- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
IP Wildcard Mask Address Objects
- LIVEcommunity
- Discussions
- General Topics
- Re: IP Wildcard Mask Address Objects
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
IP Wildcard Mask Address Objects
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-06-2022 05:17 PM
Hey,
This properly confuses me every time I look at it. Is anyone able to explain in very simple terms how to work out what the mask should be?
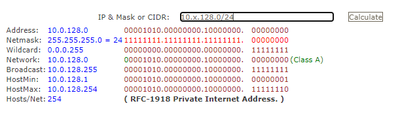
For example: We have an IP scheme that looks like 10.x.128.0/24 where the x changes for each site. We have been using an IP Wildcard address object of 10.128.128.0/0.127.127.255 which seems to have been working for sites 10.[128-201].128.0/24 but now we have a site that uses 10.224.128.0/24 and the wildcard address object does not seem to match it.
What is our address object of 10.128.128.0/0.127.127.255 actually covering?
How can I understand easily how to work out what a mask should be?
Thanks!
Shannon
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-07-2022 06:20 AM
An easier way of thinking about ACL wildcard mask is reversing what your traditional subnet statement would be. So where a subnet mask of 10.0.0.0/255.255.255.0 would allow for 10.0.0.0-10.0.0.255, a wildcard mask would actually be 0.0.0.255. Essentially stating that you want the wildcard to account for 10.0.0.0-10.0.0.255.
In your given example with 10.128.128.0/0.127.127.255 as a wildcard mask you'd be allowing 10.128.128.0-10.255.255.255.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-21-2022 12:21 PM
Thanks for the response. That is how I thought it was but in initial testing traffic did not seem to match as expected. This is for a new site which is not live yet so I will organize another test when devices are available in the relevant subnets.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-21-2022 12:54 PM
Hello,
Check the logs on the subnet (far) side of the network that is not working. Also check the site it cannot reach and make sure the routes are being distributed to that location.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-18-2022 12:20 AM
Routing can be tested via "test routing fib-lookup" command line command. With the same test command, you can also check the security policy match for the traffic.
Also remember - You can use an address object of type - IP Wildcard Mask only in a Security policy rule.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-21-2022 07:51 AM
It's not quite as easy as it may seem with the wildcard mask you're using. You need to understand how the wildcard mask works to figure out which subnets will be matched.
If your wildcard mask was 0.127.255.255, then everything from 10.128.128.0-10.255.255.255 would match. But your mask is 0.127.127.255, which means some subnets are not going to match in that range.
You'll need to do some binary comparisons to figure out what matches and what doesn't. The matching logic is opposite of subnet masking.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-21-2022 10:14 AM
Yeah thanks - this is my challenge. I am wanting to find an easy/repeatable way of working out what a mask covers, and also what mask would be required to cover a certain range.
Any tips or tools that can be used to do this easily without going through and trying to work out binary and correlating it?
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-22-2022 06:33 AM
Online calculators don't provide for unusual wc masks like you have. I don't know of any that would make it easier in this case.
Do you know why it was set this way originally? Any reason you can't change to 0.127.255.255, which would simplify knowing what would match? Or you could create a new object that will match 10.224+
How is that object being used? You're matching on a lot of potentially unnecessary addresses.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-22-2022 09:30 AM
Yeah, that is the challenge; we're not just trying to match on standard CIDR's so the traditional calculators don't seem to cover our scenario's.
We have a number of sites that use a common scheme for IP addresses, we are wanting to use these wildcards to accurately match traffic for all sites without needing to create individual objects for each site/network. e.g.
Site A:
Corp Clients = 10.224.10.0/24
Corp WiFi = 10.224.88.0/24
Corp Security = 10.224.26.0/24
SCADA = 10.224.128.0/24
PLC = 10.224.129.0/24
Management = 10.224.3.0/24
etc x 20ish
Site B:
Corp Clients = 10.225.10.0/24
Corp WiFi = 10.225.88.0/24
Corp Security = 10.225.26.0/24
SCADA = 10.225.128.0/24
PLC = 10.225.129.0/24
Management = 10.225.3.0/24
etc x 20ish
So the 2nd Octet changes for each site, but the 3rd octet is always the same. We want wildcard masks that match the different address objects (10.x.10.0/24, 10.x.88.0/24) etc. so we only need one address object in the policies for all sites, rather than creating 50-100 address objects for each network to cover all the sites.
To complicate it further we only want to look at addresses where the 2nd octet is 128-255 as lower numbers are unrelated to this use case.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-27-2023 04:25 PM
Compile this in Delphi Pascal and you have yourself a discontinious wildcard mask calculator 🙂 🙂
unit main;
interface
uses
Winapi.Windows, Winapi.Messages, System.SysUtils, System.Variants, System.Classes, Vcl.Graphics,
Vcl.Controls, Vcl.Forms, Vcl.Dialogs, Vcl.StdCtrls, System.RegularExpressions,
Vcl.Imaging.pngimage, Vcl.ExtCtrls;
type
TForm1 = class(TForm)
Memo: TMemo;
Edit1: TEdit;
Edit2: TEdit;
Button1: TButton;
Button2: TButton;
Image1: TImage;
procedure Button1Click(Sender: TObject);
procedure Button2Click(Sender: TObject);
private
{ Private declarations }
public
{ Public declarations }
end;
type
TIPAddress = record
Octets: array[0..3] of Byte;
end;
var
Form1: TForm1;
stoppressed : boolean;
implementation
{$R *.dfm}
function IPAddressToStr(const IPAddress: TIPAddress): string;
begin
Result := Format('%d.%d.%d.%d', [IPAddress.Octets[0], IPAddress.Octets[1], IPAddress.Octets[2], IPAddress.Octets[3]]);
end;
function IsValidIPAddress(const IPAddress: string): Boolean;
const
ValidOctetPattern = '^(([0-9])|([1-9][0-9])|(1[0-9]{2})|(2[0-4][0-9])|(25[0-5]))$';
var
Octets: TStringList;
I: Integer;
begin
Result := False;
Octets := TStringList.Create;
try
Octets.Delimiter := '.';
Octets.StrictDelimiter := True;
Octets.DelimitedText := IPAddress;
if Octets.Count <> 4 then
Exit;
for I := 0 to 3 do
begin
if not TRegEx.IsMatch(Octets[I], ValidOctetPattern) then
Exit;
end;
Result := True;
finally
Octets.Free;
end;
end;
function StrToIPAddress(const IPAddressStr: string): TIPAddress;
var
IPAddressStrs: TStringList;
I: Integer;
begin
IPAddressStrs := TStringList.Create;
try
IPAddressStrs.Delimiter := '.';
IPAddressStrs.StrictDelimiter := True;
IPAddressStrs.DelimitedText := IPAddressStr;
for I := 0 to 3 do
Result.Octets[I] := StrToIntDef(IPAddressStrs[I], 0);
finally
IPAddressStrs.Free;
end;
end;
procedure ExpandWildcardIP(const IPAddress, WildcardMask: string; Memo: TMemo);
var
IP, Mask: TIPAddress;
StartIP, EndIP: TIPAddress;
CurrentIP: TIPAddress;
I: Integer;
begin
if not IsValidIPAddress(IPAddress) or not IsValidIPAddress(WildcardMask) then
begin
ShowMessage('Invalid IP address or wildcard mask.');
Exit;
end;
IP := StrToIPAddress(IPAddress);
Mask := StrToIPAddress(WildcardMask);
for I := 0 to 3 do
begin
StartIP.Octets[I] := IP.Octets[I] and (not Mask.Octets[I]);
EndIP.Octets[I] := IP.Octets[I] or Mask.Octets[I];
end;
CurrentIP := StartIP;
while not CompareMem(@CurrentIP, @EndIP, SizeOf(TIPAddress)) do
begin
// Check if the current IP address matches the mask
for I := 0 to 3 do
begin
if (CurrentIP.Octets[I] and not Mask.Octets[I]) <> (IP.Octets[I] and not Mask.Octets[I]) then
Break;
end;
if I = 4 then
Memo.Lines.Add(IPAddressToStr(CurrentIP));
application.ProcessMessages;
if stoppressed then
begin
Memo.Lines.Add('Aborted...');
stoppressed := false;
exit;
end;
// Increment the IP address
for I := 3 downto 0 do
begin
Inc(CurrentIP.Octets[I]);
if CurrentIP.Octets[I] <> 0 then
Break;
end;
end;
end;
procedure TForm1.Button1Click(Sender: TObject);
begin
stoppressed := false;
ExpandWildcardIP(edit1.Text, edit2.text, Memo);
end;
procedure TForm1.Button2Click(Sender: TObject);
begin
stoppressed := true;
end;
end.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-27-2023 04:34 PM - edited 06-27-2023 04:56 PM
Or you can download the compiled wc.exe here:
jorlan72/Discontiguous-Wildcard-Masks-Calculator: Discontinious Wildcard Mask Callculator (github.co...
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-13-2024 06:57 AM
I just wanted to say thank you for doing that, it saved me time in confirming the wildcard mask I'd need!
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-06-2025 03:23 PM
Belated as I didn't see it at the time and have just stumbled over this again now but this is fantastic! Thanks Jorgen.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-01-2025 03:36 AM
Online version here: https://www.bitregn.no/wildcard-calculator
- 15818 Views
- 15 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Strata Cloud Manager with NGFW in Strata Cloud Manager
- API pagination for Panorama address object in General Topics
- Newsletter: Cloud Delivered Security Services, Oct-2025 in Advanced Threat Prevention Discussions
- Pull address object using XML API in General Topics
- SSL decryption exclusion or decryption policy in Web Proxy Discussions