- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Firewall Config Templates(network) not showing up in Panorama
- LIVEcommunity
- Discussions
- General Topics
- Firewall Config Templates(network) not showing up in Panorama
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Firewall Config Templates(network) not showing up in Panorama
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-03-2023 06:05 PM - edited 03-03-2023 06:06 PM
Yesterday we had to reboot one of our firewalls that is managed by the panorama. After the reboot, we noticed that half the config is no longer showing in the panorama. Everything appears to be ok locally on the firewall (panorama pushed config and interfaces) but it doesn't look like it's being managed by panorama anymore.
Even though in panorama the firewall shows connected and the commit/push to devices is successful. We tried restarting the mgmt server process on the Panorama but with no success.
Though the firewall shows connected we do not see any logs being forwarded from the firewall even though we have Log Settings on the firewall to forward all the logs to Panorama. We also do not see "SC3" error under ms.log on the firewall.
We can see commit on the firewall is also successful when pushed from Panorama. Still, we do not see anything under Interfaces/Zones in Template on Panorama but after the successful push, on Firewall we see all the Policies created in Panorama and all the interfaces correctly. This was working before the reboot and since we rebooted we noticed this issue.
We are trying to figure out how to get the full config of the firewall back in panorama. Is there a way we can re-add the template configuration from the firewall back on Panoarama without loosing anything?
Thanks for help.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-03-2023 07:11 PM
Can we do the import following below steps:
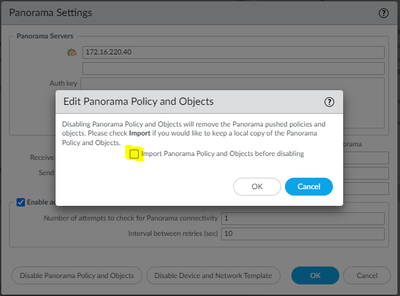
- On the firewall, remove the Panorama settings by going to Device > Setup, and edit the Panorama Settings, remove the Panorama configuration. Most Important store when Disabling the Panorama Policy and Device Network template IMPORT these settings on the firewall so that we do not have to redo any configuration again. Check the configuration box below.
- Import Panorama Policy and Objects before disabling and Import Device and Network Template before disabling. This will store all the config locally on firewall and then perform Commit.
- We would need to remove the Firewall from Panorama Managed Devices and follow step-by-step process highlighted in : https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000Cmd6CAC
- In the above step we will also remove the Device Group and Template settings so as to avoid data duplication and corruption.
- When the device is removed from Panorama and is being locally managed, we would start the process to reimport the device in Panorama.
- The step-by-step guide to reimport the firewall is at https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000CloRCAS
- Once we add the device in Managed devices we can reimport the device configuration on Panorama completely and after checking all the configuration is back from firewall, to manage this from Panorama we will do 'Export or push device config bundle'.
- The device will be back in Panorama with all the configuration.
- 4840 Views
- 1 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- cloud services plugin update to 5.2.x in Panorama Discussions
- Hotspot Shield VPN still works even though traffic logs show deny – Palo Alto Firewall in General Topics
- Escalation process for Customer's with Premium Partner Support in General Topics
- PAN OS version 11.1.13-h1 is remediate or not? in General Topics
- No ping response from AAD in Next-Generation Firewall Discussions