- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Forwarding logs to MS Sentinel
- LIVEcommunity
- Discussions
- General Topics
- Forwarding logs to MS Sentinel
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Forwarding logs to MS Sentinel
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-02-2022 09:05 PM
Hi Guys,
How to send Data Filtering Logs to our Microsoft Sentinel as there is no option in Log Settings for Data Filtering?
Many thanks in advance.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-03-2022 07:45 AM
Hello there
Am I missing something?
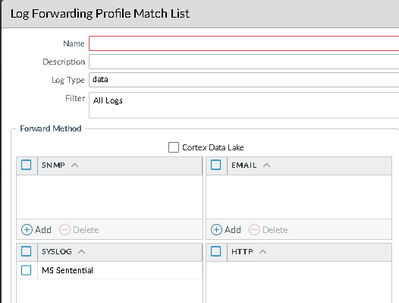
I see Data in a log forwarding profile:
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-03-2022 03:56 PM
@S.Cantwell : Thanks for that. Was only not sure about MS Sentenial. So, if it accepts syslog msgs then I should be fine.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-11-2022 09:09 PM - edited 05-12-2022 03:29 PM
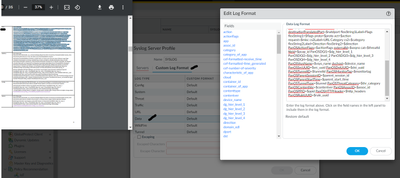
@S.Cantwell : the issue is, through log forwarding all the data from TRAFFIC, CONFIG is reaching the MS Sentential except for DATA filtering. Below is the config we did for the data filtering (CEF- style Log Format is copied)
PA version: 10.1.4-h4
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-16-2022 04:58 AM
Hi @Pras ,
I would suggest you to validate your Data Logs format. I had issues with copy-pasting from this PDF file - there were some non-printable characters when copy from the PDF. I would suggest you to paste format into text editor and check enable "show all characters" (I personally prefer NotePad++.
We don't forward data logs to Sentinel (yet), but below is what we have in our FWs (without any extra chars)
CEF:0|Palo Alto Networks|PAN-OS|$sender_sw_version|$subtype|$type|$number-of-severity|rt=$cef-formatted-receive_time deviceExternalId=$serial src=$src dst=$dst sourceTranslatedAddress=$natsrc destinationTranslatedAddress=$natdst cs1Label=Rule cs1=$rule suser=$srcuser duser=$dstuser app=$app cs3Label=Virtual System cs3=$vsys cs4Label=Source Zone cs4=$from cs5Label=Destination Zone cs5=$to deviceInboundInterface=$inbound_if deviceOutboundInterface=$outbound_if cs6Label=LogProfile cs6=$logset cn1Label=SessionID cn1=$sessionid cnt=$repeatcnt spt=$sport dpt=$dport sourceTranslatedPort=$natsport destinationTranslatedPort=$natdport flexString1Label=Flags flexString1=$flags proto=$proto act=$action request=$misc cs2Label=URL Category cs2=$category flexString2Label=Direction flexString2=$direction PanOSActionFlags=$actionflags externalId=$seqno cat=$threatid fileId=$pcap_id PanOSDGl1=$dg_hier_level_1 PanOSDGl2=$dg_hier_level_2 PanOSDGl3=$dg_hier_level_3 PanOSDGl4=$dg_hier_level_4 PanOSVsysName=$vsys_name dvchost=$device_name PanOSSrcUUID=$src_uuid PanOSDstUUID=$dst_uuid PanOSTunnelID=$tunnelid PanOSMonitorTag=$monitortag PanOSParentSessionID=$parent_session_id PanOSParentStartTime=$parent_start_time PanOSTunnelType=$tunnel PanOSThreatCategory=$thr_category PanOSContentVer=$contentver PanOSAssocID=$assoc_id PanOSPPID=$ppid PanOSHTTPHeader=$http_headers PanOSRuleUUID=$rule_uuid
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-16-2022 05:48 PM
Thanks a lot, @aleksandar.astardzhiev : will follow this too and update
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-26-2022 07:08 PM - edited 05-26-2022 07:09 PM
Checked the Custom log format one by one, and found no issues.
Is there a way in FW to check if the Data Filtering Logs are being dropped or not forwarded? The configuration has no issues for sure bc other logs are reaching except for Data Filtering.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-02-2022 07:55 AM
Hi @Pras
I don't expect FW being "dropping" the logs, for me it is more likely for the Azure to drop them because they are failing to match the CEF format. On the CEF collector there is regex pattern which if not matched log will not be forwarded to Sentinel.
You could try to run a packet capture on the firewall to confirm that Data Filtering logs. You can use the tcpdump https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000CleECAS and filter based on syslog collector address.
Note that there is no way to capture only data filtering logs, so depending on your traffic your capture could filled up with traffic logs. So you could consider doing this when there is less traffic and if possible to trigger data filtering log, so to be sure that there is such event during the capture.
- 6754 Views
- 9 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Log forwarding from Cloud NGFW in Azure to Log Analytics Workspace for Sentinel in VM-Series in the Public Cloud
- Forward NGFW logs stored in Strata Logging Service to Microsoft Sentinel in Strata Logging Service Discussions
- Identifying Source IP Addresses for Routing Palo Alto Firewall Logs to an Azure Collector via IPSec Tunnel in General Topics
- Cortex XQL "Let" replacement in Cortex XDR Discussions
- log forwarding to syslog | drops and queue in General Topics