- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Hybrid and Multi Cloud Connectivity with PAN-OS SD WAN
- LIVEcommunity
- Articles
- General Articles
- Hybrid and Multi Cloud Connectivity with PAN-OS SD WAN
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
on 02-07-2024 11:01 AM
Introduction
Organizations today adopt hybrid cloud infrastructure to provide a balanced approach, enabling them to combine the benefits of public and private clouds to meet their specific business needs, optimize costs, and ensure a secure and compliant IT environment.
At the same time, while adopting cloud, organizations also adopt a multi cloud strategy to solve different business use cases.
This entire infrastructure is interconnected to provide communication between the environment. Hence it is important to perform careful planning, robust security measures, and the use of appropriate networking technologies to ensure efficient and secure communication between the resources.
This document describes different deployment options which can be used to connect an on-prem branch/datacenter to a cloud environment , and also connectivity between multi cloud infrastructure. This document captures the design options using PAN-OS SD WAN to provide the connectivity. SD WAN components and features are out of scope of this document.
Why PAN-OS SD WAN?
Thick Branch: In a thick branch or datacenter environment, where applications are usually hosted in the on-prem environment, providing security at the perimeter is crucial. This is achieved by the PAN-OS SD WAN subscription on the NGFW
Dynamic and best path selection: PAN OS SD-WAN solution is designed to be application-aware. They can identify and classify different types of traffic, allowing for granular control and prioritization based on the specific needs of each application. This includes mission-critical applications that require low latency and high reliability.
Dynamic path selection: allowing for real-time decision-making regarding the best path for traffic based on the current network conditions. It continuously monitors the performance of available network links and selects the most optimal path for specific applications or traffic types.
Need for control over the IPSec configuration: Often in a secure environment, like a Fintech organization, where strict compliance requirements exist, customers would want to mitigate the security risks with certain network connection encryption. The native SD WAN controls cannot provide much flexibility into the configuration
Zero touch provisioning with Panorama: With PAN-OS SD WAN, customers can take the benefit of ZTP (zero touch provisioning) that permits hands-off approach to SD WAN deployment,configuration and communication between hub and spokes. This capability enables the customer to deploy SD WAN effortlessly and establish connectivity.
Cost Effective Approach- With the hub and spoke architecture of SD WAN, we can connect multiple branch data centers and remote users. When we compare it with native CSP solution with a private link, this only solves one part of connectivity. Customers end up investing more on other infrastructure elements, making it an expensive solution.
Security Enforcement: Security policies can be configured in the edge firewall in branch/DC to inspect the traffic and provide enforcement. Any internet inbound/outbound traffic can also be inspected and enforced in the edge firewall providing the internet access.
Deployment Models:
In this document, we will take examples of connectivity with AWS. Every CSP has a different service and connectivity mechanism to deploy SD WAN architecture.
Connectivity with Transit Gateway Attachment:
When talking about the connection of an SD-WAN network to AWS, AWS Transit Gateway provides a managed highly-available and scalable regional network transit hub to interconnect VPCs and your SD-WAN network. Transit Gateway connect attachments provide a native way to connect your SD-WAN infrastructure and appliances with AWS. This makes it easy to extend your SD-WAN into AWS without having to set up IPsec VPNs.
Here, VM series can be the (Hub or Spoke) head-end deployed in a separate VPC. Traffic from branch/DC will terminate on the VM series. The Routes configured on VM series, will direct the traffic towards the transit gateway attachment. Once the traffic reaches the transit gateway, the traffic is forwarded based on the routes.
Similarly in the reverse direction, when the workloads in AWS want to communicate with workloads in DC, the TGW routes forward the traffic towards the VPC providing the SD WAN connectivity. VM series can be deployed in Active-Standby mode.
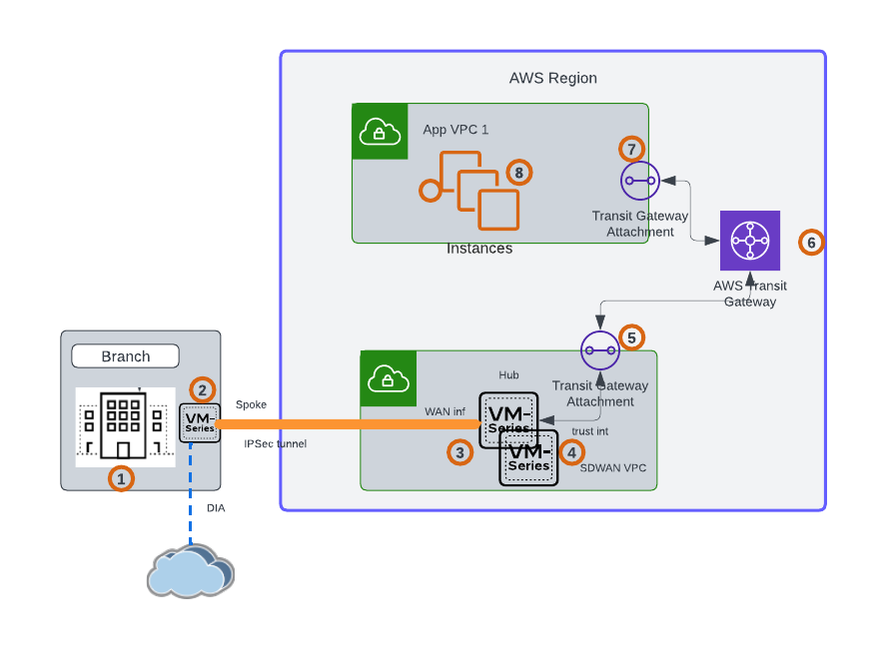
Traffic Flow:
- Traffic initiated from branch/DC is destined to the instances in App VPC1 within AWS
- Based on the route the traffic reaches the VM series in branch, which is the SD WAN device providing the edge connectivity
- The traffic is forwarded to the SD WAN VPC via the SD WAN overlay
- The VM series route forwards the traffic towards the trust interface.
- The traffic is forwarded to the TGW attachment based on the subnet route table in AWS
- Based on the TGW route table, the traffic is forwarded towards the destination VPC.
- Any internet traffic from the DC/Branch, takes the direct internet access from the edge firewall
Connectivity with Transit Gateway Connect Attachments:
Many AWS customers are using AWS Transit Gateway at the network edge to connect their global network to the AWS backbone. Transit Gateway connect attachments provide native way to connect SD WAN infrastructure to the cloud.
Transit Gateway connect attachments support Generic Routing Encapsulation (GRE) for higher bandwidth performance compared to a VPN connection. It supports Border Gateway Protocol (BGP) for dynamic routing, and removes the need to configure static routes. This simplifies network design and reduces the associated operational costs.
When integrating SD-WAN network to Transit Gateway using connect attachments, you have two common patterns. The first one is placing VM Series in a VPC within AWS. Then, you use a VPC attachment as underlying transport for the Transit Gateway connect attachment between the virtual appliances and the Transit Gateway, as can be seen in the figure below.
VM series can be deployed in Active-Standby mode.
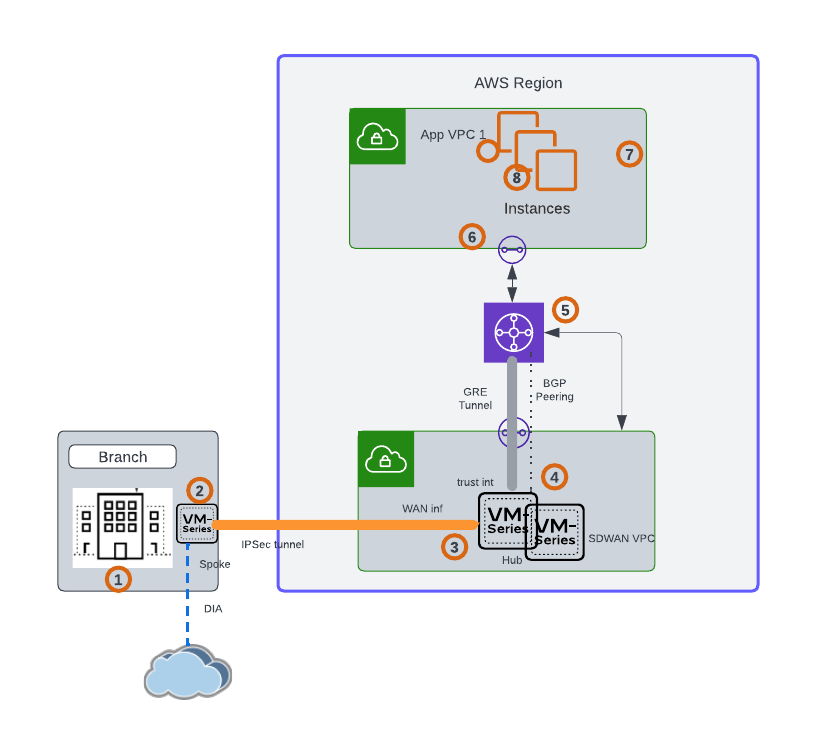
Traffic Flow:
- Traffic initiated from branch and destined to the instances in App VPC1 within AWS
- Based on the route, the traffic reaches the VM series in the branch.
- The traffic is forwarded to the VM Series in the SD WAN VPC via the SD WAN overlay
- The VM series route forwards the traffic towards the trust interface.
- The Transit Gateway connect attachment uses the VPC attachment as transport, and connects Transit Gateway to the VM Series in the SD WAN VPC using GRE tunneling and BGP.
- Based on the TGW route table, the traffic is forwarded towards the destination VPC.
- Any internet traffic from the DC/Branch, takes the direct internet access from the edge firewall
Connectivity with Site to Site VPN:
Another way to integrate your SD-WAN network to AWS Transit Gateway is by creating an AWS Site-to-Site VPN connection, peering the SD-WAN headend on VM Series, with the Transit Gateway using IPSec tunnels. The VM Series in the SD WAN VPC can use BGP to peer with the Transit Gateway to exchange route prefixes. If you want to increase the bandwidth, additional IPSec VPN connections can be used with Transit Gateway’s support for Equal-Cost Multi-Path (ECMP). VM series can be deployed in Active-Standby mode.
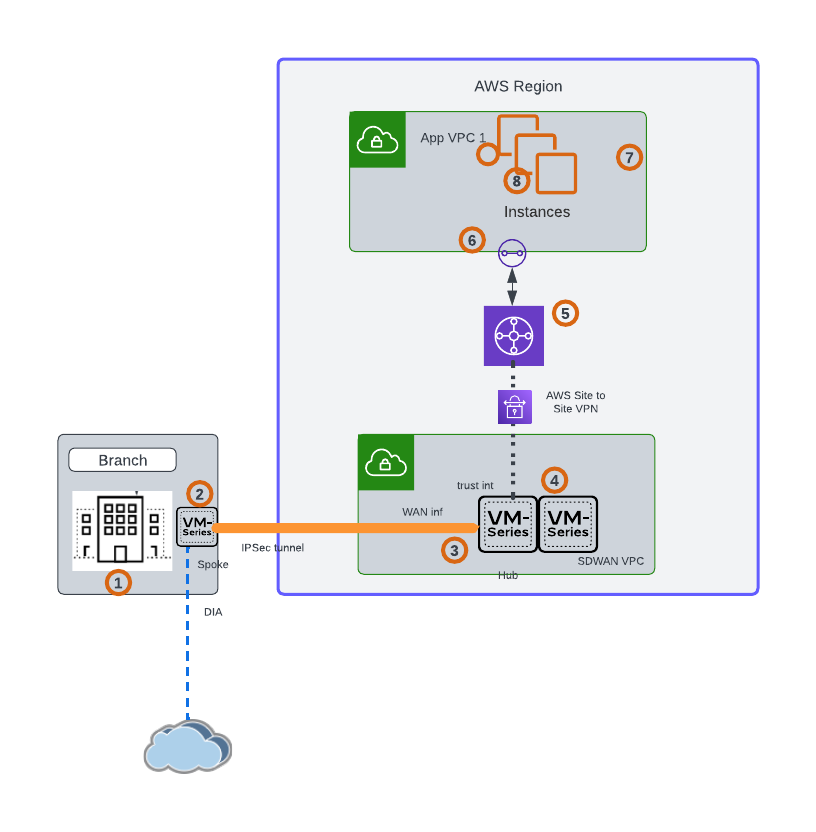
Traffic Flow:
- Traffic initiated from branch and destined to the instances in App VPC1 within AWS
- Based on the route the traffic reaches the VM series in branch.
- The traffic is forwarded to the SD WAN VPC via the SD WAN overlay
- The VM Series in the SD WAN VPC forwards the traffic to the Transit Gateway via the Site-to-Site VPN connection.
- Based on the TGW route table, the traffic is forwarded towards the destination VPC.
- Any internet traffic from the DC/Branch, takes the direct internet access from the edge firewall
Multi Cloud Connectivity with SD WAN Hub and Spoke:
You can connect your multi cloud deployment using PAN-OS SD WAN using hub and spoke or full mesh architecture. The VM series acting as hub can be in AWS DC or in the on-prem DC. Other environments, in cloud or other branch locations can host a VM series for providing spokes connectivity to the hub firewall. In the example below, we have the VM series on AWS and Azure acting as hub and VM series in the branch provides spokes connectivity.
VM series can be deployed in Active-Standby mode.
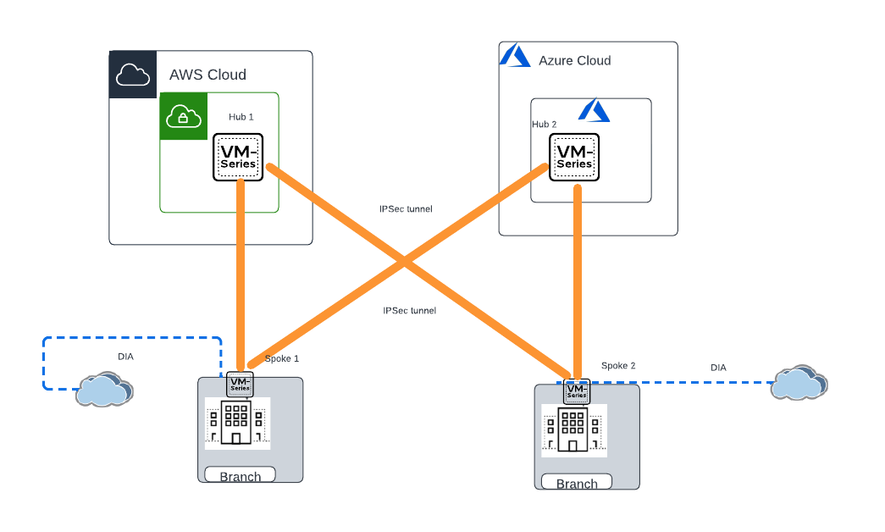
Traffic Flow:
- Traffic is destined towards applications hosted in cloud.
- Traffic reaches the hub firewall in AWS or Azure over SD WAN Overlay
- Based on the routing in VM series , the traffic gets forwarded towards the destination.
- The reverse traffic follows the same path.
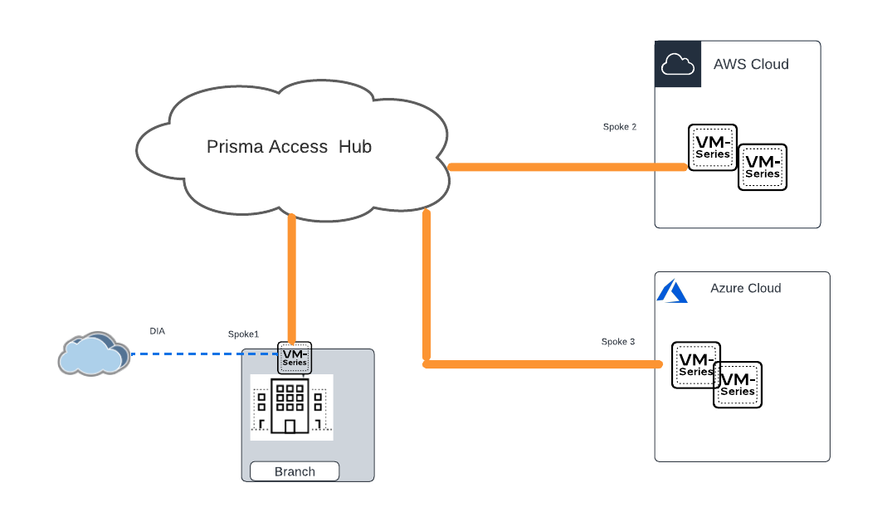
Connectivity with SD WAN Hub in Prisma Access
Prisma Access can also provide connectivity for your SD WAN overlay. Here Prisma Access acts as a hub for the SD WAN overlay. SD-WAN Plugin 2.2 provides Prisma Access hub support, in which PAN-OS firewalls connecting to Prisma Access compute nodes (CNs) achieve cloud-based security in an SD-WAN hub-and-spoke topology. In this topology, the SD-WAN hubs are Prisma Access CNs (IPSec Termination Nodes) and the SD-WAN branches are PAN-OS firewalls(VM Series/Hardware). A maximum of four hubs (any combination of PAN-OS hubs participating in DIA AnyPath and Prisma Access hubs) are supported. SD-WAN automatically creates IKE and IPSec tunnels that connect the branch to the hub. VM series can be deployed in Active-Standby mode.
References:
- 6457 Views
- 0 comments
- 0 Likes
-
"Address Objects"
1 -
10.0
1 -
10.1
1 -
10.2
2 -
ACC
1 -
Active-Passive
1 -
AD
1 -
address objects
1 -
admin roles
1 -
Administration
6 -
Administrator Profile
1 -
Advanced URL Filtering
2 -
Advanced WildFire
1 -
AI
1 -
AI Security
1 -
AIOPS
1 -
Ansible
1 -
antivirus
1 -
API
1 -
App-ID
1 -
applications
2 -
APS
1 -
Asset Management
1 -
Authentication
6 -
Authentication Profile
1 -
Authentication Sequence
1 -
automatically acquire commit lock
1 -
Automation
3 -
AWS
3 -
Basic Configuration
4 -
Beacon
1 -
best practices
6 -
Block List
1 -
categories
1 -
certificates
1 -
Certification
1 -
Certifications
1 -
Certifications & Exams
1 -
CLI
5 -
CLI command
3 -
Cloud Automation
1 -
Cloud Identity Engine
1 -
Cloud NGFW
1 -
Cloud Security
1 -
Collector Group
1 -
Commit and Push
1 -
Commit Process
1 -
Configuration
8 -
Configuration and Management
3 -
Configure Next Generation Firewall
1 -
console
1 -
Cortex
1 -
Cortex Data Lake
2 -
Cortex XDR
3 -
CPSP
1 -
Custom Signatures
3 -
cyber elite
1 -
cyberelite
11 -
dag
1 -
DDoS
1 -
Debug
1 -
debugging
2 -
Default Policy
1 -
discussions
1 -
EDL
2 -
education
1 -
Education and Training
1 -
Education Services
1 -
Educational Services
1 -
Effective Routing
1 -
Endpoint
1 -
export
1 -
failover
1 -
FAQ
1 -
file upload
1 -
Filtering
2 -
Firewall
2 -
Firewall VM-Series
2 -
Focused Services
3 -
Focused Services Proactive Insights
2 -
gateway
1 -
Gateway Load Balancer
2 -
GCP
2 -
GCP Firewall
1 -
geolocation
1 -
Getting Started
1 -
GitHub
1 -
Global Protect
1 -
Global Protect Cookies
1 -
GlobalProtect
7 -
GlobalProtect App
1 -
globalprotect gateway
1 -
GlobalProtect Portal
2 -
google
2 -
Google Cloud
3 -
google cloud platform
2 -
Hardware
2 -
Header Insertion
1 -
High Availability
1 -
How to
1 -
HTTP
1 -
https
1 -
Hybrid Cloud
1 -
ike
3 -
import
1 -
Installation & Upgrade
1 -
IoT
1 -
IPSec
4 -
IPSec VPN Administration
1 -
kerberos
1 -
Layer 2
1 -
Layer 3
1 -
Learning
1 -
licenses
1 -
local user
3 -
Log Cluster Design
1 -
Log Collection
3 -
Log Collector Design
2 -
Logging
1 -
login
1 -
Logs
3 -
Management
8 -
Management & Administration
5 -
MFA
1 -
Microsoft
1 -
Microsoft 365
1 -
Migration
1 -
minemeld
4 -
multi factor authentication
1 -
multi-factor authentication
1 -
multi-vsys
1 -
NAT
1 -
NetSec
1 -
NetSec Newsletter
1 -
Network Security
34 -
Network Security Management
1 -
network-security
1 -
Networking
1 -
newsletter
2 -
Next Generation Firewall
4 -
Next-Generation Firewall
42 -
next-generation firewall. network security
1 -
Next-Generation Firewall. NGFW
6 -
NGFW
30 -
NGFW Configuration
11 -
NGFW Newsletter
1 -
Nominated Discussion
1 -
Objects
2 -
OTP
1 -
PA-3200 Series
1 -
PA-400
1 -
pa-440
2 -
PA-5400 series
1 -
PA-800 Series
1 -
pa-820 firewall
1 -
Packet Buffer
1 -
packet debug
1 -
packet diag
1 -
PAN-OS
16 -
PAN-OS 10.2
1 -
PAN-OS 11.0
1 -
PAN-OS Prisma Access
1 -
Panorama
11 -
Panorama Configuration
2 -
PBF
1 -
PCNSA
1 -
PCNSE
1 -
performance
2 -
policies
2 -
policy
3 -
Policy Based Forwarding
1 -
Prisma Access
5 -
Prisma AIRS
1 -
Prisma SD-WAN
1 -
proactive insights
2 -
Radius
1 -
Ransomware
1 -
region
1 -
Registration
1 -
reporting and logging
1 -
RestAPI
1 -
Risk Management
1 -
Routing
1 -
SAML
1 -
SASE
1 -
script
2 -
SD WAN
1 -
SDWAN
1 -
Search
1 -
Security Advisory
1 -
Security automation
1 -
security policy
4 -
security profile
1 -
Security Profiles
2 -
Selective Push
1 -
Session Packet
1 -
Setup & Administration
8 -
Site-to-Site VPN
1 -
Split Tunneling
2 -
SSL
1 -
SSL Decryption
2 -
SSL Forward Proxy
1 -
SSO
1 -
Strata Cloud Manager
1 -
Strata Logging Service
2 -
Support Guidance
1 -
syslog
1 -
system modes
1 -
Tag
2 -
tags
2 -
Terraform
2 -
Threat
1 -
threat log
1 -
Threat Prevention
1 -
Threat Prevention License
1 -
Tips & Tricks
1 -
TLS
1 -
traffic_log
1 -
Traps
1 -
Troubleshoot
2 -
Troubleshoot. logs
1 -
Troubleshooting
6 -
tunnel
2 -
Tutorial
2 -
Unified Monitoring
1 -
upgrade
1 -
upgrade-downgrade
2 -
url categories
1 -
URL Filtering
2 -
URL-Filtering
1 -
User ID Probing
1 -
User-ID
1 -
User-ID & Authentication
1 -
User-ID mapping
1 -
userid
1 -
VM Series
1 -
VM-Series
7 -
VM-Series on AWS
3 -
VM-Series on GCP
2 -
VPC Flow logs
1 -
VPN
3 -
VPNs
4 -
Vulnerability
2 -
Vulnerability Protection
1 -
WildFire
2 -
Wildfire License
1 -
wmi
1 -
XDR
1 -
xml
2 -
XML API
2
- Previous
- Next





