- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
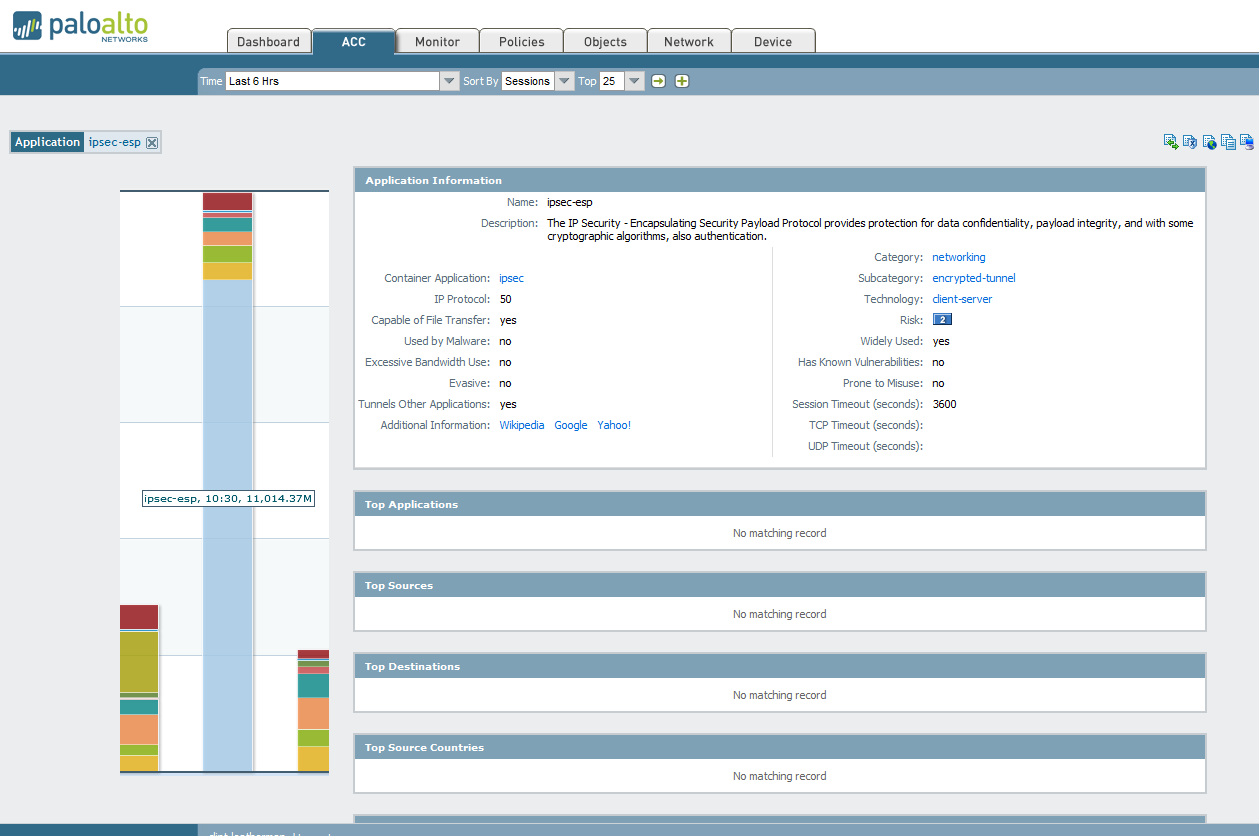
IPSec-ESP No matching record
- LIVEcommunity
- Discussions
- General Topics
- Re: IPSec-ESP No matching record
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2014 01:54 PM
The last few weeks I have noticed a large amount of traffic on the Network Monitor coming from IPSec-ESP. I moved several VPN tunnels off our old WatchGuard to our Palo Alto PA-3020 around the time this started. When I click on the application itself to filter it I see that it cannot identify anything about the traffic. Is this normal? Shouldn't it at least be able to identify the source or destination of the traffic?
- Labels:
-
Networking
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2014 03:21 PM
Hello Clint,
Is there any active session present on this PAN FW..? You may apply below mentioned CLI command:
> show session all filter protocol 50
ACC will give you the live session information, where traffic log will give you session information at the start or end.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2014 02:04 PM
Hello Clint,
ESP traffic is encrypted, hence, you would not be able to see the content of the packet. There might be an another possibility, if users are conneting through any VPN client, in that case also, firewall will identify as ESP traffic.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2014 02:07 PM
Hey Hulk,
Yeah that's what I figured but it just seems weird it can't even tell where it's coming from. No VPN clients in this case. Just regular VPN tunnels.
Thanks!
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2014 02:11 PM
Hi Clint,
To get source and destination information of traffic, go to Monitor > Traffic > Type application "IPSec-ESP". You will find number of logs.
You will have to take Educated guess to find out origin of the traffic.
If Origin of the traffic is your own firewall, than dont worry its intended IPsec Traffic.
If not than there should be something behind the firewall, try to locate IP.
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2014 02:20 PM
Hello Clint,
You are correct. The ACC report will not show the traffic details i.e source, destination etc. As HArdik said, you can filter traffic in Logs to get details information.
FYI:
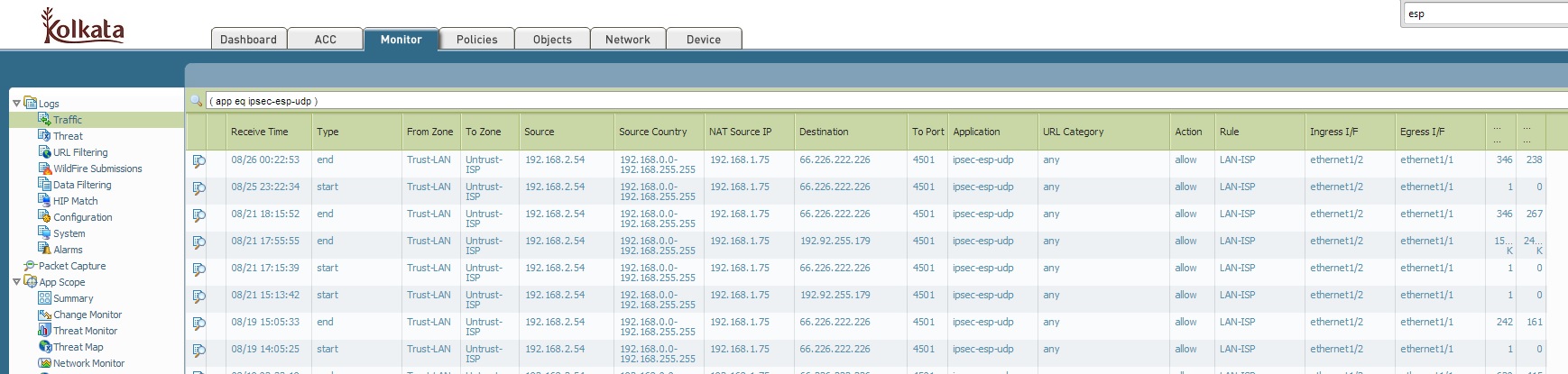
Hope this helps.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2014 02:29 PM
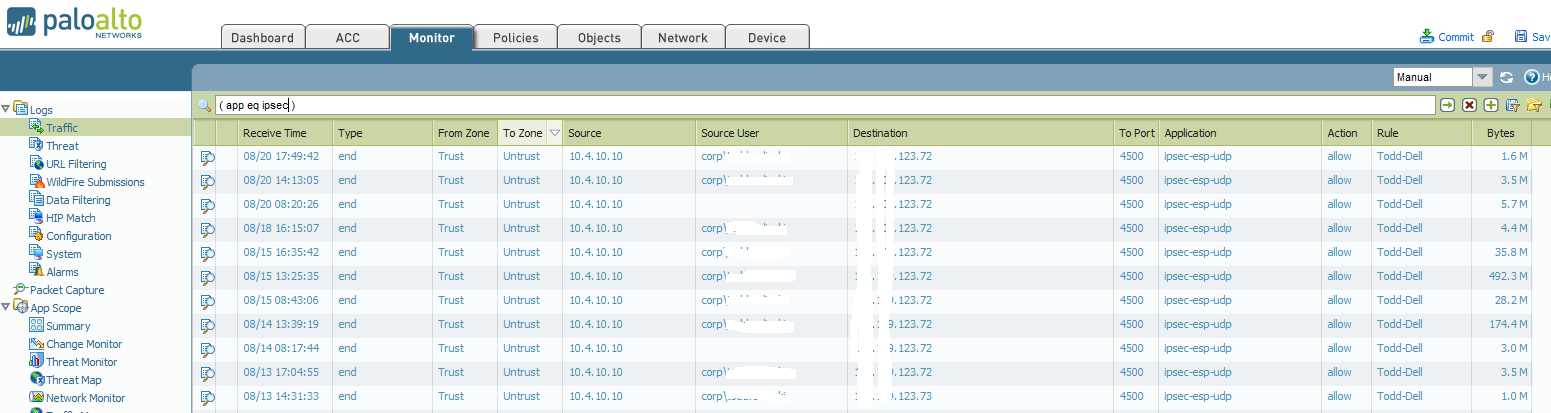
That's the thing is I see absolutely nothing with that application type that matches today's traffic and nothing in the amount I am seeing. The latest entry filtering by that app is six days ago.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2014 03:10 PM
Hello Clint.leatherman,
What version of PAN-OS are you running?
Are the VPN tunnel interfaces in a separate zone or part of your untrust zone?
Regards,
David
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2014 03:13 PM
Hey David,
We are running 6.0.3 and the tunnel interfaces are in their own zone.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2014 03:21 PM
Hello Clint,
Is there any active session present on this PAN FW..? You may apply below mentioned CLI command:
> show session all filter protocol 50
ACC will give you the live session information, where traffic log will give you session information at the start or end.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2014 03:53 PM
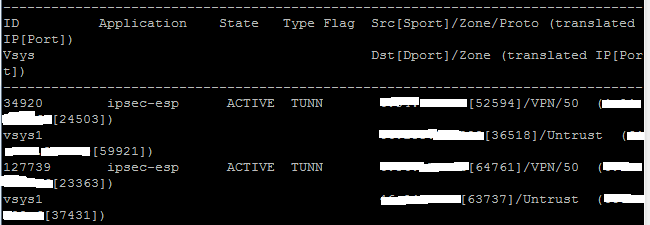
Yes I see about ten entries. If I filter the traffic monitor by the VPN zone I can see traffic destined for the different proxy-IDs. I only see that large amount of traffic classified as IPSec-ESP 2-3 times per day, sometimes early in the morning when no one is here. I have a feeling it is some backup job running on our SQL databases to a remote site but I just want to be sure.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2014 03:57 PM
Hulk is correct where the ACC will show you active sessions information and the traffic log will only show traffic information based on security rule log at start or end(default)?
So you would not see logs in traffic till session ends(tunnel goes down).
Following document explains better what you are seeing.
ACC Data is not in Sync with Traffic Logs
To determine what source/destination is causing traffic would need to look at ACC with source/destination zone for VPN at times you are seeing spike in traffic.
Regards,
David
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2014 03:58 PM
Hello Clint,
If you see the session type, it is "TUNN". So, this is not the FLOW session, which actually passes traffic.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2014 04:01 PM
Session type "TUNN" indicates an IPSec tunnel session. As soon as you will configure a VPN tunnel, the PAN firewall will assume a tunnel session for that address.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2014 04:04 PM
Thanks guys. This clarifies a lot.
One more question. When you say the tunnel going down to see the traffic do you mean completely down or does the Palo count the rekey as the tunnel going down even though it is just a moment or two?
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2014 04:24 PM
While it will be completely down. Rekey is a part of the IPSec algorithm, hence it would not be considered for session end ( according to my understanding![]() ).
).
Thanks
- 1 accepted solution
- 10394 Views
- 15 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Global Protect Connectivity Issue in GlobalProtect Discussions
- PA-415-5G not working with fresh T-Mobile SIM in General Topics
- Windows-Remote-Management & Implicit Use of Web-Browsing in General Topics
- PA Global Protect in GlobalProtect Discussions
- Problem with Conditional Task Not Matching XQL Output in Cortex XSIAM Playbook in Cortex XSIAM Discussions



