- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Extra Certs..Inbound Decryption
- LIVEcommunity
- Discussions
- General Topics
- Re: Extra Certs..Inbound Decryption
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-10-2022 08:31 AM
We have PA doing inbound decryption in front of F5 which is proxying a web server.
F5 is doing SSL bridging. That is it terminates the SSL connection and starts new connection to the server from itself.
Website itself works fine.
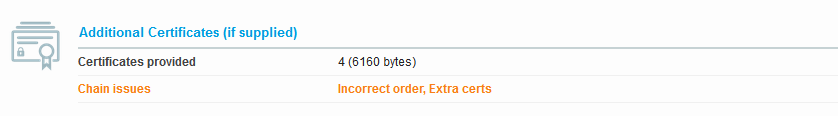
When we do SSLlabs test on it we get extra certs error. I am not sure why the certificates are being duplicated.
On clicking the download server chain link on the side of the result we get dual entries for the cert. Its duplicating both the server cert and intermediate cert making it 4 where it should be only be 2 certs.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-11-2022 03:42 AM
Hi @raji_toor ,
Theoretically speaking even with both devices doing SSL decryption, it make more sense for the firewall to do something strange, because SSL decryption is basically absolutely the same as F5 bridging - Firewall will build to separate SSL connection (one with the client and one with the server, which in your case the F5 VIP).
For the connection between FW and the client (in your tests the SSLlabs) firewall will act as a server and will provide the SSL certificate that you have imported to the FW for the Inbound SSL decryption.
For the connection between the FW and the F5 it will act as client so it will only try to validate the cert that F5 is sending - it shouldn't do anything with that, nor forward it to the client.
So as a starting point it sound reasonable to double check the certificate that you have imported to the firewall. Most simple check would be
1. Export the certificate in PEM format (you don't have to export the private key)
2. Open the file with text editot (notepad, notepad++ etc)
3. Check how many "BEGIN CERTIFICATE" and "END CERTIFICATE" sections you have
4. Open the file like certificate (double click on the file), go to "certification path" and compare how many cert do you see in that three with the number of cert sectiond do you see in the text editor. Are they matching?
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-11-2022 03:42 AM
Hi @raji_toor ,
Theoretically speaking even with both devices doing SSL decryption, it make more sense for the firewall to do something strange, because SSL decryption is basically absolutely the same as F5 bridging - Firewall will build to separate SSL connection (one with the client and one with the server, which in your case the F5 VIP).
For the connection between FW and the client (in your tests the SSLlabs) firewall will act as a server and will provide the SSL certificate that you have imported to the FW for the Inbound SSL decryption.
For the connection between the FW and the F5 it will act as client so it will only try to validate the cert that F5 is sending - it shouldn't do anything with that, nor forward it to the client.
So as a starting point it sound reasonable to double check the certificate that you have imported to the firewall. Most simple check would be
1. Export the certificate in PEM format (you don't have to export the private key)
2. Open the file with text editot (notepad, notepad++ etc)
3. Check how many "BEGIN CERTIFICATE" and "END CERTIFICATE" sections you have
4. Open the file like certificate (double click on the file), go to "certification path" and compare how many cert do you see in that three with the number of cert sectiond do you see in the text editor. Are they matching?
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-11-2022 07:48 AM
@aleksandar.astardzhiev Thanks for pointing that out, When I checked the PEM file it had duplicate entries from flawed conversion before importing. On correcting this and reimporting it works as expected.
- 1 accepted solution
- 3293 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Fortigate Correlation rules thread in Cortex XSIAM Discussions
- Prisma Access Explicit Proxy — Anti‑Spyware behavior when DNS bypasses Prisma (logging subtype + test methodology) in Prisma Access Discussions
- Unable to block download and upload for chatgpt and messengers in Next-Generation Firewall Discussions
- GlobalProtect Name Normalization issue in GlobalProtect Discussions
- Decryption suddenly failed for all Webpages using Sectigo Certs in General Topics