- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Identifying unknown-tcp in Monitor tab
- LIVEcommunity
- Discussions
- General Topics
- Re: Identifying unknown-tcp in Monitor tab
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Identifying unknown-tcp in Monitor tab
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-30-2014 11:48 AM
Hello,
We have a PA-3020 running 6.0.3. Basically we have iSCSI replication set up between two sites. When I pull up the traffic in the Monitor tab I see the picture below. Even though iSCSI traffic is defined in the Applications section I tried creating another app to identify it but still see the "unknown-tcp" traffic show up. Is there something I am missing or is it not possible to change what it pulls up in Monitor?
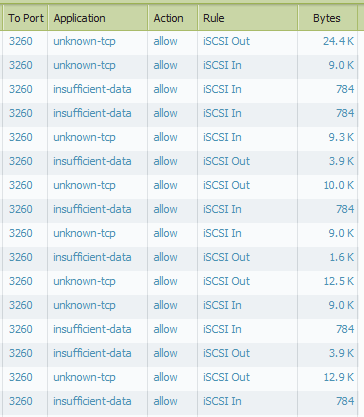
- Labels:
-
App-ID
-
Configuration
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-30-2014 12:27 PM
A reference DOC for this : Incomplete, Insufficient data and Not-applicable in the application field
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-30-2014 02:39 PM
Hey Hulk,
Is there a way though to tell the Palo that any unknown-tcp traffic on port 3260 from specific zones will be classified as iSCSI?
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-30-2014 02:42 PM
Custom app signature
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-30-2014 02:49 PM
Hello Clint,
As J.liu said, you need to configure a custom application signature to identify traffic on port 3260. Secondly, need a security policy in place from specific zones to allow that traffic.
Hope this helps.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-30-2014 05:15 PM
For iSCSI, I would be using an application override, essentially fast-pathing it which is what you would want to do with low-latency traffic.
The CNSE Study Guide page 34 gives the config steps.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-30-2014 07:24 PM
Hello Clint,
As per my understanding, the default application iSCSI is using TCP 3260. Then, why you want to use a custom app for this..? Better, you should use the previously mentioned DOC to get the exact reason.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-31-2014 05:32 AM
Hey Hulk,
Honestly I don't know why it is not identifying the traffic as iSCSI. It might be something proprietary with the vendor that is preventing the Palo from recognizing it even though it is coming across on 3260. I just want to be able to see in the reports that it is iSCSI. I will most likely end up programming both solutions.
Thanks for the answers, guys. I'll give it a try today.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-31-2014 10:18 AM
Hello Clint,
According to the screenshot you have attached here, it looks like the amount of data transferred between the Server and client is very low ( few KB). PAN firewall need at least 2000 Bytes of application data or minimum 4 packets to identify an application signature correctly. So, could you please check how many packets has been exchanged through those sessions.

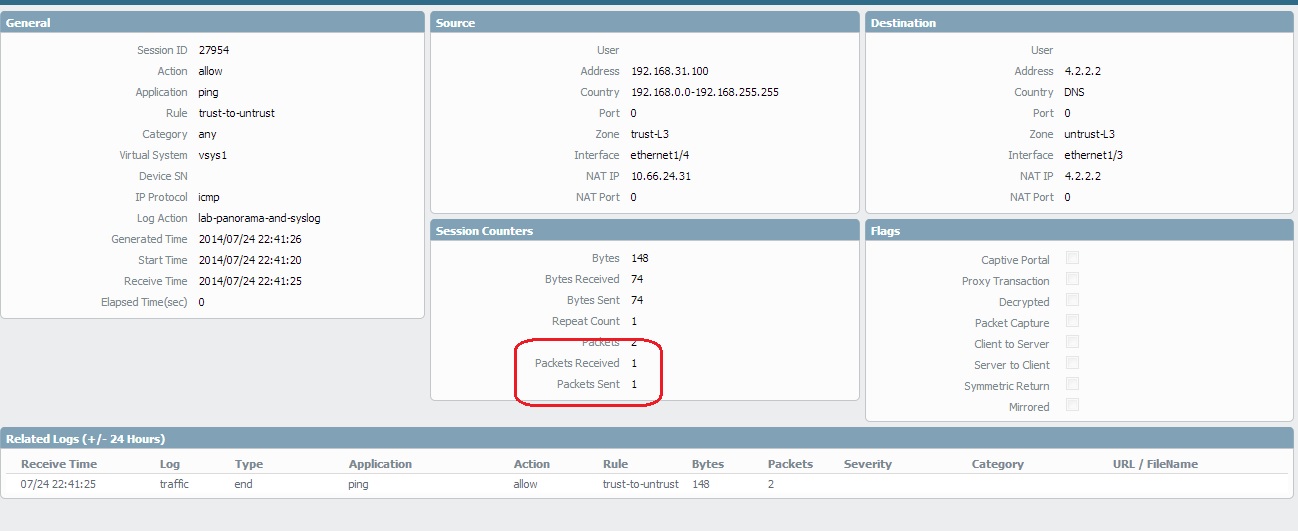
Insufficient data in the application field
Insufficient data means that there was not enough data to identify the application. So for example, if the 3-way TCP handshake completed and there was one data packet after the handshake but that one data packet was not enough to match any of our signatures, you would see insufficient data in the application field of the traffic log.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-31-2014 11:45 AM
I think there is something proprietary going on. I created a custom app signature with tcp/3260, created an allow rule and the traffic stopped transmitting altogether but I wasn't getting any deny entries. I'm just guessing but maybe when it isn't let through as is the Palo possibly strips out whatever proprietary info the data has and makes it unreadable to the iSCSI equipment on the other side. I haven't tried the application override rule yet though.
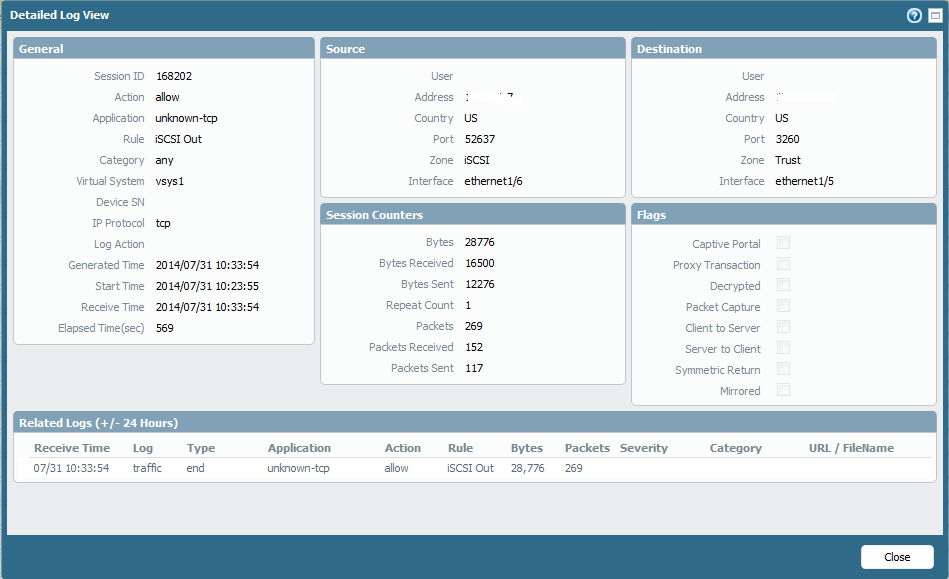
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-31-2014 12:53 PM
Hello Clint,
It's looks like the firewall passing a good amount of traffic, but still not able to identify the correct application-signature. Do you have a chance to take a packet capture. We can relay that PCAP through a LINUX REPLAY server and let you know if you need to contact with PAN support to open an App-ID BUG.
In the mean time, you may also try app-override once.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-15-2015 02:31 PM
Did you ever get this one resolved? I have a newly configured PA-500 and noticed the same issue for our iSCSI traffic. It is a Dell EqualLogic. There is already a Application ID for iscsi for tcp/3260; however in our QoS reports it is shown as unknown-tcp
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-16-2015 06:20 PM
For traffic like iSCSI your best bet is to get this into a segregated vlan that does not transit routers and firewalls if at all possible.
If it must transit the PA, create an application override to improve performance and insure there is a little latency as possible on this traffic.
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-23-2015 08:52 AM
Hey Steven,
iSCSI traffic has been segregated into its own network (own switch); however, we do send bits over our firewall/routers for replication. The traffic is coming and going between our network here and our offsite location. As one could imagine, this data is appearing in all of the reports and typically on the top5 due to the about of bits being sent offsite (for DR).
- 8580 Views
- 13 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Humps and bumps with the Palo Alto firewall integrated User-ID agent and Active Directory. in General Topics
- FW loses user mapping stop matching rule suddenly in General Topics
- URL Filtering Rule-Allowed Users to websites stops working for a few seconds. in General Topics
- Identifying unknown-tcp in Monitor tab in General Topics
- PA5020 and Proxy Server in General Topics



