- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
IPSEC VPN Tunnel Problem
- LIVEcommunity
- Discussions
- General Topics
- Re: IPSEC VPN Tunnel Problem
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
IPSEC VPN Tunnel Problem
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-18-2012 09:26 AM
PAN PA2020 PAN OS 4.16
I have a point to point vpn setup from our company to another company that is hosting our financial application.
We have 10 different proxy IDs setup to limit subnet's that can access the vpn for example:
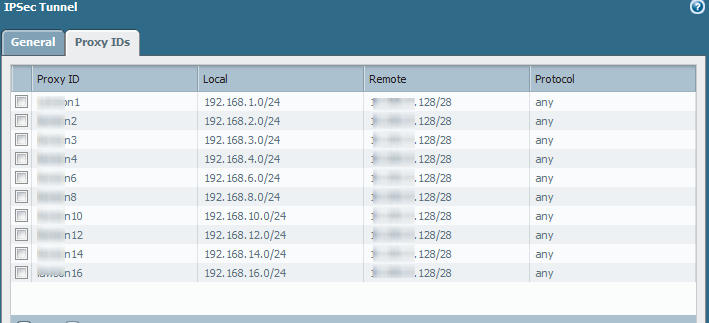
Almost everyday, all proxy ids can access the vpn tunnel with the exception of proxy id 2 or proxy id 3.
Any thoughts?
Thank you in advance...
- Labels:
-
Networking
-
Troubleshooting
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-18-2012 10:25 AM
What is the device on the other side of the VPN?
Do you see any errors in the system log? Monitor / Logs / System?
If the remote side is a CheckPoint, then it may be joining 192.168.2.0/24 and 192.168.3.0/24 into a larger subnet, 192.168.2.0/23.
--- UPDATE:
I tested this in my lab. The PAN with report the proxy IDs using during phase 2, even when the negotiation fails. This makes it much easier to determine if the other side has fat fingered a encryption domain / crypto-map ACL
Such a beautiful device.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-18-2012 12:03 PM
a> Check if the routes have been configured pointing to the tunnel interface.
b>Security rules allowing traffic between the inside and tunnel zone.
Also check if the peer device has a rule allowing this traffic.
Check traffic logs filtering the source and dest, include the columns bytes sent and received to see if PA is dropping the traffic or if we are not getting responses.
-Ameya
- 3678 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Unable to establish tunnel during Service Connection configuration (Details Added with Screenshot) in Prisma Access Discussions
- Palo Alto to Azure vpn tunnel fails at random in Next-Generation Firewall Discussions
- GRPC status UNAVAILABLE in intelligent offload in VM-Series in the Private Cloud
- Connectivity with Panorama in VM-Series in the Public Cloud
- Request Advice – BGP Failover Route-Based IPsec VPN With WatchGuard (WG) in Next-Generation Firewall Discussions



