- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
FW in Palo IP changed
- LIVEcommunity
- Discussions
- General Topics
- Re: FW in Palo IP changed
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
FW in Palo IP changed
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-01-2021 06:16 AM
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-03-2021 12:08 PM
From the new management IPs of the firewalls, is it possible to reach the panorama? Is the new network configuration correctly configured and these firewalls are able to communicate to the default gateway and other networks? Is an ACL on panorama configured that restrics access to only specific IPs or is a firewall in front of the panorama that prevents the communication from the new IPs?
The communication is always coming from the firewall to panorama so you need to make sure that this way of communication is possible.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-04-2021 12:39 AM
Hi @RobertShawver ,
Two points to remember when troubleshooting panorama connectivity:
- Aways the FW is the initiator of the connection. Which means FW is always the source of the traffic and panorama is just waiting for someone to call it
- Panorama is tracking firewalls by serial numbers, not by management IP. Which means panorama will accept any connection request as long as the FW serial number is added to panorama.
So by default Panorama will accept/establish TCP connection with any source IP, but can reject the connection if the provided FW S/N is not in the list of managed devices. You can control this by configuring "Permitted IPs" under the panorama management interface. That way Panorama will respond only IP from the allow list.
If everying is setup properly if FW is connected to Panorama, but its mgmt ip is change. The new IP will be detect and changed automatically. So it looks more like the new mgmt ip is not reaching the Panorama:
- Try to ping panorama from fw using mgmt interface
- Check if you have configured permitted ip panorama interface
- Last resort make a packet capture on panorama and FW interface and confirm that you have bi-directional traffic
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-12-2021 09:49 AM
Great info to have! I read your post and figured it out. I set the object for the Firewalls within Pano to IP (so pano saw the old IP and not the new). I changed it to FQDN and whiz-bang, it connected.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-12-2021 10:54 AM
@RobertShawver Can you please tell me where did you use that object? Would be great if you share a screenshot(after masking any sensitive details)
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-12-2021 11:25 AM
Pretty simple really, we have Addresses and Address Groups under the Objects tab in Panorama. You create the Address object and then add it to a Address Groups object. We then apply that Address Group to the Rules needed for them to talk.
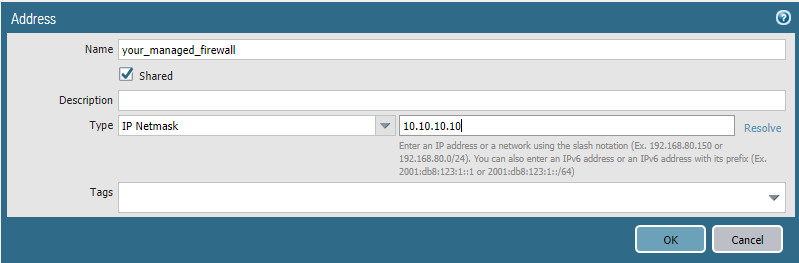
What I, stupidly, did was when I created the Address for the managed firewall I used Type IP Netmask
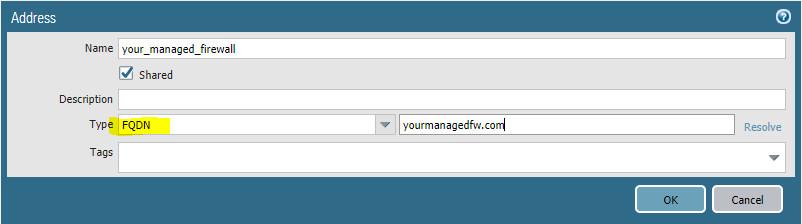
What I should have done and did correct was use Type FQDN
This way if the IP changes, I don't have to do anything. 🙂
- 4143 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Asymmetric Routing - Palo Edge Firewall Active/Passive to Nexus Core in General Topics
- What is the Palo Alto recommended standard for Vulnerabilty Profiles, is it to block Critical and High Alerts? or to block medium alerts as well? in Next-Generation Firewall Discussions
- impossibility of access to the palto firewall in Next-Generation Firewall Discussions
- Multiple High/Critical Alert Detected via Port 18264 | Possible FP in General Topics
- Multiple High/Critical Alert Detected via Port 18264 | Possible FP in VirusTotal