- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Layer 2 to Layer 3 Connection , but on same Subnet and IP range?
- LIVEcommunity
- Discussions
- General Topics
- Re: Layer 2 to Layer 3 Connection , but on same Subnet and IP range?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Layer 2 to Layer 3 Connection , but on same Subnet and IP range?
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-04-2020 01:04 PM
We have a PaloAlto PA220 at work what is used for telephony/SIP traffic that I set up several months ago.
Upstream of the PaloAlto is a unmanaged L2 netgear switch what sits between the leased internet line, the PaloAlto , and a another non-PaloAlto firewall. I want to get rid of this unmanged L2 netgear switch and connect our other non-PaloAlto firewall and the Internet leased line directly into the PaloAlto.
The thing is is through the PaloAlto has a external IP of 5.X.X.36/28 and the non-PaloAlto firewall has a IP of 5.X.X.34/28, and following the guide linked below fails (commit fails) due to setting the VLAN interface IP to 5.X.X.34/28 overlaps and conflicts with 5.X.X.36/28. Both the PaloAlto and the non-PaloAlto firewall both use the same ISP gateway (5.x.x.33/28.)
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClKMCA0
How do I get around this issue and connect our non-PaloAlto firewall into the PaloAlto firewall so that the Layer 2 switch can be got rid off.
Regards: Elliott.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-05-2020 12:28 AM
If the other firewall has 5.X.X.34 , then it's going to conflict if both are the same?? Or are you getting rid of the other firewall?
Rob
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-05-2020 05:55 AM
The other firewall is our main corporate Checkpoint branded firewall and can not be got rid of. Yes it uses a IP on the same subnet and the same default gateway as the PaloAlto firewall.
I essentially want to integrate the layer 2 switch into the PaloAlto so the layer 2 switch is not needed anymore.
Regards: Elliott
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-05-2020 06:00 AM
I don't think you've provided enough information here for people to help you. A diagram would be nice. I am guessing you want to use your PA-220 as a switch just so you can remove some equipment. On the surface, you can do this but it sounds like a really bad idea. Is there a technical reason you want to remove this switch?
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-05-2020 06:59 AM
So the L2 Switch has the
Internet on one port.
PA on another port
Checkpoint on another port.
All there in the same vlan.
Personally that's how I intend my external infrastructure to be, I can then have multiple ISP's and trusted their part circuits on different VLANS going to any combination of firewalls.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-05-2020 08:24 AM
@RobinClayton so, I think the issue you are having is that you are trying to prestage the PA220 by creating the second interface in the same subnet before you deprecate the existing one... if this is the case that explains the error as PANOS will not let you do that in the same VR IIRC.
As for removing the L2 switch and directly connecting that should be OK, based on what we know at this point, so long as your upstream CP FW is not in HA and doesn't need a common L2 to accommodate...
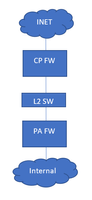
Assuming below is a simple representation:
The L2 switch should not be needed... could you just leave the configs as-is and directly connect the CP/PA FWs directly?
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-05-2020 12:13 PM
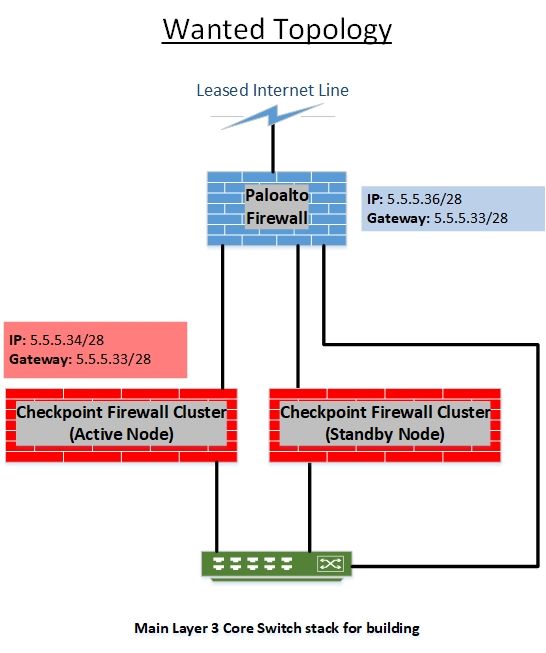
Please see below for the topology diagrams. It is to note the Checkpoint firewall can not be changed and is out of my control.
The PaloAlto firewall servers as the route for SIP/VOIP traffic, and the Checkpoint firewall servers as the route for all other traffic.
Current Topology:
Wanted Topology:
Regards: Elliott.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-05-2020 12:59 PM
If it were me, I would prefer the setup you currently have over the proposed. I'm still trying to see what you are trying to accomplish or gain here. I don't like forcing Layer 2 through a PAN. You can do it but I wouldn't unless I was forced.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-05-2020 03:35 PM
Hello,
In all honesty, I dont think your 220 could handle the traffic. And you might not have enough ports to do vwire plus you would still need a switch between the pan and leased line. If you made the PAN interfaces L2, you still need a L3 interface for it to route the sip traffic so you would need a L3 vlan interface for that.
However depending on the traffic through the CheckPoints, i still dont think the PAN could handle the traffic.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-06-2020 12:50 AM
Otakar eludes to the V-Wire, which would allow traffic to traverse the PA seamlessly, but in that scenario, as he points out, you would need bot a trusted and untrusted v-wire ports. And the untrusted v-wire and external interface still both need to connect to the Leased line somehow.
The present setup is really correct for most instances.
Or are you trying to get rid of £$ threat inspection licences on the checkpoint and put that into the PA??
Rob
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-06-2020 08:49 AM
I would agree with @RobinClayton @OtakarKlier @jeremy.larsen here... this is not simply getting rid of a switch but also redesigning your outbound traffic layer... today, specific traffic (SIP/VoIP) is directed via some kind of route engineering (I assume) to go thru the PA220 and the rest is engineered to go thru CP and bypass the PA220... the proposed design now puts the PA220 in line with the CP and capacity issues aside you still need a common L2 north/south of the CP FWs for HA to work and pushing that to the PA220 is just moving the same functionality to a new spot...
If full resiliency is required, you have HA on the CP FWs, then having redundant L2 switches north/south gets you there as a failure on either switch means use lose outbound connectivity regardless of the HA on the CP FWs.
On the capacity front it would be recommended to understand the traffic load/rates currently going thru the CP FWs and add that to what the PA220 is currently doing to see if it can handle the additional load, you still would have a SPOF as the PA220 is not in HA...
Lots of things to consider, perhaps reaching out to your SE to have a more detailed conversation on this would be a good next step.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-13-2020 07:29 AM
I should mention that what I want to do, we are currently doing with another/2nd PA-220 that we have that handles both the 1) gateway for our public Wi-Fi what 2) also feeds our main checkpoint firewall for another connection on the Checkpoint.
But in that case the Wi-Fi (using the PalAlto as the layer 3 router) and the connection to our Checkpoint Firewall (via a layer 2 to layer 3 connection on the Palo Alto) are using completely different subsets with their own distinct gateway.
I was hoping I could do the same thing with the PaloAlto PA220 that handles the SIP traffic and the Layer 2 connection from the unmanged switch to the Checkpoint firewall that both use the same subnet as originally proposed in this thread.
Regards: Elliott.
- 12913 Views
- 11 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- PA Global Protect in GlobalProtect Discussions
- Prisma Access with ECMP in Prisma Access Discussions
- Unable to Ping Palo Alto Interface – Connectivity Appears One-Sided in Next-Generation Firewall Discussions
- Azure Virtual Desktops integration with Global Protect nightmare in GlobalProtect Discussions
- Cortex Broker Mapper scans in Cortex XDR Discussions