- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Aggregation interface on virtual wire
- LIVEcommunity
- Discussions
- General Topics
- Aggregation interface on virtual wire
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Aggregation interface on virtual wire
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-18-2015 02:09 PM
Hello All,
Is there supported to create virtual wire aggregate group ae1 with 3 physical interfaces and another ae2 with another 3 physical interfaces, then form virtual wire with ae1 and ae2. Point of this setup is to put PA between two switches with port channel group formed with 3 physical interfaces.
Regards,
Predrag
- Labels:
-
Networking
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-19-2015 02:48 AM
This tech note outlines the process for a two interface bundle, but the same procedure can be used for three. Naturally, the two AE will be separate v-wires but you can put them into the same zones.
Cisco Link Aggregation Traffic Through a Palo Alto Networks Device
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-19-2015 07:44 AM
This doc is good, but I considering case where trunk with multiple vlan's are deployed a cross port channel. If you don't aggregate this links on pan, that's mean that you need deploy two vwire interfaces from one switch to same security zone. But how can I make policies to secure traffic between two vlan's on this particular formed vwire. Should I create subinterfaces with vlan tag membership, or just make policies by source and destination IP, users and so on...?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-19-2015 01:53 PM
If I understand you correctly, your AE bundle is also a Q tag trunk port. In that case you simply create the subinterfaces on the AE interface and match the tags.
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-20-2015 04:26 AM
Ok, just clarify what I want to do.
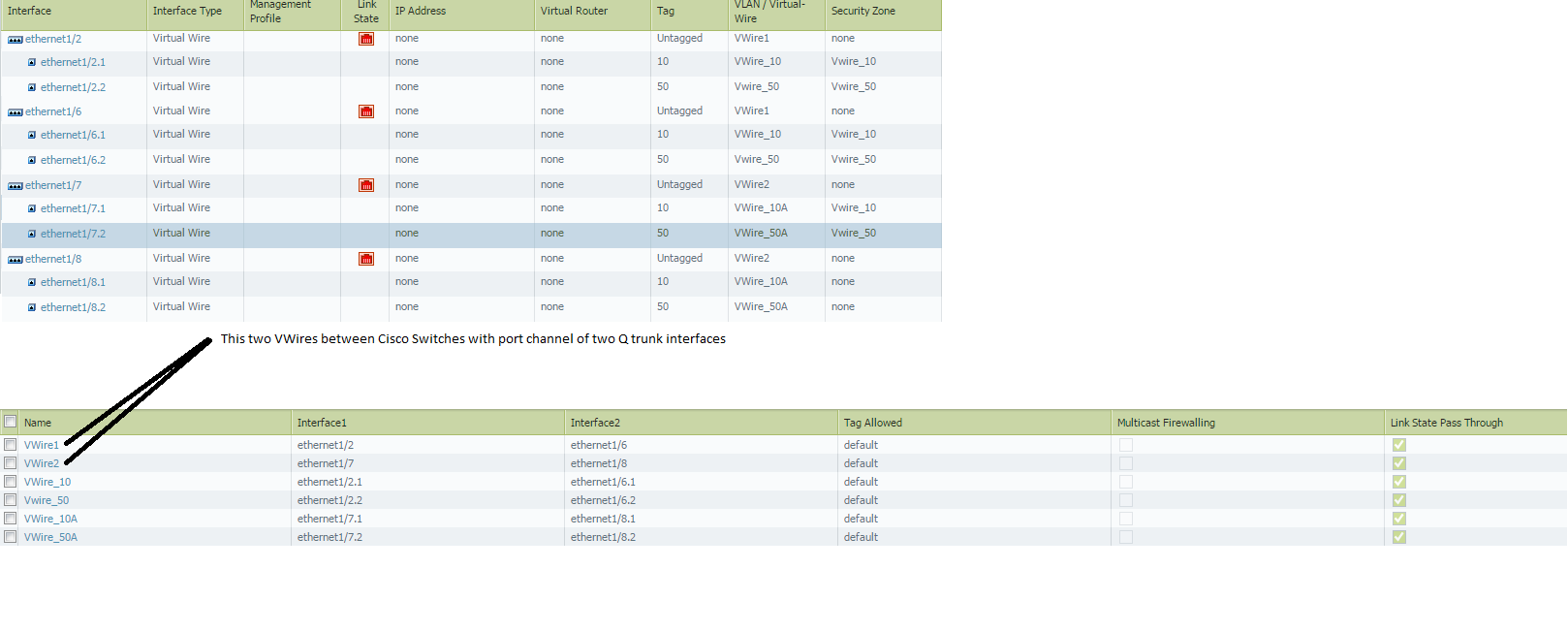
To put PAN between two Cisco switches with Q trunk formed on port channel with two physical port. So I configured two physical VWires without aggregation and corresponded vlan subinterfaces with vlan tag respectively. Then I create Vwires interfaces of same vlan's. Then new created vwire side subs in same vlan, put on same security zone eg. Vwire_10 zone. On second physical Vwire I need to create same vlan subs and put them on corresponded sec zone eg. Vwire_10. On that point I create security policies to secure traffic between vlan's (eg. Vwire_10 to Vwire_50). Maybe picture below is better to help understand this setup than I could explain...
I have no enough resources to test this and I'm concerned whether is this recommended scenario or not, when we talk about Vwire setup on trunk link's with aggregated interfaces on switches?
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-12-2022 05:56 AM
for this case I recommend to use layer 2 interface because vwire is only for physical interface and aggregate interface. You can improve on the following solutions:
https://live.paloaltonetworks.com/t5/general-topics/palo-alto-layer-2-bridging/m-p/388782#M90540
- 8566 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- PA-415-5G not working with fresh T-Mobile SIM in General Topics
- GloablProtect + Explicit Proxy blocks WSL traffic. in Prisma Access Discussions
- GRPC status UNAVAILABLE in intelligent offload in VM-Series in the Private Cloud
- Trying the DNSProxy feature for Static Response in General Topics
- How does the Azure Virtual Network discovers that there is Palo Alto Gateway Interface in VM-Series in the Public Cloud



