- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Active directory OU as selection for users security policy
- LIVEcommunity
- Discussions
- General Topics
- Re: Active directory OU as selection for users security policy
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-08-2021 08:43 AM
Hello all
I am new in Palo Alto devices and PanOS, so here is my questions.
Is there a way to select an active directory OU as a source user in a security policy?
(Or something else to manage it)
Working with Forcepoint they apply policies to a whole OU (and also users and groups)
Thanks in advanced
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-08-2021 03:10 PM
Thank you @ChrisKarakostas for posting question.
To my knowledge it is not possible. In the security policy, you can use only AD Groups or Users.
Here is the link for Documentation: https://docs.paloaltonetworks.com/pan-os/10-1/pan-os-admin/user-id/map-users-to-groups.html You can configure the Base-DN in LDAP profile for entire AD Domain, however when you configure Group Mapping Setting only Group Objects and User Objects are available and this is what you will end up using as source user in a security policy.
If you are setting this up for the first time from scratch, below are a few KBs for reference:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClXWCA0
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClGOCA0
Note: After you complete the LDAP profile and Group Mapping Setting with user/group include list, you will have to commit it first before you can select user/group as a source in the security policy.
If you get stuck with the setup do not hesitate to post your problem here, I will do my best to help.
Kind Regards
Pavel
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-11-2021 03:09 AM - edited 09-11-2021 03:10 AM
Thank you for quick reply @ChrisKarakostas
I see. There might be other way around it, but probably the easiest one might be to configure your firewall to fetch IP addresses from EDL Hosting Service and configure this EDL as a destination in the policy you just created. Below links are covering more details:
https://docs.paloaltonetworks.com/resources/edl-hosting-service.html
The actual process to configure it should be straight forward:
1. Import relevant certificates and configure EDL itself: https://docs.paloaltonetworks.com/pan-os/10-0/pan-os-admin/policy/use-an-external-dynamic-list-in-po...
2. Add EDL to security policy as a destination and remove destination any.
Kind Regards
Pavel
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-08-2021 03:10 PM
Thank you @ChrisKarakostas for posting question.
To my knowledge it is not possible. In the security policy, you can use only AD Groups or Users.
Here is the link for Documentation: https://docs.paloaltonetworks.com/pan-os/10-1/pan-os-admin/user-id/map-users-to-groups.html You can configure the Base-DN in LDAP profile for entire AD Domain, however when you configure Group Mapping Setting only Group Objects and User Objects are available and this is what you will end up using as source user in a security policy.
If you are setting this up for the first time from scratch, below are a few KBs for reference:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClXWCA0
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClGOCA0
Note: After you complete the LDAP profile and Group Mapping Setting with user/group include list, you will have to commit it first before you can select user/group as a source in the security policy.
If you get stuck with the setup do not hesitate to post your problem here, I will do my best to help.
Kind Regards
Pavel
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-11-2021 12:52 AM
Ok , it is clear for the user-group selection.
Now let me ask for another subject.
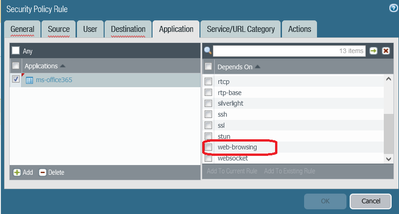
I'm trying to create a security rule to permit only microsoft365 appications, and nothing else for a specific group of users.
I choose the relevant app-id with their depentencies , application-default in services,action allow, but that policy permits also every web browsing traffic.
No other policies ,except the default implicit ones
Where am i wrong
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-11-2021 01:50 AM
Thank you @ChrisKarakostas for the update.
My best guess is following, if you have added the application: ms-office-365, then one of the dependency is: web-browsing. By adding this dependency, you have also enabled web browsing traffic:
Kind Regards
Pavel
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-11-2021 02:16 AM
I added it.
But my problem is that i DON'T want further internet browsing except microsoft365
With my policy , internet browsing if permitted at all
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-11-2021 03:09 AM - edited 09-11-2021 03:10 AM
Thank you for quick reply @ChrisKarakostas
I see. There might be other way around it, but probably the easiest one might be to configure your firewall to fetch IP addresses from EDL Hosting Service and configure this EDL as a destination in the policy you just created. Below links are covering more details:
https://docs.paloaltonetworks.com/resources/edl-hosting-service.html
The actual process to configure it should be straight forward:
1. Import relevant certificates and configure EDL itself: https://docs.paloaltonetworks.com/pan-os/10-0/pan-os-admin/policy/use-an-external-dynamic-list-in-po...
2. Add EDL to security policy as a destination and remove destination any.
Kind Regards
Pavel
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-11-2021 10:16 AM
It works.
Thanks again PavelK
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-13-2021 01:19 AM
Hi @ChrisKarakostas ,
Regarding the Goup Mapping, @PavelK already provided excelent answer, to which I wanted to add:
You can check the "Custom Group" feature, which allowes you to create LDAP filter, based on which firewall will create user group that can be referenced in a rule - https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClJ1CAK
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-13-2021 05:29 AM
That's very helpfull
Thanks Astardzhiev
- 2 accepted solutions
- 10552 Views
- 8 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- GlobalProtect Agent constantly 'Not Responding'. in GlobalProtect Discussions
- CIE for user/group mapping for firewall on-premise in General Topics
- SHOW ALL ALERT in Cortex XDR Discussions
- Difficulty in Displaying Unused Firewall policies in PA networks using API key in Next-Generation Firewall Discussions
- Usergroup in Panorama Discussions