- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Tips & Tricks: SSL Forward Proxy
- LIVEcommunity
- Articles
- General Articles
- Tips & Tricks: SSL Forward Proxy
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
In today's digital world, where encryption is all around us, SSL decryption becomes a real superhero in the fight against hidden threats and bolstering network security. Luckily, Palo Alto Networks Next-Generation Firewall comes to the rescue with its powerful SSL decryption capabilities. With these tools, organizations can gain insight into encrypted traffic, spot potential risks, and take proactive measures to keep their network safe and sound. In this Tips & Tricks, I'm going to walk you through the steps of enabling SSL inbound decryption. Let's dive in!
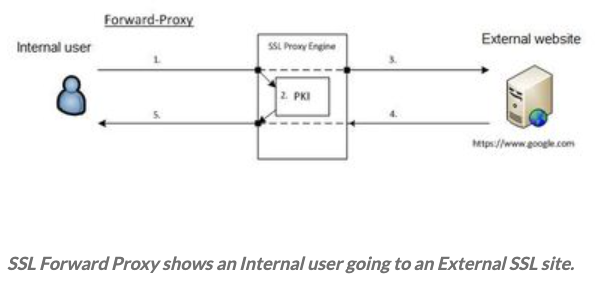
In Forward-Proxy mode, PAN-OS will intercept outbound SSL traffic matched to a decryption policy. The firewall acts as a proxy (Man In The Middle) initiating an SSL session with the destination server. During this process, the firewall presents a certificate signed by an Enterprise CA or third-party CA.
Configuring SSL Forward Proxy
-
Generate or import SSL/TLS certificates:
- Generate a self-signed certificate or import a trusted third-party certificate for SSL decryption. You can import certificates under Device > Certificate Management > Certificates.
Note: If you are using a certificate signed by a third-party CA, will have to import the public AND private key (Key Pair).
-
Configure decryption policies:
- Go to Policies > Decryption.
- Click on the "Add" button to create a new decryption policy.
- Define the decryption policy based on source and destination zones, addresses, applications, and users.
-
Set up SSL decryption profiles:
- Under Policies > Decryption, click on "SSL Decryption Profiles."
- Click on the "Add" button to create a new SSL decryption profile.
- Configure settings such as SSL protocol versions, encryption ciphers, certificate selection, and authentication requirements.
-
Configure SSL decryption rules:
- Under Policies > Decryption, click on "SSL Decryption Rules."
- Click on the "Add" button to create a new SSL decryption rule.
- Define the rule conditions based on source and destination zones, addresses, applications, or users.
- Select the SSL decryption profile you created in the previous step.
-
Enable SSL decryption on security policies:
- Under Policies > Security, select the security policy that you want to enable SSL decryption for.
- Click on the "Actions" tab.
- Enable the "Decryption" option and select the SSL decryption rule you created.
-
Fine-tune SSL decryption settings:
- Under Device > Setup > Content-ID > SSL Decryption Settings, you can configure additional SSL decryption settings.
- Customize options such as exclusions for specific websites or applications, trusted root CA certificates, or revocation checking options.
-
Monitor and troubleshoot:
- Monitor the firewall logs and review the decrypted traffic logs to ensure that the SSL decryption process is functioning correctly.
- Use the SSL Decryption Logs to view detailed information about decrypted SSL sessions and any potential issues.
There you have it! With SSL decryption on your side, you'll be proactive in protecting your network, detecting potential risks, and keeping your organization safe from ever-evolving cyber threats. Stay vigilant and protect yourself online!
Thanks for reading! @JayGolf out.
@JayGolf , do you know if the SSL Forward Trust cert can be from public CA such as GoDaddy? Or it can only be self-signed and Enterprise CA? Thank you in advance.
On 10.2.x and cannot find this setting. Has this moved?
Fine-tune SSL decryption settings:
- Under Device > Setup > Content-ID > SSL Decryption Settings, you can configure additional SSL decryption settings.
- Customize options such as exclusions for specific websites or applications, trusted root CA certificates, or revocation checking options.
If you have 2 Forward trust certs, how do you select. The example is we have a current CA that is going to be shutdown (Win2012) and use a new CA (2022) and want to tell the PA to use the new Forward Trust Cert.
- 13026 Views
- 4 comments
- 2 Likes
- Tips & Tricks: Palo Alto Global Counters for Layer 1 to Layer 4 issues troubleshooting like MTU and DOS in General Articles
- Why It's Essential to Secure Your Management Interface in General Articles
- Support FAQ: SSL Decryption in Support FAQ
- Support FAQ: How to Handle High Data Plane CPU Issues in Support FAQ
- Nominated Discussion: SSL Forward Proxy with Real Certificate in General Articles
-
"Address Objects"
1 -
10.0
1 -
10.1
1 -
10.2
2 -
ACC
1 -
Active-Passive
1 -
AD
1 -
address objects
1 -
admin roles
1 -
Administration
6 -
Administrator Profile
1 -
ADNS
1 -
Advanced DNS Security
1 -
Advanced URL Filtering
2 -
Advanced WildFire
1 -
AI
2 -
AI Security
1 -
AI Threat
1 -
AIOPS
1 -
Ansible
1 -
antivirus
1 -
API
1 -
App-ID
1 -
applications
2 -
APS
1 -
Artificial Intelligence
1 -
Asset Management
1 -
Authentication
6 -
Authentication Profile
1 -
Authentication Sequence
1 -
automatically acquire commit lock
1 -
Automation
3 -
aws
3 -
Basic Configuration
4 -
Beacon
1 -
Best Practices
6 -
Block List
1 -
categories
1 -
certificates
1 -
Certification
1 -
Certifications
1 -
Certifications & Exams
1 -
CLI
5 -
CLI command
3 -
Cloud Automation
1 -
Cloud Identity Engine
1 -
cloud ngfw
1 -
cloud security
1 -
Collector Group
1 -
Commit and Push
1 -
Commit Process
1 -
Configuration
8 -
Configuration and Management
3 -
Configure Next Generation Firewall
1 -
console
1 -
Cortex
1 -
Cortex Data Lake
2 -
Cortex XDR
3 -
CPSP
1 -
Custom Signatures
3 -
cyber elite
1 -
cyberelite
11 -
Cybersecurity
1 -
dag
1 -
DDoS
1 -
Debug
1 -
debugging
2 -
Default Policy
1 -
discussions
1 -
DLP
1 -
EDL
2 -
education
1 -
Education and Training
1 -
Education Services
1 -
Educational Services
1 -
Effective Routing
1 -
End to End Encryption
1 -
Endpoint
1 -
export
1 -
failover
1 -
FAQ
1 -
file upload
1 -
Filtering
2 -
Firewall
2 -
Firewall VM-Series
2 -
Focused Services
3 -
Focused Services Proactive Insights
2 -
gateway
1 -
Gateway Load Balancer
2 -
GCP
2 -
GCP Firewall
1 -
geolocation
1 -
Getting Started
1 -
GitHub
1 -
Global Protect
1 -
Global Protect Cookies
1 -
GlobalProtect
7 -
GlobalProtect App
1 -
globalprotect gateway
1 -
GlobalProtect Portal
2 -
google
2 -
Google Cloud
3 -
google cloud platform
2 -
Hardware
2 -
Header Insertion
1 -
High Availability
1 -
How to
1 -
HTTP
1 -
https
1 -
Hybrid Cloud
1 -
ike
3 -
import
1 -
Installation & Upgrade
1 -
IoT
1 -
IPSec
4 -
IPSec VPN Administration
1 -
kerberos
1 -
Layer 2
1 -
Layer 3
1 -
Learning
1 -
licenses
1 -
local user
3 -
Log Cluster Design
1 -
Log Collection
3 -
Log Collector Design
2 -
Logging
1 -
login
1 -
Logs
3 -
Management
8 -
Management & Administration
5 -
MFA
1 -
Microsoft
1 -
Microsoft 365
1 -
Migration
1 -
minemeld
4 -
multi factor authentication
1 -
multi-factor authentication
1 -
multi-vsys
1 -
NAT
1 -
NetSec
1 -
NetSec Newsletter
1 -
network security
34 -
Network Security Management
1 -
Network-Security
1 -
Networking
1 -
newsletter
2 -
Next Generation Firewall
4 -
Next-Generation Firewall
42 -
next-generation firewall. network security
1 -
Next-Generation Firewall. NGFW
6 -
NGFW
30 -
NGFW Configuration
11 -
NGFW Newsletter
1 -
Nominated Discussion
1 -
Objects
2 -
OTP
1 -
PA-3200 Series
1 -
PA-400
1 -
pa-440
2 -
PA-5400 series
1 -
PA-800 Series
1 -
pa-820 firewall
1 -
Packet Buffer
1 -
packet debug
1 -
packet diag
1 -
PAN-OS
16 -
PAN-OS 10.2
1 -
PAN-OS 11.0
1 -
PAN-OS Prisma Access
1 -
Panorama
11 -
Panorama Configuration
2 -
PBF
1 -
PCNSA
1 -
PCNSE
1 -
performance
2 -
policies
2 -
policy
3 -
Policy Based Forwarding
1 -
Prisma Access
7 -
Prisma AIRS
1 -
Prisma SASE
2 -
Prisma SD-WAN
1 -
proactive insights
2 -
Prompt Poaching
1 -
Radius
1 -
Ransomware
1 -
RBI
2 -
region
1 -
Registration
1 -
Remote Browser Isolation
3 -
reporting and logging
1 -
RestAPI
1 -
Risk Management
1 -
Routing
1 -
SAML
1 -
SASE
1 -
script
2 -
SD WAN
1 -
SDWAN
1 -
Search
1 -
Security Advisory
1 -
Security automation
1 -
security policy
4 -
security profile
1 -
Security Profiles
2 -
Selective Push
1 -
Session Packet
1 -
Setup & Administration
8 -
Site-to-Site VPN
1 -
Split Tunneling
2 -
SSL
1 -
SSL Decryption
2 -
SSL Forward Proxy
1 -
SSO
1 -
Strata Cloud Manager
1 -
Strata Logging Service
2 -
Support Guidance
1 -
syslog
1 -
system modes
1 -
Tag
2 -
tags
2 -
Terraform
2 -
Threat
1 -
threat log
1 -
Threat Prevention
1 -
Threat Prevention License
1 -
Tips & Tricks
1 -
TLS
1 -
traffic_log
1 -
Traps
1 -
Troubleshoot
2 -
Troubleshoot. logs
1 -
Troubleshooting
6 -
tunnel
2 -
Tutorial
2 -
Unified Monitoring
1 -
upgrade
1 -
upgrade-downgrade
2 -
url categories
1 -
URL Filtering
2 -
URL-Filtering
1 -
User ID Probing
1 -
User-ID
1 -
User-ID & Authentication
1 -
User-ID mapping
1 -
userid
1 -
VM Series
1 -
VM-Series
7 -
VM-Series on AWS
3 -
VM-Series on GCP
2 -
VPC Flow logs
1 -
VPN
3 -
VPNs
4 -
Vulnerability
2 -
Vulnerability Protection
1 -
WhatsApp
1 -
WildFire
2 -
Wildfire License
1 -
wmi
1 -
XDR
1 -
xml
2 -
XML API
2
- Previous
- Next