- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
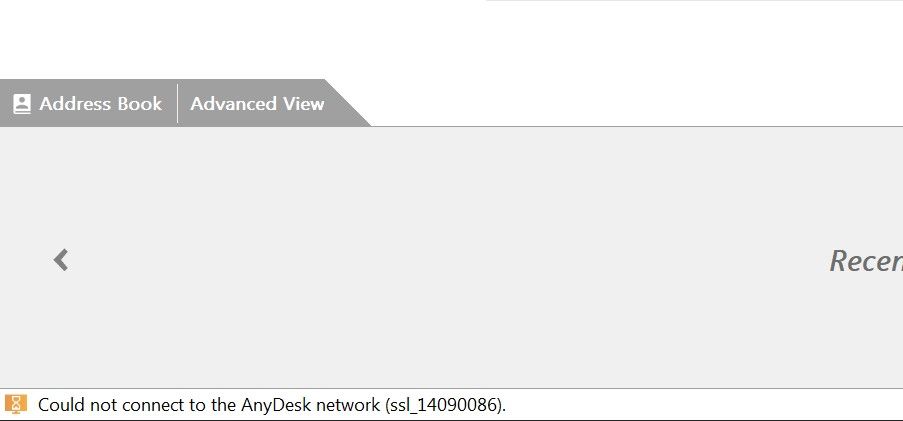
Anydesk issue.
- LIVEcommunity
- Discussions
- General Topics
- Anydesk issue.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Anydesk issue.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-04-2018 10:43 PM
Hi everyone!
I have some issues with anydesk application. It has ssl issue because of decryption, I think.
I've added *.anydesk.com ind 'SSL decryption exclusion', but it didn't worked.
Maybe some of you have faced such kind of issue?
Thanks in advance!
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-26-2020 02:44 AM
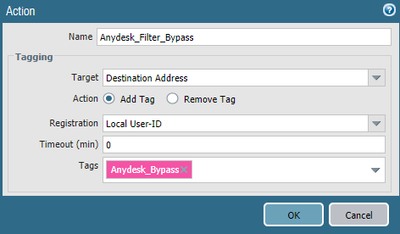
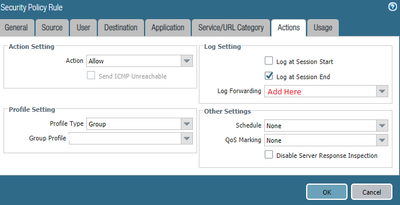
OK got this working for now but not exactly the way I want.
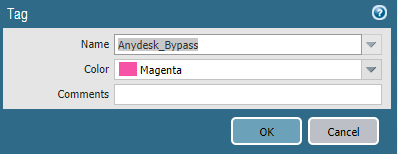
1) Tag
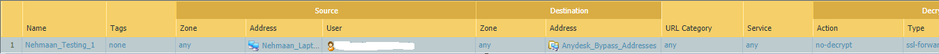
2) Address Group
3) SSL Decryption Policy
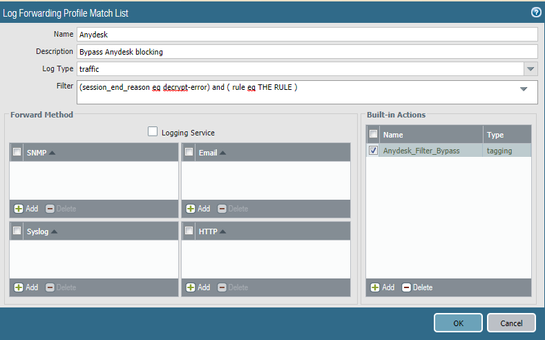
4) Log Forwarding
5) Built-in Actions
6) Security Rule
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-26-2020 02:58 AM - edited 02-26-2020 03:00 AM
Hello, guys!
I met this issue and found out the root cause. Many of you know that desktop applications often check certificate. Anydesk does it. So we need to exclude it from SSL decryption, but here is the trick: *.anydesk.com works only for Anydesk website (NGFW detects web-browsing application, see that URL match *.anydesk and exclude the session from decryption), but it doesn't work for the desktop application and here is why:
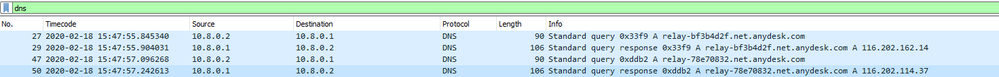
I made a little investigation and found out that the application makes DNS query for random URL, generated upon installation. (Guess it called DGA, but correct me if I wrong)
Here is an example:
Then it establishes TCP session to IP, that was previously taken from DNS Query and that's all:
So our exclusion rules will not work for IP.
Solution:
1. Go to Monitor>Traffic and filter logs by application "Anydesk".
2. Export logs to CSV and open it in Excel
3. Find Destination IP column, select all items and delete duplicates
4. Copy this list to *.txt file and create EDL.
5. Use this EDL in No-Decrypt policy
6. PROFIT!
You also can go further. According to WHOIS service - backend IP addresses are located in different DCs all over the world. You can take IPs you found in logs and find the whole IP ranges in WHOIS info and use these ranges in EDL. But it doesn't seem safe to me, because many of those IPs in IP range can be used by other applications, not Anydesk, so this is a potential risk.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-26-2020 03:13 AM
Looks cool!
But I think 6 should be after 3. Because you use the security rule name in the filter in Log Forwarding settings
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-26-2020 03:17 AM
Yes, On the assumption that the security rules doesn't exist. It does in my case.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-10-2020 01:54 AM
Could you please show me how to create a custom EDL IPv4 with Minemeld. Currently I have created and using Office365 IPv4 list but I don't know how to create a custome EDL IPv4 list with a text file as you mentioned.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-12-2020 03:51 AM
Hi!
Actually I think @Nehmaan provided a better solution to this problem. You should try it. I use it myself.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-06-2020 12:59 AM - edited 07-06-2020 01:02 AM
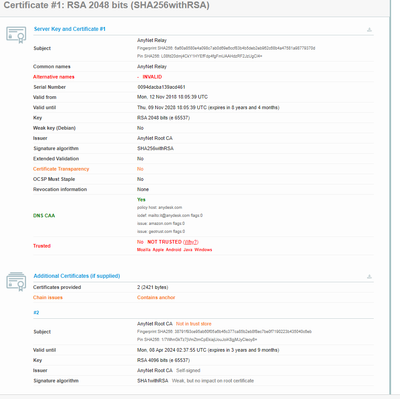
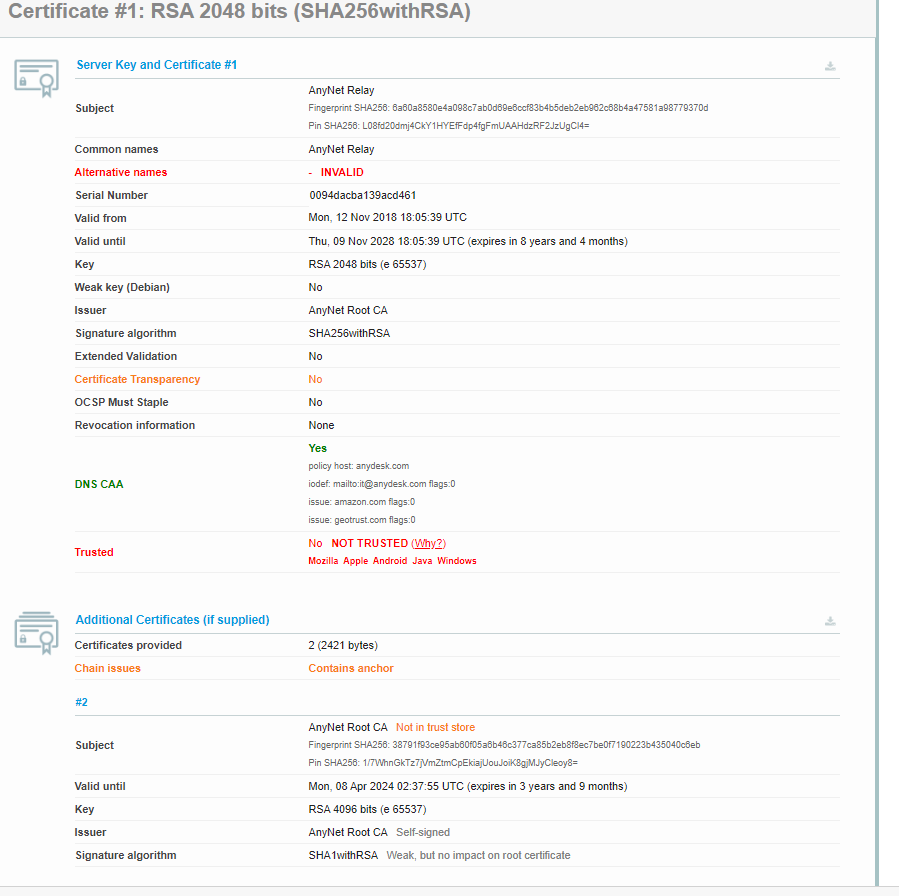
I came up with another solution. I imported the certificates these Anydesk "relay" servers use.
After some investigations, I found Anydesk was using INTERNALLY created certificates for these relays and since they are internal, there is no way the PAs will trust them. If the PA does not trust the certificate Root it WILL NOT let decryption or even no-decryption work for that site, it simply stops access to it.
I noticed in my logs, that the client kept hitting various sites of URL relay-xxxxxxx.net.anydesk.com (ie:relay-dbb2d168.net.anydesk.com). Browsing to that URL would forward you to the Anydesk site, so you couldn't get the SSL certificates it was using. To grab them I had to use https://www.ssllabs.com/ssltest/index.html then I entered the relay URL (relay-dbb2d168.net.anydesk.com) in this tool and let it run.
It returns the following certificates
The benefit of this SSL checker is that it lets you download the certificates it finds so I just downloaded both of them (AnyNet Root CA and AnyNet Relay) and imported them into my PA Certificates section. I also ticked "Trusted CA" for the AnyNet Root CA
To be 100% I also added *.net.anydesk.com into my no-decrypt policy and into the ssl-decryption-exclusion section under Certificate Management.
Here are the certificates for you to paste them into a text file and save as a .cer for import. If you wish you can use https://www.sslshopper.com/certificate-decoder.html and copy the below certificate texts to confirm they are legitimate.
AnyNet Root CA
-----BEGIN CERTIFICATE-----
MIIFYzCCA0ugAwIBAgIJAIf7DQy3sYvoMA0GCSqGSIb3DQEBBQUAMEgxFzAVBgNVBAMMDkFueU5l
dCBSb290IENBMSAwHgYDVQQKDBdwaGlsYW5kcm8gU29mdHdhcmUgR21iSDELMAkGA1UEBhMCREUw
HhcNMTQwNDExMDIzNzU1WhcNMjQwNDA4MDIzNzU1WjBIMRcwFQYDVQQDDA5BbnlOZXQgUm9vdCBD
QTEgMB4GA1UECgwXcGhpbGFuZHJvIFNvZnR3YXJlIEdtYkgxCzAJBgNVBAYTAkRFMIICIjANBgkq
hkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAtBVBDdoa01og/vnfvwqM8aSt79RUlufigrcNAOrxN+LX
jKEWO6BoCDiqbdsmvqZpkzaojh5w3KyBHuLdFoM0tRVw9YrNne5dgHxaeKIHpK7m+NYx+lx7u+Ba
61Evl7/2+zMnkLPY5ODNaDtqh2ymDefYvWHfVmsq4Rwr9Z+/hd2MWwYecX+6SqZAsHcX6iw/W5QU
hS6tEWGriPYBu7NHa+KBGPGOOebYewxjhoOscIR1Jy01PXt7qM6ySHkIOC2CJn6TSzJ2ZoWn/crx
Ci/HYg9qQP4aa1gcU+RjwXWDmqt4BEmDH+cjcJ+jv2jRMy9M3l6GmH1hfQE09Zzpy0FrrlArZ9XZ
8gL8X6NSNLncZ+/6c8WUQOq1iveY7Oibu4ZsbzY3ioCMn4T2ykp2InKNUn2FdU1V762v8+UWIwBb
6Lbtfp8ugEvu1V/cZemJ3NumQwS7zv2pTC8ZM6rmcSCG/kWLl+bIHU9wusfAw/Om8trCpBvdiU7s
HNp7JI+qQvkUMoNoY8gmvOwTsw0L4rYIxsYGfqMWbxXSGxZSPB8ikSUXFcxCgto7qDnHKlDK2Uyg
jJUzdQNwuN+gybKyixs4g3kywxLaM5ZC9JERqsYmMbzqQ4owVGXFQ55QO/qRkw6dOyNKPUPBxiKb
aK8v/AGAUhgFIg69auQuydbsxY/zE7MCAwEAAaNQME4wHQYDVR0OBBYEFBlleQaAxt6yqliZV7I2
XO0BYo1HMB8GA1UdIwQYMBaAFBlleQaAxt6yqliZV7I2XO0BYo1HMAwGA1UdEwQFMAMBAf8wDQYJ
KoZIhvcNAQEFBQADggIBALOqRxekr9JgNBWtJdWOKF7BqrGNMFabR3by4CBUBj3xI8Lvu6Hyn+Or
DAa/VF4MGjVWbeGTS8WZX5CGflKDlKCgRzby/PLCTXDJyW40XKcPBP3rFl6KvoY7oAxzf6P1Xz0r
xUEMZwrjSCvKYvapmh7J5ES8F/nbXEWYCWnsyGPvhSlOce35maxJIIqQvFmO8fOlmZkS46d75Wg0
q1NarfFEyrp/wqZzkhDqjLHGydXkXisPHkqT+W1MBoWQZVHTicwuomu15PDqNzWpfcDLhxIycpMh
UYEdowzKlviB9JKgr/cZJPPmzeoRKcnxKR2yKxgatKPAWMRwOXiniNd0MsKAYoNY47Q+JbhWLGB3
UiWqYTLRl413JDQkxdvy3WHI7WNXDsJw5R9S3WxvOLLa7Z2nL4f6s3DlZE35wwLVRtofy/BYIPxE
lvDKtps55s8n0CyZdNTK3keI7d/3nDusimLSdZDZAIHT+MJHjpq9h23O5Zp/KHakd8Y/ub9N8cvf
Dyxz/rRg4yZeg/KuNlaU6aedoT3KXW49Xahv8qWP855ohSfs6WeFNBYNRTQUjgcMeyVRVPM/oSrv
mheeUd4WZPvd4ciUCYw5u3dz1Ga7SStc+itXi2at96hwO4+eCXHeEi7tAhBM1Wcecv86PjRtkmA9
RF70IWDubC46cxrDJmr0
-----END CERTIFICATE-----
AnyNet Relay
-----BEGIN CERTIFICATE-----
MIIECjCCAfICCQCU2suhOazUYTANBgkqhkiG9w0BAQsFADBIMRcwFQYDVQQDDA5B
bnlOZXQgUm9vdCBDQTEgMB4GA1UECgwXcGhpbGFuZHJvIFNvZnR3YXJlIEdtYkgx
CzAJBgNVBAYTAkRFMB4XDTE4MTExMjE4MDUzOVoXDTI4MTEwOTE4MDUzOVowRjEL
MAkGA1UEBhMCREUxIDAeBgNVBAoMF3BoaWxhbmRybyBTb2Z0d2FyZSBHbWJIMRUw
EwYDVQQDDAxBbnlOZXQgUmVsYXkwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEK
AoIBAQC6ysgUWfAYUkJb68TFtX+MtdpN0+uCDnqnFV+kSdMhlazT3Z2WIlEeAIwk
H0KDrOJ2oUZaYo+N15CmMhu5pmlobXnPSHq4E4k6Z7NCCqLsgJFUpowCrshADFe7
BflWC3D16n0seoElsphBQNYZorlEr3TziGdVqwcjCqYu3Eyhd9akCcW94T2Is31E
Llah1xBeSoVewzoP3L7uoIjCNIYGsIgU/7SYERkdcFiZwVHI/hgQN1E0q38lbSjC
4/V4LpXwfJoEbktT7TZDOSAk9LSUHYRr43BwyPiANJKTEkCyWTv4kjfRdMAcywak
twifQbR2gYgJKpLzXTIg8CaW5NFFAgMBAAEwDQYJKoZIhvcNAQELBQADggIBAGqM
On7XkIok+ZA56KH+v/3b4ltTkaZnY+8CM/7D4gjCwbAeer5/WJBIFNCAk+FY3tym
t9CfkshsAJqL9zh9neIF1UFy+cTBeCCZ8P8GP8pPzV8/1NecAHBa+Owbj6oX9yao
SAyiw9OoFUqTBIUGvGeWmLF0cVTD4xonBo0woJ1KJKYLPCk32eyA3QdehNJlPeH5
wqASanvIQb4jQU6GXZWbzYR6SOcYg9ofRUAXXK/7cUI2Kdxrq7DGAO5IwTDEnMv/
c+cnZuRiIWbf8syiDvPrJ4valyfgxnhi12QGHjlKUPgEhsbWazEnAYqmenljKuOn
DKFOiPdfGM6ep/AncGzC5H+wHO3OIqeBLNJb/0sjEfnJuP/OCZlYC1T9SLV760cp
fgj23xUBm4JbXAf1SxuZ85urYEOguNgsaRG1BbKOOZeUA5edQHwpXaIddfTG2ke5
MvU8qcoI+Cu0nM5PUKRarNYVTflkTn9gsT/2tCbr7Lzdr+IWkuCuocnOZK3j3pBk
1I3ZWwnf5LSNE/puo+G4jeverBV8yMiGhWeFj272VvFjuyl60JK6fl+3fPm1IgCM
3ZiW/a5SZN+Xs4zK3dIzoAp1XlwSZ9l3oVr2UWh7l+aFiPxX4lS37tyjLF46tTBp
3w2M1LSWZuOgnuf4TXpPwTAVve8nLoxIpKGhQozQ
-----END CERTIFICATE-----
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-06-2020 04:23 AM
Not sure what happened to my last post, it hasn't come up (maybe because I included a certificate code) but I believe I found a quick solution.
Essentially I discovered my clients were hitting Anydesk relay sites of relay-xxxxxxx.net.anydesk.com (ie: relay-dbb2d168.net.anydesk.com). I used https://www.ssllabs.com/ssltest/index.html to check the above URL to see what certificates it was using and it's using INTERNALLY created certificates (WTF). No wonder why the PAs are denying it entirely!
NOTE: you cannot see its certificates jsut by browsing to the URL as it has an auto-forward to the Anydesk main site.
The ssllabs site lets you download the certificates it discovers, you then need to import them into your PA and mark the AnyNet Root CA as a trusted Root CA and then it will work.
I also added *.net.anydesk.com as a decryption exception.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-23-2020 04:49 AM
Adding the AnyNet Root/Relay certs resolved it for me immediately.
Great find, thanks!
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-01-2021 12:44 AM
Now it works. Thank you!!!
Claudio VERNIANI Pae
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-17-2022 02:09 AM
Anynet Relay certificate, doesn't seem to be a CA Certificate, so it cannot be marked as trusted CA once imported into Paloalto.
Anyone has this problem?
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-19-2022 04:49 AM
Same problem.
Is there a definitive solution for this?
The provided instructions are not working.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-21-2022 06:40 AM
Now it works. Thank you !
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-03-2022 03:30 AM - edited 04-23-2024 10:40 AM
Hello,
For a period of time, the solution proposed by @dcaporetto worked also for me, but starting with one month ago I start having problems with Anydesk clients. After investigation, the following solution work for my PA:
Update on April 10th, 2024:
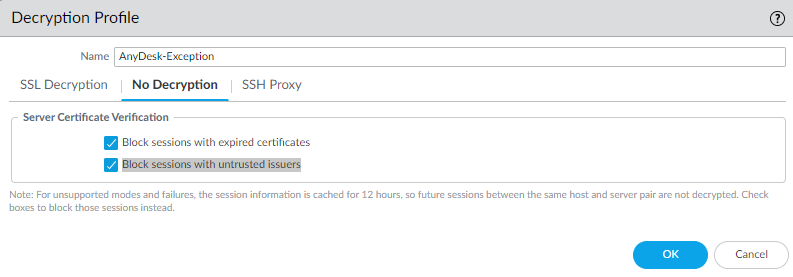
Because I saw that there is interest in managing Anydesk traffic through the Palo Alto Networks firewall and the changes from April 2024, I decided to update this. In fact, at least one change in the decryption profile is necessary, that is, to stop verifying the issuer of the certificate because we have no way until we can obtain the new AnyDesk Root CA 2 certificate.
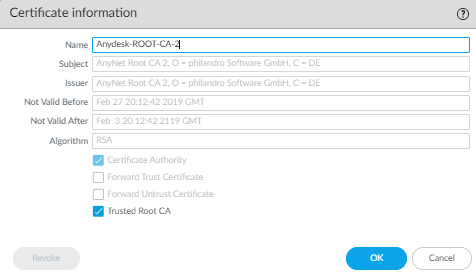
Update 2 on April 10th, 2024: (a big Thank You! for @S-Battermann, because we have now the new AnyDesk Root CA 2 certificate)
- Unzip the AnyDesk-Root-CA-2.zip attached file
- Import into firewall the AnyNet Root CA 2 certificate (AnyDesk ROOT CA 2.crt) and marked as Trusted Root CA.
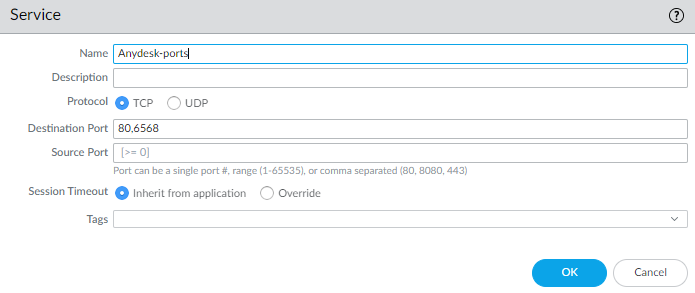
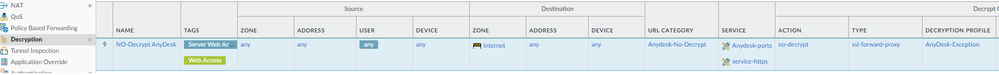
- Create a service object for TCP 80 and 6568
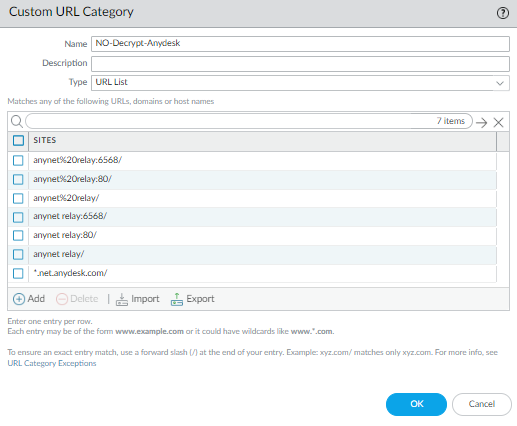
- Create a custom URL list for:
- anynet%20relay/
- anynet%20relay:80/
- anynet%20relay:6568/
- anynet relay:6568/
- anynet relay:80/
- anynet relay/
- *.net.anydesk.com/
- Create a decryption profile with "Block sessions with expired certificates" and "Block sessions with untrusted issuers" checked on No Decryption tab
- Create a decryption policy with action of NO-DECRYPT using custom URL categories and services configured above as match criteria and action of NO-DECRYPT
Note: If your service object includes only destination port 6568, then in your decryption policy you need to include also service-http, on service criteria.
Cosmin
Don't forget to Like items if a post is helpful to you!
Please help out other users and “Accept as Solution” if a post helps solve your problem!
Read more about how and why to accept solutions.
Disclaimer: All messages are my personal ones and do not represent my company's view in any way.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-03-2022 03:34 AM
Thank you
- 56296 Views
- 43 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- XSIAM V3.4 upgrade - anyone having issues? in Cortex XSIAM Discussions
- Panorama scheduled export path in Panorama Discussions
- Regarding impoper tagging of node-tar vulnerability with alpine-tar package when using prisma scan tool in Prisma Cloud Discussions
- Tuning Panorama HA Timers to Stop False HA1 Alerts over MPLS in Panorama Discussions
- Cortex XDR 8.9 Non-Persistent Citrix Servers and Cache Write Issue in Cortex XDR Discussions