- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
how can we confirm if there is existing firewall rule or not in the policy by filtering by source and destination IP address and port numbers.
- LIVEcommunity
- Discussions
- General Topics
- how can we confirm if there is existing firewall rule or not in the policy by filtering by source and destination IP address and port numbers.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
how can we confirm if there is existing firewall rule or not in the policy by filtering by source and destination IP address and port numbers.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-09-2021 03:06 AM
I can find existing firewall rule in the Firewall policy by searching by just source IP address or Just Destination IP address but our Firewall policy rule base is huge and i need to filter it by Source IP and destination IP address (both) and possibly by port number as well , (Just like Checkpoint).
can someone kindly share screenshot of this, that how we can do this in the Palo alto FW.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-09-2021 07:08 AM
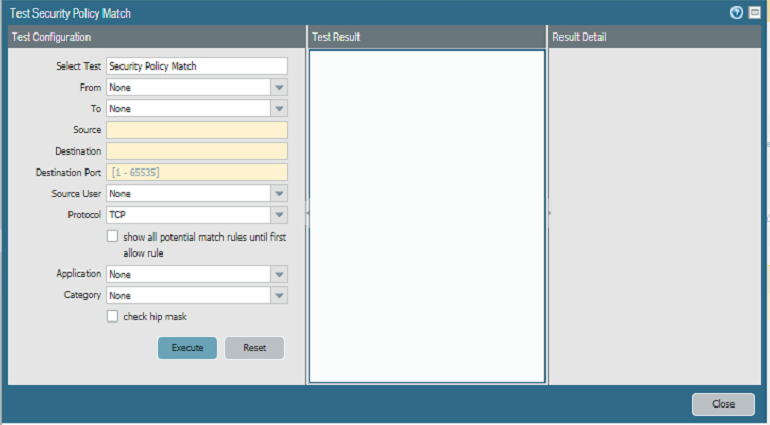
So I'll actually do ya one better; the firewall actually has a built in function to test rulebase matches to ensure that traffic is actually going to match outside of just looking through the policies!
If you are using the GUI and a newer PAN-OS release, you can use the 'Test Policy Match' on the bottom right of the policies tab view. This lets you to simulate traffic flows to ensure that you do/don't have a policy already that will match the traffic.
You can also access this feature via the CLI if you aren't running one of the newer releases that exposes this feature in the GUI by building out the traffic flow with the test security-rulebase-match command.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-09-2021 12:13 PM
Just in case you are still interested in filtering the security policy based on multiple criteria. Actually this is possible. You can click on the drop down in the objects to add them to the filter or only to see the syntax to create a filter. For example for filtering based on a specific source object, destination object and service object you can use the following:
(source/member eq 'OBJECTNAME') and (destination/member eq 'OBJECTNAME') and (service/member eq 'SERVICEOBJECTNAME')
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-10-2021 03:47 AM
@getjamshedkhan what picture would you like to see (as I provided the filter syntax already in the last comment)?
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-10-2021 04:24 AM - edited 07-10-2021 04:33 AM
perhaps a picture of you Mr Remo... ha ha..
here's one...
additional options...
Tags: (tag/member eq 'tagname')
Name: (name contains 'unlocate-block')
Type: (rule-type eq 'intrazone|interzone')
Source Zone: (from/member eq 'zonename')
Source Address: (source/member eq 'any|ip|object')
Source User: (source-user/member eq 'any|username|groupname')
Hip profile: (hip-profiles/member eq 'any|profilename')
Destination Zone: (to/member eq 'zonename')
Destination Address: (destination/member eq 'any|ip|object')
Destination User: (destination-user/member eq 'any|username|groupname')
Application: (application/member eq 'any|applicationname|applicationgroup|applicationfilter')
Service: (service/member eq 'any|servicename|application-default')
URL Category: (category/member eq 'any|categoryname')
This is a destination category, not a URL filtering security profile
Action: (action eq 'allow|drop|deny|reset-client|reset-server|reset-both')
stolen from here....
https://live.paloaltonetworks.com/t5/blogs/tips-and-tricks-filtering-the-security-policy/ba-p/163250
and here is @BPry suggestion which gets my vote...
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-10-2021 05:19 AM
@Mick_Ball : D
(disabled eq 'yes') is missing in that list ... and also one for security profiles and logforwardingprofiles but this I don't know out of my head : P
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-11-2021 05:26 AM
You can do this from the Policies Tab and then click on Security to show list of Security Policies configured. Then at the bottom right of this page you can see "Test Policy Match" button. By clicking on that you can search the policy as per your exact requirement.
- 13991 Views
- 7 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Multiple High/Critical Alert Detected via Port 18264 | Possible FP in General Topics
- Multiple High/Critical Alert Detected via Port 18264 | Possible FP in VirusTotal
- FortiGate 501E & FG1101F equivalent Palo Alto model (below PA-5000) in General Topics
- Move Firewall from one Hierarchy device group/template to another hierarchy device group/template in panorama in Panorama Discussions
- Not able to log XFF (Actual Client IP) in PaloAlto Logs even when we enable XFF and URL filtering profile in Palo's in Next-Generation Firewall Discussions