- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Inbound decryption working/not?
- LIVEcommunity
- Discussions
- General Topics
- Inbound decryption working/not?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-06-2021 03:57 PM
2 web servers, inbound decryption for both, one working and other does not and are using same wildcard cert.
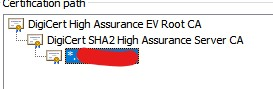
Bold are the only differences I see between 2. I don't know why working server without decryption shows the root instead of intermediate SHA2 certificate or vice a versa. However if i see the cert in browser it looks the same for both servers.
Also not sure why the signature type is different and also not sure if that can be controlled in Apache config. Traffic to both is from same test client.
---------------------------------------------
Server A without Decryption
PS C:\Users\whoami\Downloads\New folder (7)\openssl-1.1.1k-win64> .\openssl.exe s_client -connect webpac.test.ca:443 -brief
depth=2 C = US, O = DigiCert Inc, OU = www.digicert.com, CN = DigiCert High Assurance EV Root CA
verify error:num=19:self signed certificate in certificate chain
CONNECTION ESTABLISHED
Protocol version: TLSv1.2
Ciphersuite: ECDHE-RSA-AES256-GCM-SHA384
Peer certificate: C = CA, O = TEST, OU = IT, CN = *.test.ca
Hash used: SHA256
Signature type: RSA
Verification error: self signed certificate in certificate chain
Supported Elliptic Curve Point Formats: uncompressed:ansiX962_compressed_prime:ansiX962_compressed_char2
Server Temp Key: ECDH, P-256, 256 bits
Server A with Decryption
depth=0 C = CA, O = TEST, OU = IT, CN = *.test.ca
verify error:num=20:unable to get local issuer certificate
depth=0 C = CA, O = TEST, OU = IT, CN = *.test.ca
verify error:num=21:unable to verify the first certificate
CONNECTION ESTABLISHED
Protocol version: TLSv1.2
Ciphersuite: ECDHE-RSA-AES256-GCM-SHA384
Peer certificate: C = CA, O = TEST, OU = IT, CN = *.test.ca
Hash used: SHA256
Signature type: RSA
Verification error: unable to verify the first certificate
Server Temp Key: ECDH, P-256, 256 bits
Server B without decryption
depth=1 C = US, O = DigiCert Inc, OU = www.digicert.com, CN = DigiCert SHA2 High Assurance Server CA
verify error:num=20:unable to get local issuer certificate
CONNECTION ESTABLISHED
Protocol version: TLSv1.2
Ciphersuite: ECDHE-RSA-AES256-GCM-SHA384
Peer certificate: C = CA, O = TEST, OU = IT, CN = *.test.ca
Hash used: SHA256
Signature type: RSA-PSS
Verification error: unable to get local issuer certificate
Supported Elliptic Curve Point Formats: uncompressed:ansiX962_compressed_prime:ansiX962_compressed_char2
Server Temp Key: ECDH, P-256, 256 bits
Server B with decryption
Server B with decryption
30632:error:14094410:SSL routines:ssl3_read_bytes:sslv3 alert handshake failure:ssl\record\rec_layer_s3.c:1544:SSL alert number 40
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-07-2021 07:47 AM - edited 08-07-2021 07:53 AM
It's the RSA-PSS signature which isn't supported, disable this on the server.
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000PMR7CAO
They are supported from version 10, but only for TLS 1.3 I believe.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-07-2021 07:47 AM - edited 08-07-2021 07:53 AM
It's the RSA-PSS signature which isn't supported, disable this on the server.
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000PMR7CAO
They are supported from version 10, but only for TLS 1.3 I believe.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-13-2021 03:14 PM
@dmifsud Thanks. This is what I had suspected. This is what worked for us on apache.
SSLOpenSSLConfCmd Curves secp384r1:prime256v1
SSLOpenSSLConfCmd SignatureAlgorithms ECDSA+SHA512:ECDSA+SHA256:RSA+SHA512:RSA+SHA256
- 1 accepted solution
- 3708 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Prisma Access Explicit Proxy — Anti‑Spyware behavior when DNS bypasses Prisma (logging subtype + test methodology) in Prisma Access Discussions
- Unable to block download and upload for chatgpt and messengers in Next-Generation Firewall Discussions
- Decryption suddenly failed for all Webpages using Sectigo Certs in General Topics
- Chatgpt enteprise login only in Next-Generation Firewall Discussions
- web file blocking in Next-Generation Firewall Discussions