This article is based on a discussion, "IPSEC Tunnel to ASA". Read on to see the solution!
I am setting up an IPSec tunnel to an ASA. I am getting an error message about the PEERID type only allowing IP but receiving FQDN. Per the other KB article, I changed the PAN Exchange mode to Aggressive.
Now the PAN received an FQDN of the ASA side and gave listed the FQDN in the system logs.
My question.. where in the ASA can you configure PEER and LOCAL ID in the Phase1 settings? I am not seeing that option so I cannot figure out how the PAN is getting the FQDN.
Accepted Solution:
- Configure PA Firewall (Network > IKE Gateways > Configure IKE Gateway), as in the example below. Ensure that the Local and Peer Identification match with the Cisco Router.
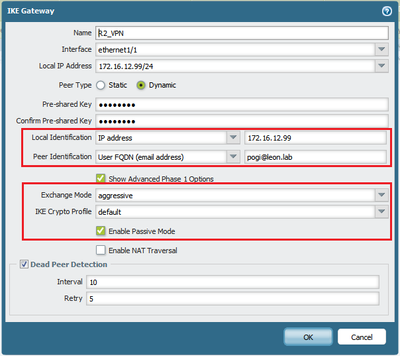
Note: Use Aggressive Exchange Mode and Enable Passive Mode if the other end is a Dynamic IP. Choose a local and peer Identification for IKE phase 1 and match this to the Cisco Router Configuration.
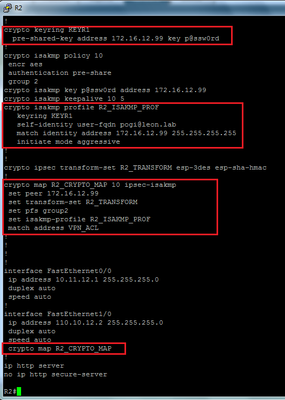
- With the Cisco router in VTI mode, configure IKE Gateway (see example below). Again, ensure that the Local and Peer Identification match with the Palo Alto Networks firewall.

With the Cisco router in equivalent Crypto Map mode, configure IKE Gateway (see example below).
owner: jlunario







