- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
HTTPS and SSH Traffic Is Not Working
- LIVEcommunity
- Discussions
- General Topics
- Re: HTTPS and SSH Traffic Is Not Working
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
HTTPS and SSH Traffic Is Not Working
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-09-2018 08:10 PM
Hello,
I’m new to the Palo Alto community. I’m hoping someone would be able to help me with this problem we are having.
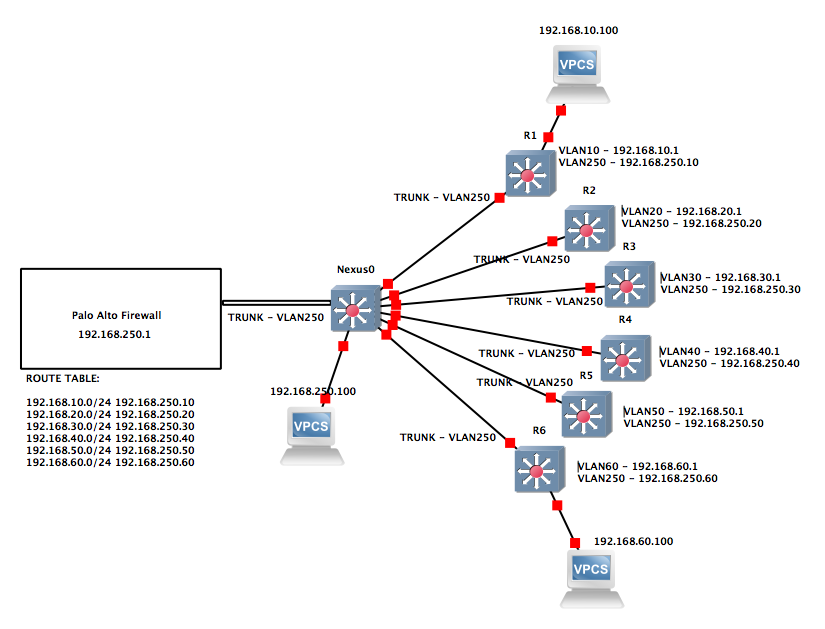
We have a Palo Alto PA3060 firewall that has a Layer 3 interface configured with a sub-interface that is also Layer 3 and tagged with VLAN250. The sub-interface is assigned an IP address of 192.168.250.1.
On the other end of the link is a Cisco Nexus switch. It’s interface is configured as a switchport trunk. The trunk has formed successfully between the Palo Alto firewall and the Cisco Nexus switch.
Conncected off the Cisco Nexus switch are 6 more Cisco Nexus switches. Each of these 6 Cisco Nexus switches are configured as a router for a network that is unique to each switch. See the attached network drawing for reference.
Below are the networks configured on each Cisco Nexus switch:
R1 - 192.168.10.1/24
R2 - 192.168.20.1/24
R3 - 192.168.30.1/24
R4 - 192.168.40.1/24
R5 - 192.168.50.1/24
R6 - 192.168.60.1/24
The Palo Alto firewall, the Cisco Nexus switch that is trunked to it, and the links to each of the 6 Cisco Nexus switches are all configured for the 192.168.250.0/24 network. The reason we have a middle switch in between the firewall and the 6 Cisco Nexus switches is because we are utilizing the 2x 10gig ports on the Palo Alto firewall. If we were to connect each of the 6 Cisco Nexus switches directly to the firewall, we would only be able to use the 8x 1 gig ports on the firewall (if this is incorrect, please let me know.) In order to get routing to work, each of the 6 Cisco Nexus switches has a SVI that has an IP address on the 192.168.250.0 network. The Palo Alto firewall has a static route for each network that points to the respective 192.168.250.0 address on the Cisco Nexus switch.
With all that being said, I am able to ping from a laptop connected to VLAN10 to the web server connected to VLAN60. The laptop in VLAN10 can also ping any of the 192.168.250.x addresses. The laptop in VLAN10 can also open a web page from the server in VLAN60. However, a laptop connected to VLAN250 is unable to access that same webpage on the server in VLAN60. The laptop connected to VLAN250 is also not able to SSH to 192.168.10.1, 192.168.20.1, 192.168.30.1, 192.168.40.1, 192.168.50.1, or 192.168.60.1. The laptop connected to VLAN250 is able to ping all the devices though.
The firewall sees all the ICMP traffic as "intrazone" since its leaving R1 on the 192.168.250.10 interface and entering R6 on the 192.168.250.60 interface. I am not seeing any HTTPS or SSH traffic in the Monitor view on the firewall.
Does anyone have any idea why this would be happening? It's not a routing issue from what I can tell as I can ping all devices from anywhere on the network. If you have any questions or need something clarified, just let me know. Thanks in advance for your help in this matter.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-10-2018 06:52 AM
Just out of curiosity, why wouldn't you do L3 routing for the associated R1-R6 switches on your Nexus switch and then just point the traffic from the PA to your Nexus switch and let the aggregation layer do the routing?
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-10-2018 11:31 AM
Our project manager has a specific requirement that any routing leaving one of the R1-R6 switches must be handled by the PA firewall. The justification behind this is that he wants the firewall to be able to log the traffic that is leaving one switch and is destined for a device connected to a different switch.
Let me know if this makes sense or if you have a different idea of how to implement this then what we are currently doing.
Thanks!
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-10-2018 12:11 PM
In that case I actually wouldn't do this how you have it. What I would do is bring VLANs 10,20,30,40,50,60 to the aggregation switch, then I would utilize sub-interfaces to make the PA the default gateway of each VLAN. This simplifies routing substantially and you wouldn't have to make any physical cabling changes so you could continue to utilize the 10G interfaces on the PA.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-10-2018 12:20 PM
Hello,
I agree with @BPry, also you would be able to write policies around the differetn vlans and what traffic can pass, etc.
Are you using ACI? If yes you could then ensure all traffic is routed via the PAN and acheive the same thing.
Hope that makes sense.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-11-2018 03:49 PM
Thanks for the advice @BPry and @OtakarKlier. After doing some more reasearch, it appears the initial problem was related to asymmetric routing. Implementing the solution that you all recommended eliminates this problem though.
Thanks again!
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-11-2018 03:51 PM
I am not familiar with ACI. I will do some research into it and see if that's something we should implement for our project. Thanks!
- 5604 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Unable to block download and upload for chatgpt and messengers in Next-Generation Firewall Discussions
- Hotspot Shield VPN still works even though traffic logs show deny – Palo Alto Firewall in General Topics
- No ping response from AAD in Next-Generation Firewall Discussions
- Azure to OnPrem Connectivity issue in Next-Generation Firewall Discussions
- Discord voice chat no longer connecting after PA-440 install in General Topics