- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
XDR Isolation Exceptions and Exclusions Use Case
- LIVEcommunity
- Articles
- General Articles
- XDR Isolation Exceptions and Exclusions Use Case
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-12-2022 08:39 AM - edited 11-22-2022 05:37 AM
When you isolate an endpoint, you halt all endpoint network access — except for traffic to Cortex XDR. This can prevent a compromised endpoint from communicating with other endpoints, which reduces an attacker’s mobility. After the Cortex XDR agent receives the instruction to isolate the endpoint and carries out the action, the Cortex XDR console shows an isolated check-in status. To ensure an endpoint remains in isolation, agent upgrades are not available for isolated endpoints.
Traffic to Cortex XDR can be halted in some cases. For example, enabling the GlobalProtect feature “Enforce Global Protect for Network Access” will block ALL traffic on GlobalProtect clients until the GlobalProtect agent is internal or connects to an external gateway. Forcing users to connect to GlobalProtect to access the network reduces the security risks of exposing your enterprise to endpoints who aren’t connected via VPN. In this case, to ensure communication to Cortex XDR is always allowed, an IP or FQDN exclusion can be made for the XDR cloud. As best practice, it is recommended to create FQDN exclusions because domain names do not change as often as IP addresses do
The IP address and FQDN names used by the XDR service can be found on Resources Required to Enable Access to Cortex XDR; find out more about the enforce option in the resources list at the bottom of this article.
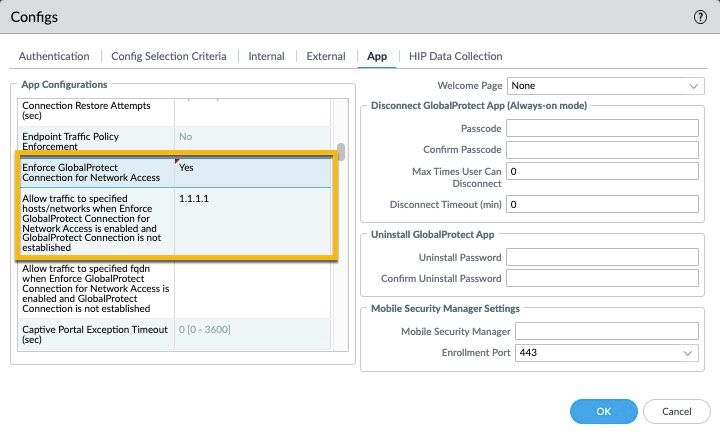
Still, if the FQDN exclusions are configured, then the process (the native operational system DNS process or custom agent specific process) that the VPN agent uses for the DNS resolution should also not be isolated by the XDR system as when the VPN agent can’t resolve a DNS/FQDN domain name then it can not be excluded and this is where ” Network isolation allow list ” comes into play.
A quick note is that with DNS FQDN exclusions better to use the Palo Alto DNS Proxy feature where your clients will use the Palo Alto as local DNS resolver as it is possible that the client's DNS to resolve differently the FQDN name than the Firewall as inteligent DNS services can do this.
This feature is located under the “Agent Settings Profile” and allows a process and destination IP address to not be blocked during isolation and for an IP address also a wildcard can be configured. Sometimes a process may use another process for DNS resolution, so it should be checked which is the final process that does the DNS resolution for the VPN agent.
Windows and Mac Response Actions
If you need to isolate an endpoint but want to allow access for a specific application, add the process to the
Network Isolation Allow List . The following are considerations to the allow list:
- When you add a specific application to your allow list from network isolation, the Cortex XDR agent continues to block some internal system processes. This is because some applications, for example ping.exe, can use other processes to facilitate network communication. As a result, if the Cortex XDR agent continues to block an application you included in your allow list, you may need to perform additional network monitoring to determine the process that facilitates the communication, and then add that process to the allow list.
- (Windows) For VDI sessions, using the network isolation response action can disrupt communication with the VDI host management system thereby halting access to the VDI session. As a result, before using the response action you must add the VDI processes and corresponding IP addresses to your allow list.
- Add an entry to the allow list
- Specify the Process Path you want to allow and the IPv4 or IPv6 address of the endpoint. Use the * wildcard on either side to match any process or IP address. For example, specify * as the process path and an IP address to allow any process to run on the isolated endpoint with that IP address. Conversely, specify * as the IP address and a specific process path to allow the process to run on any isolated endpoint that receives this profile.
- Click the check mark when finished.
This is a really helpfull XDR feature as many other EDR and Endpoint Security solutions when isolating the device can't exclude the VPN agent DNS resolution and this becomes a big issue. Some EDR and Endpoint Security solutions can only exclude from isolation other applications and VPN agents that are from the same vendor and this is vendor lockdown.
Just for an info I have seen this issue with another VPN agent and their feature that is like “Enforce Global Protect for Network Access” as there is a big chance that Globalprotect may use the same DNS process as the XDR agent (XDR is not going to block their own DNS resolution) or the XDR knowing that the Globalprotect DNS resolution shouldn't be blocked but I used Globalprotect as an example as in this forum I want to talk about Palo Alto stuff 🙂
RESOURCES
TechDocs: Enforce GlobalProtect Exclusions
Enforce GlobalProtect Connections with FQDN Exclusions
Global Protect Enforcer Exception List
TechDocs: Add a New Agent Settings Profile TechDocs: Cytool for Windows
How to Exclude Application and Video Traffic from the GlobalProtect VPN Tunnel*
*For the GlobalProtect split-tunnel, there is an exclusion that is based on process and this may at some point be added also for the Enforce option and then it will be much easier to just exclude the XDR process that connects to the XDR cloud console. I have seen the process exclusion option for "Enforce Global Protect for Network Access” in the Globalprotect PanGPS/PanGPA agent logs, so it should be added to some point.
- advanced endpoint protection
- Cortex
- Cortex XDR
- Cortex XDR Agent
- Cyberelite
- Dns
- endpoint
- fqdn
- GlobalProtect
- GlobalProtect Agent
- GlobalProtect client
- Pan-os
- traps
- XDR
- 11214 Views
- 0 comments
- 2 Likes
-
"Address Objects"
1 -
10.0
1 -
10.1
1 -
10.2
2 -
ACC
1 -
Active-Passive
1 -
AD
1 -
address objects
1 -
admin roles
1 -
Administration
6 -
Administrator Profile
1 -
ADNS
1 -
Advanced DNS Security
1 -
Advanced URL Filtering
2 -
Advanced WildFire
1 -
AI
2 -
AI Security
1 -
AI Threat
1 -
AIOPS
1 -
Ansible
1 -
antivirus
1 -
API
1 -
App-ID
1 -
applications
2 -
APS
1 -
Artificial Intelligence
1 -
Asset Management
1 -
Authentication
6 -
Authentication Profile
1 -
Authentication Sequence
1 -
automatically acquire commit lock
1 -
Automation
3 -
aws
3 -
Basic Configuration
4 -
Beacon
1 -
Best Practices
6 -
Block List
1 -
categories
1 -
certificates
1 -
Certification
1 -
Certifications
1 -
Certifications & Exams
1 -
CLI
5 -
CLI command
3 -
Cloud Automation
1 -
Cloud Identity Engine
1 -
cloud ngfw
1 -
cloud security
1 -
Collector Group
1 -
Commit and Push
1 -
Commit Process
1 -
Configuration
8 -
Configuration and Management
3 -
Configure Next Generation Firewall
1 -
console
1 -
Cortex
1 -
Cortex Data Lake
2 -
Cortex XDR
3 -
CPSP
1 -
Custom Signatures
3 -
cyber elite
1 -
cyberelite
11 -
Cybersecurity
1 -
dag
1 -
DDoS
1 -
Debug
1 -
debugging
2 -
Default Policy
1 -
discussions
1 -
DLP
1 -
EDL
2 -
education
1 -
Education and Training
1 -
Education Services
1 -
Educational Services
1 -
Effective Routing
1 -
End to End Encryption
1 -
Endpoint
1 -
export
1 -
failover
1 -
FAQ
1 -
file upload
1 -
Filtering
2 -
Firewall
2 -
Firewall VM-Series
2 -
Focused Services
3 -
Focused Services Proactive Insights
2 -
gateway
1 -
Gateway Load Balancer
2 -
GCP
2 -
GCP Firewall
1 -
geolocation
1 -
Getting Started
1 -
GitHub
1 -
Global Protect
1 -
Global Protect Cookies
1 -
GlobalProtect
7 -
GlobalProtect App
1 -
globalprotect gateway
1 -
GlobalProtect Portal
2 -
google
2 -
Google Cloud
3 -
google cloud platform
2 -
Hardware
2 -
Header Insertion
1 -
High Availability
1 -
How to
1 -
HTTP
1 -
https
1 -
Hybrid Cloud
1 -
ike
3 -
import
1 -
Installation & Upgrade
1 -
IoT
1 -
IPSec
4 -
IPSec VPN Administration
1 -
kerberos
1 -
Layer 2
1 -
Layer 3
1 -
Learning
1 -
licenses
1 -
local user
3 -
Log Cluster Design
1 -
Log Collection
3 -
Log Collector Design
2 -
Logging
1 -
login
1 -
Logs
3 -
Management
8 -
Management & Administration
5 -
MFA
1 -
Microsoft
1 -
Microsoft 365
1 -
Migration
1 -
minemeld
4 -
multi factor authentication
1 -
multi-factor authentication
1 -
multi-vsys
1 -
NAT
1 -
NetSec
1 -
NetSec Newsletter
1 -
network security
34 -
Network Security Management
1 -
Network-Security
1 -
Networking
1 -
newsletter
2 -
Next Generation Firewall
4 -
Next-Generation Firewall
42 -
next-generation firewall. network security
1 -
Next-Generation Firewall. NGFW
6 -
NGFW
30 -
NGFW Configuration
11 -
NGFW Newsletter
1 -
Nominated Discussion
1 -
Objects
2 -
OTP
1 -
PA-3200 Series
1 -
PA-400
1 -
pa-440
2 -
PA-5400 series
1 -
PA-800 Series
1 -
pa-820 firewall
1 -
Packet Buffer
1 -
packet debug
1 -
packet diag
1 -
PAN-OS
16 -
PAN-OS 10.2
1 -
PAN-OS 11.0
1 -
PAN-OS Prisma Access
1 -
Panorama
11 -
Panorama Configuration
2 -
PBF
1 -
PCNSA
1 -
PCNSE
1 -
performance
2 -
policies
2 -
policy
3 -
Policy Based Forwarding
1 -
Prisma Access
7 -
Prisma AIRS
1 -
Prisma SASE
2 -
Prisma SD-WAN
1 -
proactive insights
2 -
Prompt Poaching
1 -
Radius
1 -
Ransomware
1 -
RBI
2 -
region
1 -
Registration
1 -
Remote Browser Isolation
3 -
reporting and logging
1 -
RestAPI
1 -
Risk Management
1 -
Routing
1 -
SAML
1 -
SASE
1 -
script
2 -
SD WAN
1 -
SDWAN
1 -
Search
1 -
Security Advisory
1 -
Security automation
1 -
security policy
4 -
security profile
1 -
Security Profiles
2 -
Selective Push
1 -
Session Packet
1 -
Setup & Administration
8 -
Site-to-Site VPN
1 -
Split Tunneling
2 -
SSL
1 -
SSL Decryption
2 -
SSL Forward Proxy
1 -
SSO
1 -
Strata Cloud Manager
1 -
Strata Logging Service
2 -
Support Guidance
1 -
syslog
1 -
system modes
1 -
Tag
2 -
tags
2 -
Terraform
2 -
Threat
1 -
threat log
1 -
Threat Prevention
1 -
Threat Prevention License
1 -
Tips & Tricks
1 -
TLS
1 -
traffic_log
1 -
Traps
1 -
Troubleshoot
2 -
Troubleshoot. logs
1 -
Troubleshooting
6 -
tunnel
2 -
Tutorial
2 -
Unified Monitoring
1 -
upgrade
1 -
upgrade-downgrade
2 -
url categories
1 -
URL Filtering
2 -
URL-Filtering
1 -
User ID Probing
1 -
User-ID
1 -
User-ID & Authentication
1 -
User-ID mapping
1 -
userid
1 -
VM Series
1 -
VM-Series
7 -
VM-Series on AWS
3 -
VM-Series on GCP
2 -
VPC Flow logs
1 -
VPN
3 -
VPNs
4 -
Vulnerability
2 -
Vulnerability Protection
1 -
WhatsApp
1 -
WildFire
2 -
Wildfire License
1 -
wmi
1 -
XDR
1 -
xml
2 -
XML API
2
- Previous
- Next





