- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Captive portal authentication over TLS
- LIVEcommunity
- Discussions
- General Topics
- Re: Captive portal authentication over TLS
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Captive portal authentication over TLS
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-08-2022 01:45 AM
Hi, I've enabled captive portal on our systems, following the PA docs (Configure Authentication Portal (paloaltonetworks.com)). I have an SSL/TLS profile created with a valid, trusted certificate signed by our own internal CA. When our machines try to authenticate to the captive portal, they do so over HTTP not HTTPS. Is there some way to force captive portal auth over HTTPS?
Thanks!
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-08-2022 07:37 AM
Hmmm, good question. The SSL request needs to come from the users browser, not from the FW.
You may want to also make sure that your redirect IP has an interface mgmt profile that support only HTTPS and not HTTP.
You may want to confirm that traffic from the user to the redirect IP is ONLY SSL on app-default, vs any on port 443.
Thanks.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-11-2022 05:52 AM
Hi Steve,
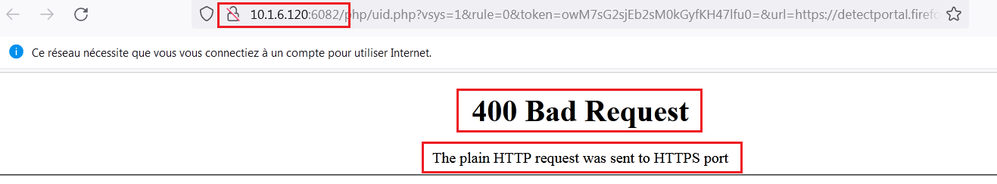
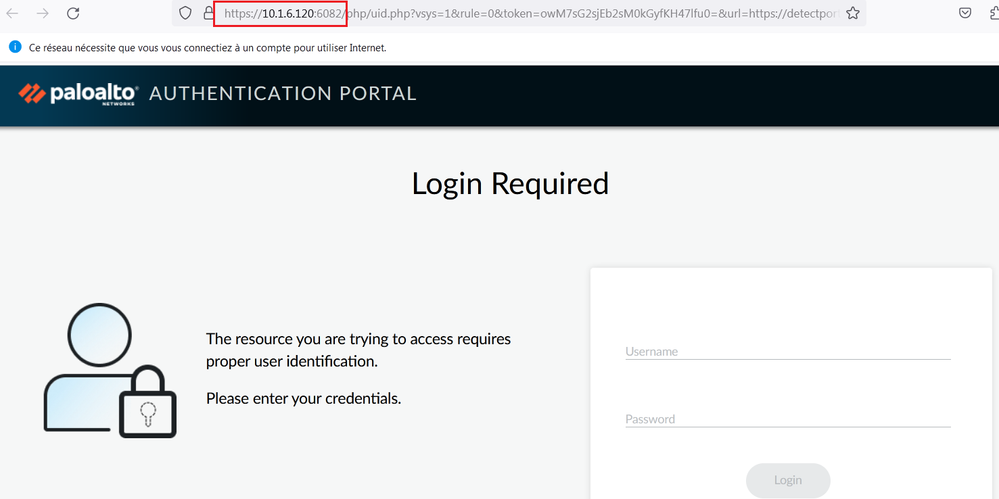
The SSL request made to the firewall is via a 302 injected into the session by the FW. If I decrypt the traffic I see the 302 which has a header location value of http://my_captive_portal_addr:6080.
Palo alto documentation suggests that 6080 should only be used for NTLM auth (Ports Used for Management Functions (paloaltonetworks.com)) however we are successfully auth'ing using kerberos.
If I manually browse to https://my_captive_portal_addr:6082 I get a valid TLS connection albeit with a 403, so the firewall is obviously capable of setting up a TLS encrypted session to the captive portal address.
The interface management profile I'm using doesn't have HTTP or HTTPS selected. Only Response Pages and User-ID, which I believe is suggested by the palo alto documentation. I'm having a bit of trouble getting logs for the traffic in question, although I can see it in the fw session browser, I'm not sure it's using the security rule I'm expecting, so I need to narrow that down first.
I was hoping there might be a way to tell the captive portal configuration to only use port 6082 but my googling has returned nothing so far. I can't see that configuring a security rule allowing only SSL on app default will make any difference given the header location specifies http traffic over port 6080.
Thanks,
George
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-08-2023 07:38 AM
Anyone have a solution to this problem? I'm seeing the exact same thing. I verified via PCAP that users are getting redirected to the Captive Portal unencrypted over port 6080. I can browse to the Captive Portal over port 6082 and I get a valid TLS connection with the correct server certificate.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-10-2024 01:50 PM - edited 02-10-2024 01:51 PM
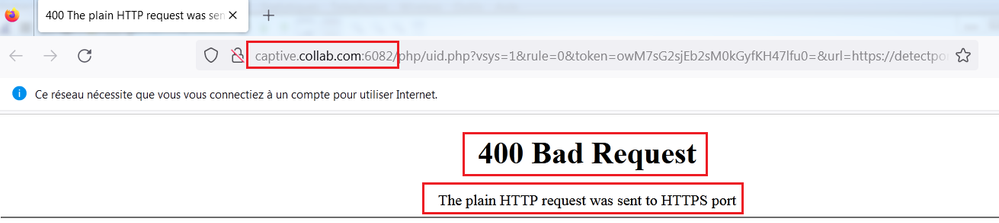
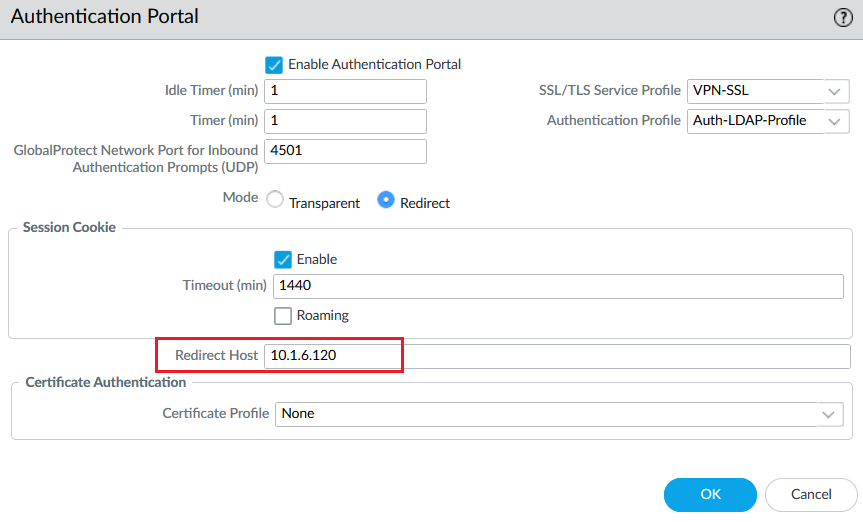
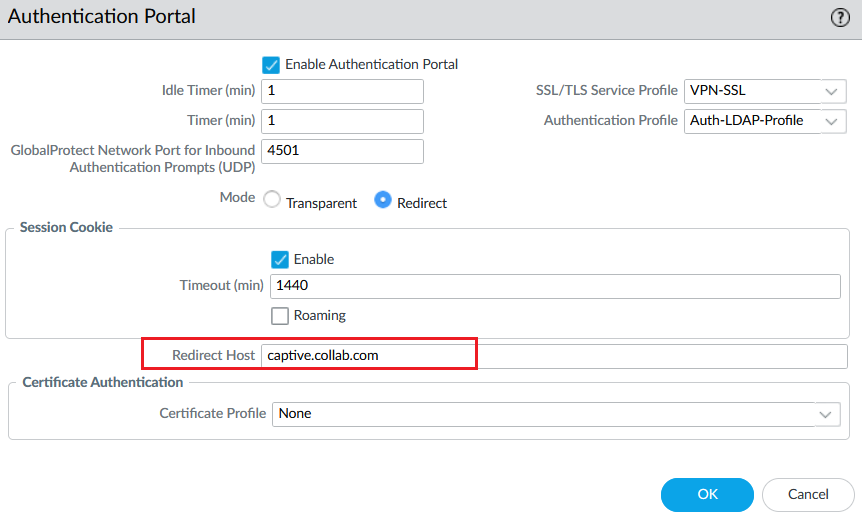
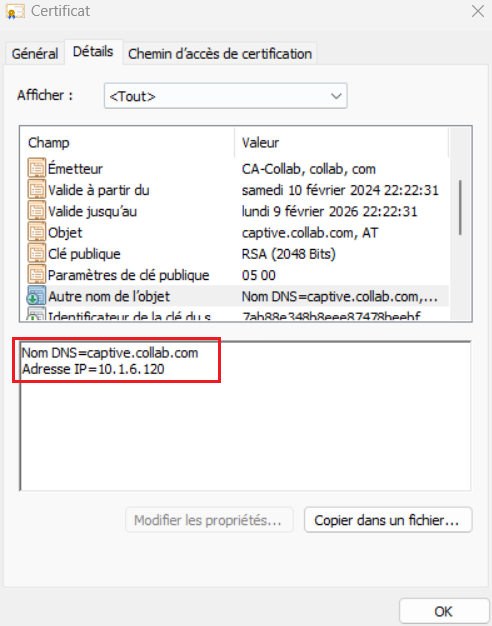
@jambulo @GSA_George @S.Cantwell I was faced to the same issue and I found where is the problem :
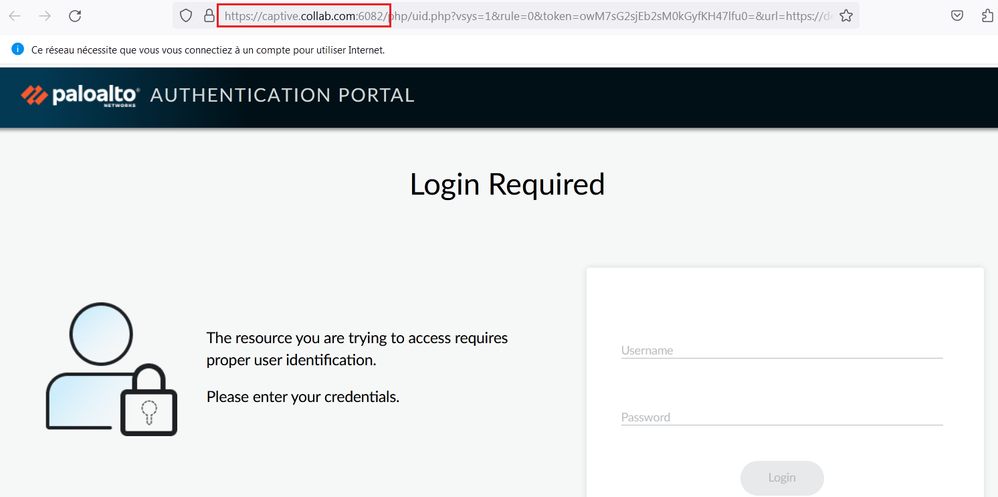
If you are using the IP address of the firewall or the FQDN in the Authentication Portal Settings, make sure that the certificate associated to the TLS Service Profile has this IP address of the FQDN in the SAN (Subject Alternative Name).
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-13-2024 03:05 PM
Hello @rmeddane
Thanks for this info.. I totally make sense that if the cert is signed as FDQN, then we use the FQDN name, but if the cert is signed by IP, then we use the IP in the Captive Portal settings... same/similar to a local/test GP configuration.
It is good info for other community users and your contribution is appreciated.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-18-2024 04:59 AM
Thanks @S.Cantwell for the additional infos.
- 6868 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Global Protect Portal / Clientless VPN does not recognize SAML username after update to 10.1.14-h20 in GlobalProtect Discussions
- Global Protect Connectivity Issue in GlobalProtect Discussions
- GlobalProtect Always-On (6.3.3-c711) – Users Stuck in “Connecting” State but Still Have Internet Access in General Topics
- Windows Clients – Captive Portal Not Triggering with GlobalProtect Always-On Enabled in General Topics
- PA Global Protect in GlobalProtect Discussions