- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
How to bound an ACL to GP VPN client
- LIVEcommunity
- Discussions
- General Topics
- Re: How to bound an ACL to GP VPN client
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-27-2016 03:25 PM
Hello
i have a need to provide a contractor with VPN access to certain resource on internal network (let’s call them 10.20.1.0/24)
I have a working VPN GP/Portal and contractor can connect to VPN with no issue. But contractor is allowed to access all internal resources not just 10.20.1.0/24
I have setup a GP policy (allow access from VPN zone to internal zone, destination 10.20.1.0/24 only), put that policy above generic VPN (allow all) and when user logs in, this policy is not hitting; instead default policy (which will allow al AD users to login) is utilized.
We are using MFA for authentication, AD has user contractor created, all looks fine. For testing i created another GP portal with local authentication, put user into local group and he is able to conenct but still not prevented from accessing internal resources.
The question is - how can i bound a ACL into VPN access policy? I know in other vendors it was mater of assigning ACL to VPN profile that can get pushed down to the user when they connect to VPN.
Apprecaite valuable inputs.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-27-2016 11:24 PM
Usually companies have 2 AD groups.
VPN Users
VPN Users third party
Policy that permits traffic from Globalprotect zone to LAN has only VPN Users group attached.
VPN Users third party has no default access to lan (ok maybe towards domain controller to auth and resolve dns).
And then you add specific sec policies to every contractor who needsd access to your network.
In your case it might be temporary step to create top rule to allow from this user to access resource you need and second rule below it to block anything else from that user (don't forget to put his username to user field).
If you have 0.0.0.0/0 route towards your network then you probably want to allow contractor to access wan zone aswell not to cut his internet 🙂
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-27-2016 11:24 PM
Usually companies have 2 AD groups.
VPN Users
VPN Users third party
Policy that permits traffic from Globalprotect zone to LAN has only VPN Users group attached.
VPN Users third party has no default access to lan (ok maybe towards domain controller to auth and resolve dns).
And then you add specific sec policies to every contractor who needsd access to your network.
In your case it might be temporary step to create top rule to allow from this user to access resource you need and second rule below it to block anything else from that user (don't forget to put his username to user field).
If you have 0.0.0.0/0 route towards your network then you probably want to allow contractor to access wan zone aswell not to cut his internet 🙂
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-28-2016 07:59 AM
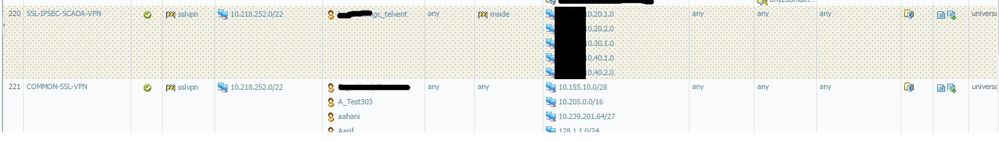
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-28-2016 09:39 AM
Those destinations that you covered with black box.
Are they address objects?
They have 0 at the end so I assume they have some subnetmask also set?
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-28-2016 09:40 AM
Well, it is kind of hard to grasp to the logic that i need to create a deny rule to everything else in order to limit access to certain resources, as a separate policy. Anyhow, thanks for your suggestion, i managed to get it going by following your suggestion, moving two VPN policies (allow, deny) above a common policy, and applying it to contractor's AD username.
Thanks
- 1 accepted solution
- 4065 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- recv rst from server or recv from zero win from server in General Topics
- Global Protect Connectivity Issue in GlobalProtect Discussions
- Strange Gateway change issue on network with Prisma Access GP Client in GlobalProtect Discussions
- GlobalProtect Agent constantly 'Not Responding'. in GlobalProtect Discussions
- GlobalProtect Always-On (6.3.3-c711) – Users Stuck in “Connecting” State but Still Have Internet Access in General Topics



