Click Add. Set Name to the name of the domain controller (for example, AD01), make sure the Enabled box is checked, set Type to Microsoft Active Directory, and enter the server’s IP address for Network Address (for example, 10.46.168.121), then click OK.
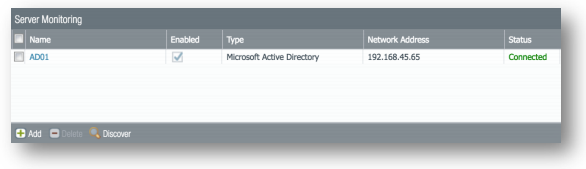
- Commit your changes. You should now see the server(s) you added show up with a Connected status under Server Monitoring.
At this point, you should be able to add users and group to Security Policies via the User tab in addition to seeing User-ID information in the traffic logs. If you do not see users in the traffic logs, wait 15 minutes to an hour for that information to start populating. If it still does not show up, revisit the configuration.

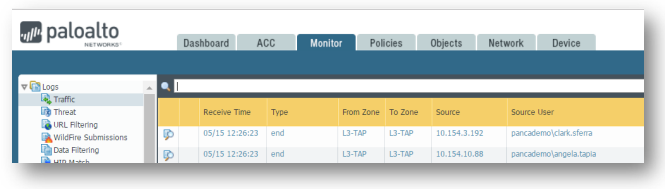
8. TAP Mode Evaluation Final Check
Almost immediately, you should have Traffic logs, but check that the Source User column is starting to populate with user names. It may require users to log out, and log back into the network, to get those user names to really start flowing, so sometimes this column doesn’t fully populate until the next work morning. Also, you should be seeing accurate representations under the Application column. If you are seeing predominately "incomplete," "not-applicable," or "Insufficient Data" then it is possible we are not seeing full sessions on our tap, and we should re-examine the SPAN port configuration.
Most environments will generate at least a few informational level threats, so there should show something (hopefully NOT criticals) in the Threat log.
URL filtering will have logs quickly, assuming there is any browsing activity, as well as User-ID on them.
WildFire submissions may not populate for approximately 15 minutes to several hours after deployment. This is a log of files that were submitted to WildFire for analysis. Given that SSL decryption cannot be deployed in TAP mode, this means we will be seeing and/or submitting files found in clear text traffic. Furthermore, files already known by hash value to WildFire will not be submitted. To expedite this testing process, you may download an inert sample file that will register as completely unique to WildFire at http://wildfire.paloaltonetworks.com/publicapi/test/pe.
NOTE: Existing files known to WildFire as malicious will not appear in submission logs, rather search the Threat Logs for Type = 'wildfire-virus’ to see those preventions.
Data Filtering logs should populate rather quickly, but in TAP mode, relies on files seen in clear text (non-encrypted) protocols.
If all five logs are populating, along with User-ID, then your TAP mode evaluation configuration is complete.
For best results, allow the device to collect logs using this configuration for at least seven days. Any time after those initial 7 days, revisit your logs with your Palo Alto Networks (or partner) engineer and generate a Security Lifecycle Review (SLR) report. The SLR is an executive style report that reflects a snapshot-in-time of the last seven days of traffic.
9. Vwire Evaluation Setup
- Configure the first virtual wire interface
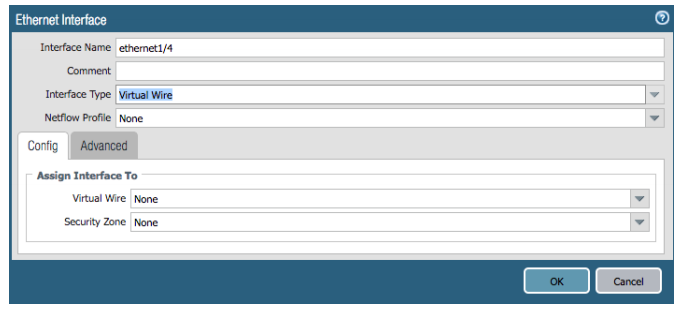
- Select Network Tab > Interfaces > Ethernet and select an interface you have cabled (ethernet1/4 in this example)
- Set the Interface Type to Virtual Wire and click OK.
- Repeat this step to configure a second Virtual Wire interface (ethernet1/5 in this example)
- Attach the interfaces to a virtual wire object
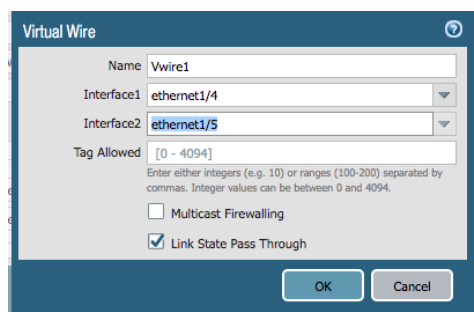
- Select one of the virtual wire Ethernet interfaces, on the Config tab, select Virtual Wire and click New Virtual Wire
- Enter a Name for the virtual wire object
- Select the two Virtual Wire interfaces you just created as Interface1 and Interface2 (it doesn't matter which interface is assigned to 1 or 2)
- Attach the interfaces to a virtual wire object
- Create a separate security zone for each virtual wire interface
- Select Network > Zones and add a zone
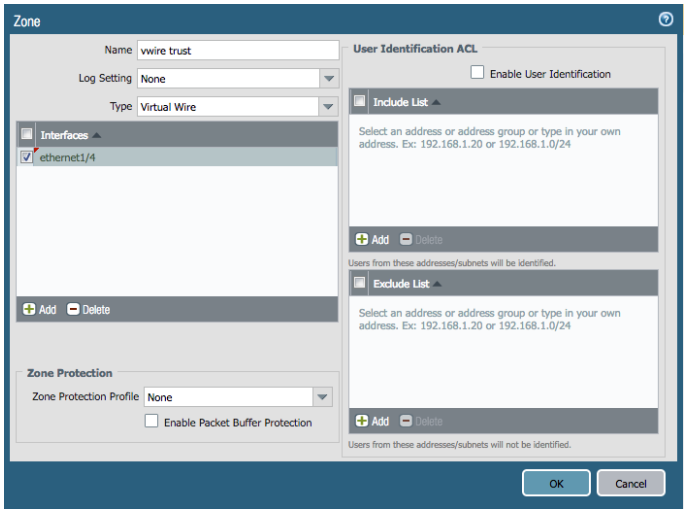
- Enter the name of the zone (such as Vwire trust)
- For Type select Virtual Wire
- Add the Interface that belongs to the zone (ethernet1/4 in this example)
- Click OK
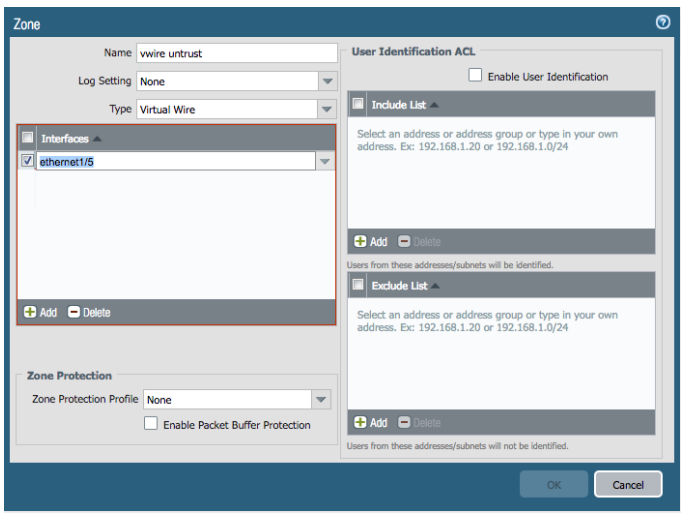
- Create a second zone for the second Virtual Wire interface
- Enter the name of the zone (such as vwire untrust)
- For Type select Virtual Wire
- Add the interface that belongs to the zone (ethernet1/5 in this example)
- Select Network > Zones and add a zone
10. Vwire Basic Security Policy (firewall rule) Setup
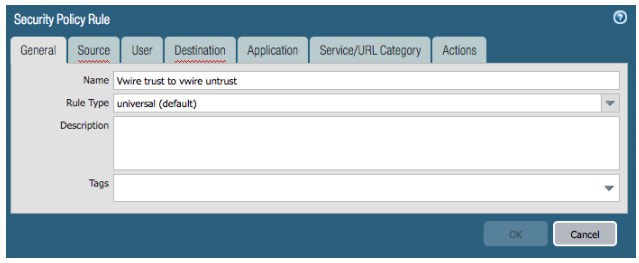
- Policies Tab > Security > Add
- General Tab, Set Name to 'vwire trust to vwire untrust' or whatever label you choose.
NOTE: We will create this as an “Any to Any” Rule. Any configuration will reflect accurately in the logs however, so if you choose to write additional rules that do block things, those blocks will show in the logs.
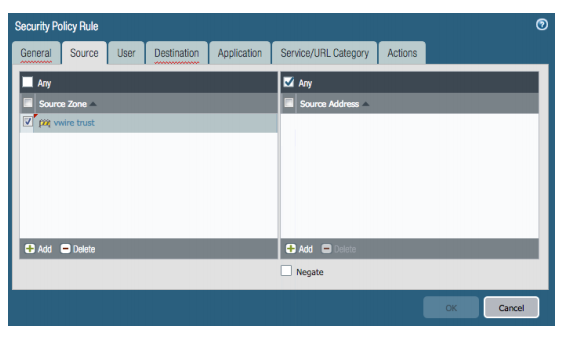
- Source Tab, Select Vwire trust for Source Zone and Any for Source Address
- User Tab, Select Any for Source User and HIP Profiles
NOTE: These will be users or groups pulled from your Active Directory Domain. Users and groups of users will only appear after User-ID has been configured.
- Destination Tab, Click the drop down on Destination Zone and choose Any
- Application tab, Select Any on Applications.
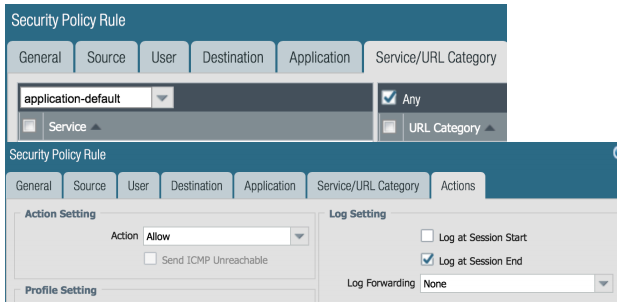
- Service/URL Category tab, Click the drop down on Service select any. This will ensure that regardless of an application’s default ports, we will still log it on any/all ports we observe it on.
- Service/URL Category tab, Select Any on URL Category.
- Actions tab, Select Allow for the Action. Leave all else as None for now. Click OK. You should now see this policy in your Security Policy list.
- Repeat this process to create a second Security Policy Rule, but now have the Source Zone as Vwire untrust, and the destination zone as Vwire trust
Commit to apply your policy to the data plane, making it now take effect.
After a minute or so, you should now be able to see traffic logging start to appear under Monitor > Logs > Traffic.
11. Layer 3 Evaluation Setup
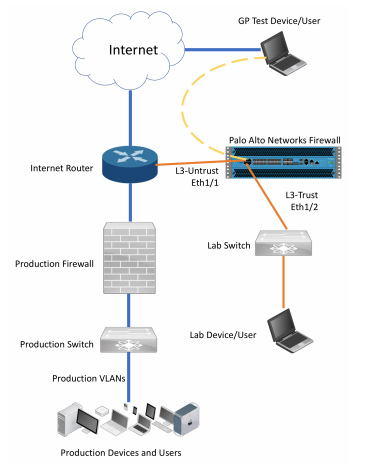
For this install, we are going to be within the production network, and it must be planned around the changes that can affect production traffic. For this guide, we are under the assumption that we are within the production network but not replacing the firewall. With a Layer 3 installation, you would also be able to test a GlobalProtect VPN setup as well.
Below is an example of this network diagram:
Example Environment:
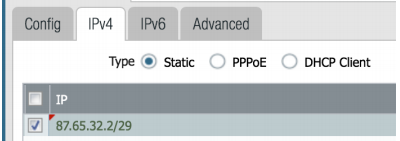
Public IP: 87.65.43.2/29
Next Hop: 87.65.43.1
eth1/1 interface connected to ISP
l3-trust Zone
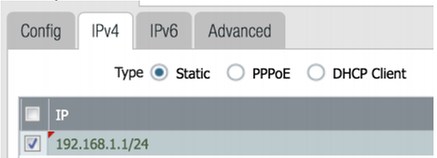
Priv. Subnet: 192.168.1.0/24
Firewall IP: 192.168.1.1
eth1/2 interface connected to local switch
Firewall will act as router
Palo Alto Networks Firewall configuration
For this, we will be utilizing the web interface to perform our configuration moving forward. To reach this page, browsing to the IP that was setup for the management interface (https://x.x.x.x).
Resulting page should look like this:
Device tab config is same as Tap mode
When looking at the user interface for the firewall, we have seven tabs across the top. We will now select the Network tab.
Now that we are in the network tab, we are going to create our security zones by selecting Zones on the left.
At the bottom left of the page, you have an Add button with a green plus symbol. Click on Add so you can create our Untrust Zone.
Type: Layer3
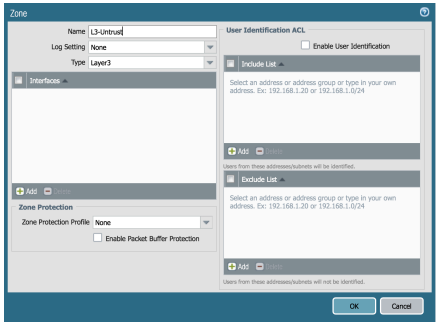
Type: Layer3
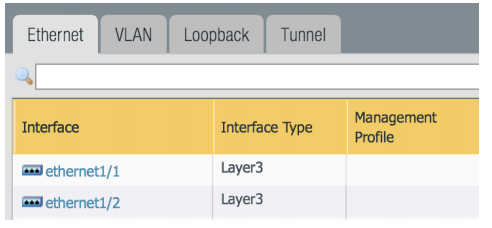
Our next step will be to configure our ethernet interfaces and assign them to our new Security Zones. We will click on Interfaces on the left which is above Zones. The page should look like this.
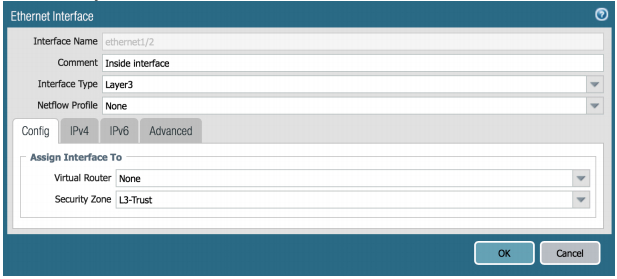
Click to open ethernet1/1 and configure the following:
Interface Type: Layer3
Virtual Router: none
Security Zone: L3-Untrust

Click to open ethernet1/2 and configure the following:
Interface Type: Layer3
Virtual Router: none
Security Zone: L3-Trust

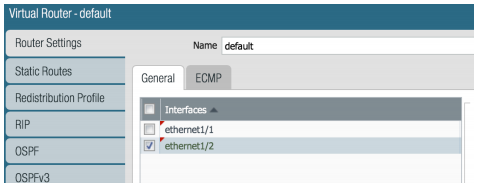
Destination: 0.0.0.0/0
Interface: ethernet1/1
Next Hop: IP address, 87.65.43.1
It should look like the image below:
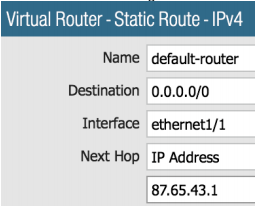
Our final network configuration left is to create our NAT policy. For this, we will be leaving the Network tab and going to the Policies tab.


General tab
NAT Type: ipv4
Destination Zone: L3-Untrust
Destination Interface: ethernet1/1
Address Type: Interface Address
Interface: ethernet1/1
IP Address: Select the IP address of the outside interface from the list.
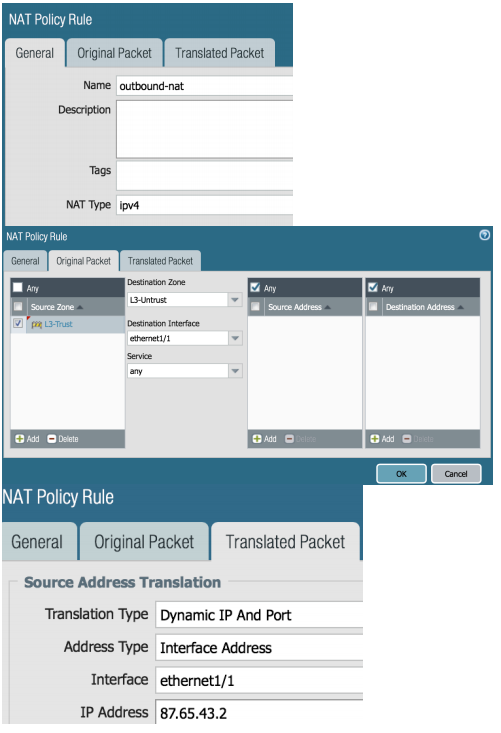
We will now create our policy to allow traffic leaving our network. To complete this, we will navigate to the Security Policies configuration page. This is on the left above NAT. Once we have reached that page, click Add on the lower left so that we can create our policy.
General tab:
Rule Type: universal (default)
Source Address: Any
Destination Address: Any
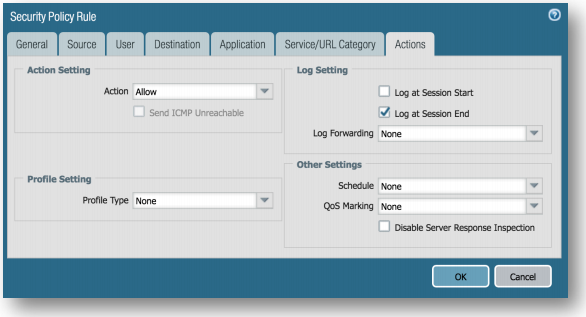
Log Setting: Log at Session End
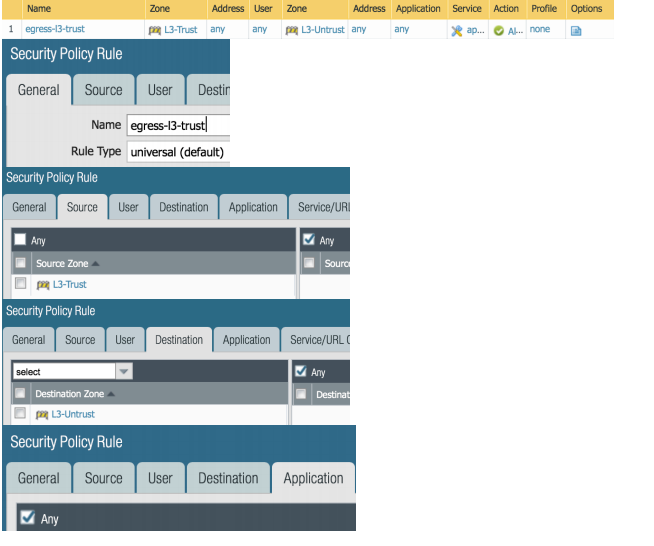

Test and Validate Connectivity
- Connect an endpoint to the ethernet1/2 interface or a switch attached to the ethernet1/2 interface.
- Configure the endpoint’s network settings with the following:
- An IP Address in the 192.168.1.0/24 subnet
- The Gateway IP address with firewall interface (192.168.1.1)
- DNS servers reachable from the outside interface (e.g. 4.2.2.2 and 8.8.8.8)
- Attempt to access the internet.
- 15244 Views
- 1 comments
- 1 Likes
- Custom Signatures With ChatGPT and AI Security in General Articles
- Support FAQ: Flood Attacks - Configuration & Troubleshooting Best Practices in Support FAQ
- A Guide to NAT on Palo Alto Networks Firewalls in Support FAQ
- Best Practices for Configuration Management Performance on Panorama in General Articles
- Identify and Deploy Specific PAN-OS Versions of VM-Series on Google Cloud in General Articles
-
"Address Objects"
1 -
10.0
1 -
10.1
1 -
10.2
2 -
ACC
1 -
Active-Passive
1 -
AD
1 -
address objects
1 -
admin roles
1 -
Administration
6 -
Administrator Profile
1 -
ADNS
1 -
Advanced DNS Security
1 -
Advanced URL Filtering
2 -
Advanced WildFire
1 -
AI
2 -
AI Security
1 -
AI Threat
1 -
AIOPS
1 -
Ansible
1 -
antivirus
1 -
API
1 -
App-ID
1 -
applications
2 -
APS
1 -
Artificial Intelligence
1 -
Asset Management
1 -
Authentication
6 -
Authentication Profile
1 -
Authentication Sequence
1 -
automatically acquire commit lock
1 -
Automation
3 -
aws
3 -
Basic Configuration
4 -
Beacon
1 -
Best Practices
6 -
Block List
1 -
categories
1 -
certificates
1 -
Certification
1 -
Certifications
1 -
Certifications & Exams
1 -
CLI
5 -
CLI command
3 -
Cloud Automation
1 -
Cloud Identity Engine
1 -
cloud ngfw
1 -
cloud security
1 -
Collector Group
1 -
Commit and Push
1 -
Commit Process
1 -
Configuration
8 -
Configuration and Management
3 -
Configure Next Generation Firewall
1 -
console
1 -
Cortex
1 -
Cortex Data Lake
2 -
Cortex XDR
3 -
CPSP
1 -
Custom Signatures
3 -
cyber elite
1 -
cyberelite
11 -
Cybersecurity
1 -
dag
1 -
DDoS
1 -
Debug
1 -
debugging
2 -
Default Policy
1 -
discussions
1 -
DLP
1 -
EDL
2 -
education
1 -
Education and Training
1 -
Education Services
1 -
Educational Services
1 -
Effective Routing
1 -
End to End Encryption
1 -
Endpoint
1 -
export
1 -
failover
1 -
FAQ
1 -
file upload
1 -
Filtering
2 -
Firewall
2 -
Firewall VM-Series
2 -
Focused Services
3 -
Focused Services Proactive Insights
2 -
gateway
1 -
Gateway Load Balancer
2 -
GCP
2 -
GCP Firewall
1 -
geolocation
1 -
Getting Started
1 -
GitHub
1 -
Global Protect
1 -
Global Protect Cookies
1 -
GlobalProtect
7 -
GlobalProtect App
1 -
globalprotect gateway
1 -
GlobalProtect Portal
2 -
google
2 -
Google Cloud
3 -
google cloud platform
2 -
Hardware
2 -
Header Insertion
1 -
High Availability
1 -
How to
1 -
HTTP
1 -
https
1 -
Hybrid Cloud
1 -
ike
3 -
import
1 -
Installation & Upgrade
1 -
IoT
1 -
IPSec
4 -
IPSec VPN Administration
1 -
kerberos
1 -
Layer 2
1 -
Layer 3
1 -
Learning
1 -
licenses
1 -
local user
3 -
Log Cluster Design
1 -
Log Collection
3 -
Log Collector Design
2 -
Logging
1 -
login
1 -
Logs
3 -
Management
8 -
Management & Administration
5 -
MFA
1 -
Microsoft
1 -
Microsoft 365
1 -
Migration
1 -
minemeld
4 -
multi factor authentication
1 -
multi-factor authentication
1 -
multi-vsys
1 -
NAT
1 -
NetSec
1 -
NetSec Newsletter
1 -
network security
34 -
Network Security Management
1 -
Network-Security
1 -
Networking
1 -
newsletter
2 -
Next Generation Firewall
4 -
Next-Generation Firewall
42 -
next-generation firewall. network security
1 -
Next-Generation Firewall. NGFW
6 -
NGFW
30 -
NGFW Configuration
11 -
NGFW Newsletter
1 -
Nominated Discussion
1 -
Objects
2 -
OTP
1 -
PA-3200 Series
1 -
PA-400
1 -
pa-440
2 -
PA-5400 series
1 -
PA-800 Series
1 -
pa-820 firewall
1 -
Packet Buffer
1 -
packet debug
1 -
packet diag
1 -
PAN-OS
16 -
PAN-OS 10.2
1 -
PAN-OS 11.0
1 -
PAN-OS Prisma Access
1 -
Panorama
11 -
Panorama Configuration
2 -
PBF
1 -
PCNSA
1 -
PCNSE
1 -
performance
2 -
policies
2 -
policy
3 -
Policy Based Forwarding
1 -
Prisma Access
7 -
Prisma AIRS
1 -
Prisma SASE
2 -
Prisma SD-WAN
1 -
proactive insights
2 -
Prompt Poaching
1 -
Radius
1 -
Ransomware
1 -
RBI
2 -
region
1 -
Registration
1 -
Remote Browser Isolation
3 -
reporting and logging
1 -
RestAPI
1 -
Risk Management
1 -
Routing
1 -
SAML
1 -
SASE
1 -
script
2 -
SD WAN
1 -
SDWAN
1 -
Search
1 -
Security Advisory
1 -
Security automation
1 -
security policy
4 -
security profile
1 -
Security Profiles
2 -
Selective Push
1 -
Session Packet
1 -
Setup & Administration
8 -
Site-to-Site VPN
1 -
Split Tunneling
2 -
SSL
1 -
SSL Decryption
2 -
SSL Forward Proxy
1 -
SSO
1 -
Strata Cloud Manager
1 -
Strata Logging Service
2 -
Support Guidance
1 -
syslog
1 -
system modes
1 -
Tag
2 -
tags
2 -
Terraform
2 -
Threat
1 -
threat log
1 -
Threat Prevention
1 -
Threat Prevention License
1 -
Tips & Tricks
1 -
TLS
1 -
traffic_log
1 -
Traps
1 -
Troubleshoot
2 -
Troubleshoot. logs
1 -
Troubleshooting
6 -
tunnel
2 -
Tutorial
2 -
Unified Monitoring
1 -
upgrade
1 -
upgrade-downgrade
2 -
url categories
1 -
URL Filtering
2 -
URL-Filtering
1 -
User ID Probing
1 -
User-ID
1 -
User-ID & Authentication
1 -
User-ID mapping
1 -
userid
1 -
VM Series
1 -
VM-Series
7 -
VM-Series on AWS
3 -
VM-Series on GCP
2 -
VPC Flow logs
1 -
VPN
3 -
VPNs
4 -
Vulnerability
2 -
Vulnerability Protection
1 -
WhatsApp
1 -
WildFire
2 -
Wildfire License
1 -
wmi
1 -
XDR
1 -
xml
2 -
XML API
2
- Previous
- Next