- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
group-based policies for RADIUS authenticated users.
- LIVEcommunity
- Discussions
- General Topics
- group-based policies for RADIUS authenticated users.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
group-based policies for RADIUS authenticated users.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-16-2021 07:31 AM
Dear community,
For users who authenticate via RADIUS on Active Directory, is there any possibility to fetch the groups for those RADIUS users so that group-based policies can be created in the firewall?
Thank you!
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-16-2021 02:13 PM
Hello,
I think this might be what you are looking for:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000POFXCA4
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000CluUCAS
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-30-2021 01:54 AM
Hi @OtakarKlier ,
Many thanks for your answer.
What I´m trying to do is to retrieve the group membership for RADIUS authenticated users in the AD. So that I can use the groups in the policies.
I´m trying to do a group mapping in some way like you do through LDAP.
Is this possible?
Thank you in advance!
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-30-2021 07:43 AM
Hello,
Yes this is possible.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-23-2023 02:01 AM
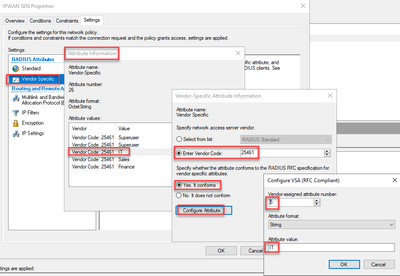
hi @OtakarKlier This KB is for LDAP and not for Radius like what @Carracido was after. I am also having issues with Radius and retrieving user groups. i have ticket the 'Retrieve user groups' in the auth profile and configure radius with what i believe are the correct VSA's as per https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClIxCAK
Unfortunately i still cannot pull any groups up to panorama/firewall. Unfortunately this design cannot utilise LDAP at the moment so my options are limited. Any suggestions?
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-23-2023 05:15 AM
You can configure VSA's to use group membership to log into the firewall but Palo don't support using RADIUS groups in security policies.
There is a feature request FR2729 to add that capability.
Ask your Palo SE to add a vote to it.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-23-2023 05:19 AM
hi @Raido_Rattameister thanks for the update. in my case, the customer doesnt require security enforcement via policy. At this stage we want to just pull the user groups up from radius and use the im the auth profile and subsequently the client config in GP. If you have any advice, it would be appreciated.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-24-2023 01:08 PM - edited 10-24-2023 01:09 PM
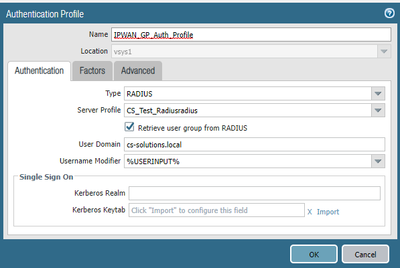
I did get this working but it took quite a lot of messing around so as to not break inadvertently what was working. Not sure what the issue is on your end but in my case we did not have the USER DOMAIN field filled in or the RETRIEVE USER GROUP FROM RADIUS options checked. I never went far enough with it to tell if I absolutely needed the domain in there but in my case this was what ultimately did the trick for me.
Also the gateway or wherever the RADIUS group check is being done needs the full distinguished name to work properly.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-24-2023 06:01 PM
hi @TonyDeHart thanks for the info. i have configured the user domain and ticked 'retrieve user groups' in the auth profile. i have no issue with authenticating user with radius when 'All' is selected.
VSA's configured on the radius for user group IT as an example.
if anyone has any ideas, let me know.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-25-2023 05:10 AM
I'm no expert on this, but what I was told when working with Palo support,was that the domain actually doesn't have any impact on the RADIUS authentication itself (in my case it is RSA) and that the domain and group info used is actually using the LDAP groups defined in the authentication profile to determine group membership. Without the domain configured it wasn't determining/matching the groups up with the auth profile and failed the membership check. It was necessary for the groups to be included in the auth profile AND the domains to match.
Sorry it was a detail I'd forgotten until I looked a bit closer.
- 5999 Views
- 9 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Best practices for Palo Alto security policy when destination IP/FQDN is dynamic or unknown in Next-Generation Firewall Discussions
- Tuning Panorama HA Timers to Stop False HA1 Alerts over MPLS in Panorama Discussions
- Unable to block download and upload for chatgpt and messengers in Next-Generation Firewall Discussions
- Assistance with LDAP Authentication in General Topics
- Inquiry regarding Tenant Backu & Recovery in Cortex XDR Discussions