- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Dealing with Threat Alerts?
- LIVEcommunity
- Discussions
- General Topics
- Re: Dealing with Threat Alerts?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-23-2017 06:50 AM
Hi Folks,
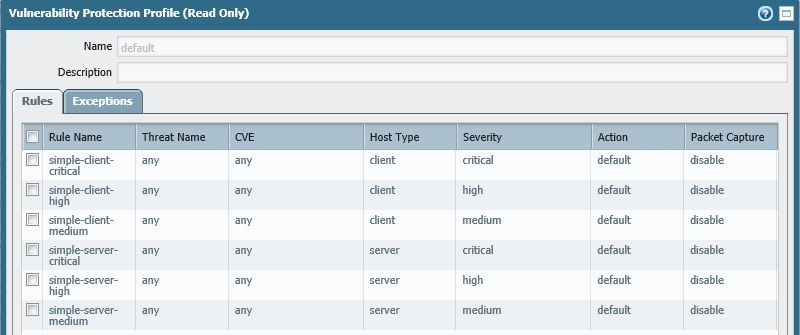
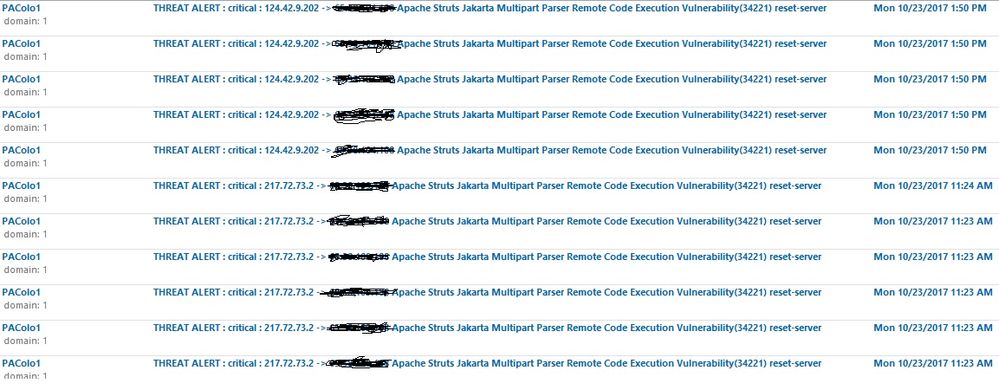
We have Critical Threat Alerts emailed to us and usually its every couple of days we get a few alerts, mostly Apache Struts Jakarta. But over the last 4-5 days there has been a significant increase in threat alerts. 60-100 emails per day, same IP address in groups of ~10. We are using default vulnerability protection profile and default action (reset-both).
Since the increase in alerts, our management gets concerned asking if there is a problem. I talked to support and assured me that firewall is doing its job, its just an increase in attack attempts, and is common.
I've considered creating a new security rule at the top to keep a running list of source IP address with a deny action, but that sounds like a lot of manual administration.
I'm curious if anyone in the community has comments about receiving alerts or how they handle an increase in attacks?
Is it common, just deal with it? Do folks filter out certain threat emails or stop critical threat email alerts all together?
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-23-2017 01:27 PM
Hello,
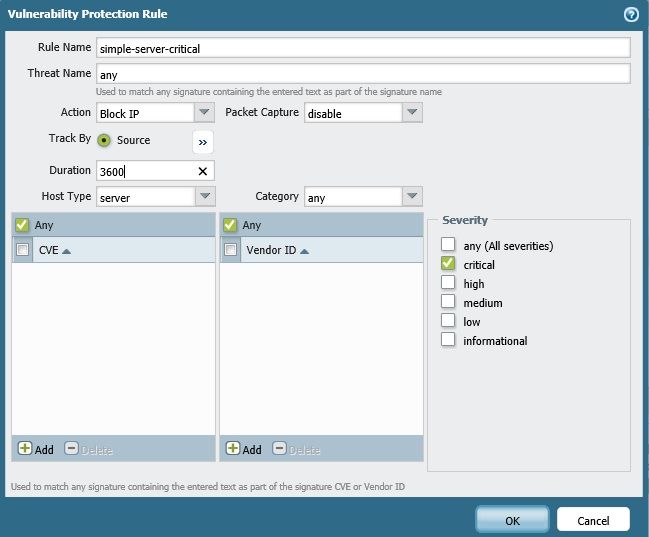
What we did was set the policies to block for the max time of 3600 seconds. That way the attacker takes a lot longer to figure out they are denied.
The other thing you could try is to set the policy to reset client. Since the attack is coming from the external "server", only your servers connection gets reset and theirs has to time out. Basically forcing their connection to stay open and bleeing their resources and not yours.
I would also love to hear others thoughts on this.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-23-2017 01:27 PM
Hello,
What we did was set the policies to block for the max time of 3600 seconds. That way the attacker takes a lot longer to figure out they are denied.
The other thing you could try is to set the policy to reset client. Since the attack is coming from the external "server", only your servers connection gets reset and theirs has to time out. Basically forcing their connection to stay open and bleeing their resources and not yours.
I would also love to hear others thoughts on this.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-23-2017 02:00 PM
You really should have an automated response setup that can read these events and block the source IPs at a set threshold. While @OtakarKlier's solution is a good first step, it isn't really recommend to just live with the IPs attacking your network. Setup an automated response that puts these indicated addresses into a deny rule and just block them all together. MineMeld can help with this, otherwise their are plenty of other possible solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-24-2017 11:39 AM
Thank you guys for the feedback.
We are currently using default vulnerability profile.
When you say block action, do you mean Block IP like this? Does that reduce the alert emails?
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-24-2017 12:26 PM
The setting you have displayed would block the IP that triggered that critical threat alert for 3600 seconds. That will stop you from recieving another alert for that time period, but if you have IPs continually launching attacks against your network you would still recieive alerts when that window has passed.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-24-2017 12:37 PM - edited 10-24-2017 12:37 PM
BPry
Thank you again (I am still learning). The alerts and traffic log indicates that the attacks occur within a couple of minutes and then a different IP (group) comes. Would blocking the IP for this duration (1 hour) at least give some relief, assuming the attacks stay like they currently are (within minutes and then stops)?
I agree, ideally need to come up with an automatically updated IP deny rule.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-24-2017 01:24 PM
It would certaintly help. Keep in mind that IP Spoofing is a thing though, and what you are describing is typical of someone employing a botnet.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-24-2017 01:32 PM
BPry
Thank you so much for your responses, as I continue to learn new everyday. 🙂
Just to confirm. For this example, since these two IP threats came in consecutively and then stops, I should only receive two alerts (1 for each IP) instead of a whole bunch of them by employing this new Block IP setting? (For at least the hour)
That's the idea right? Making more sense to me.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-01-2017 03:24 AM
Hi,
I'm not sure is this quite correct if you live this host type to server? If you filter your traffic logs for attacker address, you will see that it is client side of connection. So any attacker which initiate connection to your exposed resource (ex. web server...), is considered as client and stateful firewall marked it as client side of session.
When replicate that on this policy setting it should be client host type, isn't it?
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-01-2017 05:43 AM
Out of curiosity why would you want to close the client side by a reset? If you force the potential attacker to leave its connection open, but you close the servers connection, then you save resources on your end but cause the attacker to increase their resources.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-01-2017 06:06 AM
yes you're completely right, it is good to reset server connections in this case, so what should be scenario where you suggest to use reset client connections instead?
- 1 accepted solution
- 8178 Views
- 11 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Building Cybersecurity Strategies: A Game of Digital Mahjong in General Topics
- Newsletter: Cloud Delivered Security Services, Oct-2025 in Advanced Threat Prevention Discussions
- High availability system alarms in Next-Generation Firewall Discussions
- How to allowlist a file form wildfire-virus in General Topics
- Does Panorama Forward These Events to External SIEMs via Syslog by Default? in Panorama Discussions