- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Destination NAT vs Source NAT with Bi-directional?
- LIVEcommunity
- Discussions
- General Topics
- Re: Destination NAT vs Source NAT with Bi-directional?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-04-2017 01:22 PM
Hi folks,
I am reading several articles about NAT types and bi-directional.
I have a test going, but confused about how my web server is translating its source address when replying.
I thought that I would have to create a bi-directional NAT rule to get the web server to change its IP back to public (after the D-NAT), but that's not the case. It works with just a D-NAT rule.
How is the source IP of the web server switching back to a public IP on reply?
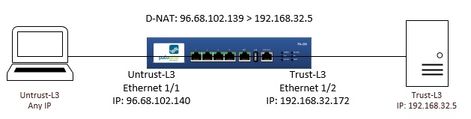
This is my goal and current configuration.
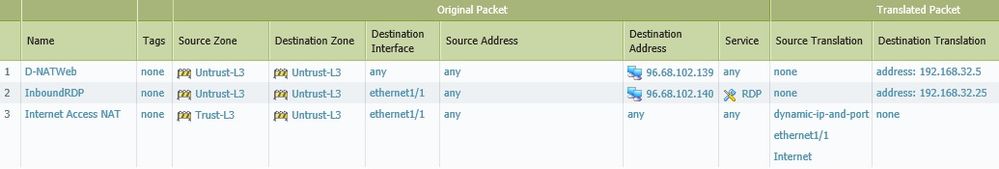
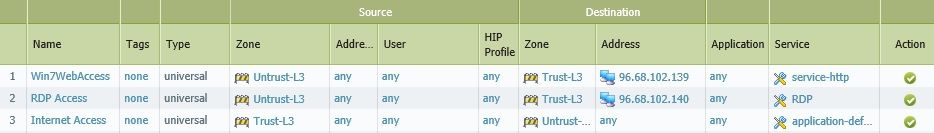
Rules:
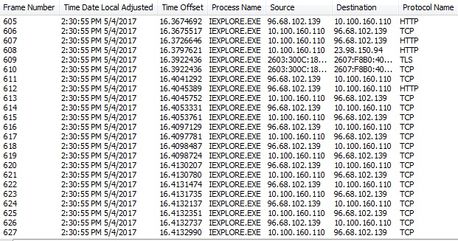
Client (behind a NAT) on the internet. I can see the source must have changed back to the public IP.
I can see when it leaves the Web Server it is still the private IP as source, but must change to public at some point.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-07-2017 04:53 AM
- I thought that I would have to create a bi-directional NAT rule to get the web server to change its IP back to public (after the D-NAT), but that's not the case. It works with just a D-NAT rule.
If I understand the question correctly, you see that the inbound flow has the destination nat change but you don't understand why the private address of the server reply packet is also converted back to the original public address.
The reason for this behavior is that stateful firewalls in general, like the PA maintain a session table that knows about both directions of the flow based on the unique total combination both ip addresses and both source and destination ports and protocol.
So when that reply packet from the web server comes back to the firewall it matches the session and the firewall knows it must reverse the NAT it originally performed on the same flow.
This is not unique to Palo Alto but standard firewall NAT behavior.
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-04-2017 01:46 PM
Everything you send out the firewall will get sourced as a public/external IP address. So based on its route out, it will take on that external/unstrusted interface IP. Firewall's will do that with all outbound traffic unless told otherwise.
ACE 7.0, PCNSE7
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-04-2017 02:10 PM
If you have single public IP then you don't need bi-nat rule as everything sourcing from inside will be SNAT'ed to this single IP anyway.
If you have range of IP's and you need specific servers to go out from specific IPs then you either create 2 NAT policies (SNAT and DNAT) but it is easier to do single bi-nat rule.
Example is email servers where you want outgoing email go out from same IP it comes in to because then reverse DNS matches and spam filters are more happy accepting emails from you.
Actually bi-nat rule creates 2 rules one for SNAT and other for DNAT but you don't see this in GUI (only in CLI).
bi-nat rule will double your NAT rule count and both (visible and hidden) NAT policy count againt firewall max NAT count (might be important in case of smaller boxes).
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-05-2017 08:19 AM
Thanks for responding!
Yea, I can understand if you are using the one public IP, but I am using a different one than the one for my general internet connection. I do have a range, but using two of them in my example. One for general internet usage and the other for my web server. That's why I am confused. It's successfully changing its source IP when leaving the firewall, but without the need for a bi-directional S-NAT rule.
Still researching...
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-05-2017 08:27 AM
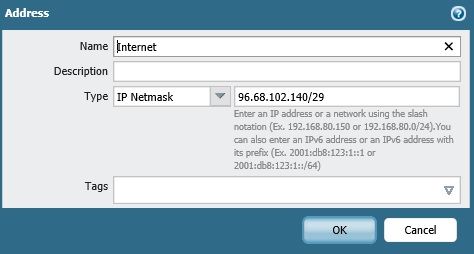
Hi,
Do you mind showing your 'internet' address object's subnet mask? I suspect you've added this in as a network and therefore the firewall has a pool of IPs to use for source NAT.
Ben
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-05-2017 01:52 PM
Yes, I did configure my internet address with a subnet bit mask.
Does that explain how it knows to change the source IP back?
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-07-2017 04:53 AM
- I thought that I would have to create a bi-directional NAT rule to get the web server to change its IP back to public (after the D-NAT), but that's not the case. It works with just a D-NAT rule.
If I understand the question correctly, you see that the inbound flow has the destination nat change but you don't understand why the private address of the server reply packet is also converted back to the original public address.
The reason for this behavior is that stateful firewalls in general, like the PA maintain a session table that knows about both directions of the flow based on the unique total combination both ip addresses and both source and destination ports and protocol.
So when that reply packet from the web server comes back to the firewall it matches the session and the firewall knows it must reverse the NAT it originally performed on the same flow.
This is not unique to Palo Alto but standard firewall NAT behavior.
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-08-2017 01:24 AM
@pulukas is on the money i think
you don't need to create a policy in both directions of a flow: the firewall maintains a state table of all active sessions with their c2s and s2c (client to server and server to client) flows. This includes any NAT actions taken on the outbound flow so it can be automatically applied to the inbound flow (this is indeed pretty common among modern firewalls)
A bi-directional NAT rule enables traffic to be initiated in both directions so a server can receive sessions from the internet on it's public IP and outbound (new) connections will also use the public IP (think smtp relay server receiving an email and then relaying it out to the exchange server)
I tried to list all NAT combo's here:
Getting Started: Network Address Translation (NAT)
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-08-2017 08:39 AM
Thank you folks!
I will be getting my first real training starting next week. PA-201 class.
So I will try to get my understanding clear about bi-directional NAT.
- 1 accepted solution
- 14277 Views
- 8 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Unable to establish tunnel during Service Connection configuration (Details Added with Screenshot) in Prisma Access Discussions
- Security Policy with Destination Criteria in Strata Cloud Manager
- Move Firewall from one Hierarchy device group/template to another hierarchy device group/template in panorama in Panorama Discussions
- Issue with call recording (flow_predict_convert_rtp_drop) in Next-Generation Firewall Discussions
- Traffic Logs missing from subset of datetime range when using certain filters? in General Topics