- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Malware site and response page - problem
- LIVEcommunity
- Discussions
- General Topics
- Re: Malware site and response page - problem
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Malware site and response page - problem
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-08-2014 03:29 AM
Hello
Some time ago I created url-filtering profile:
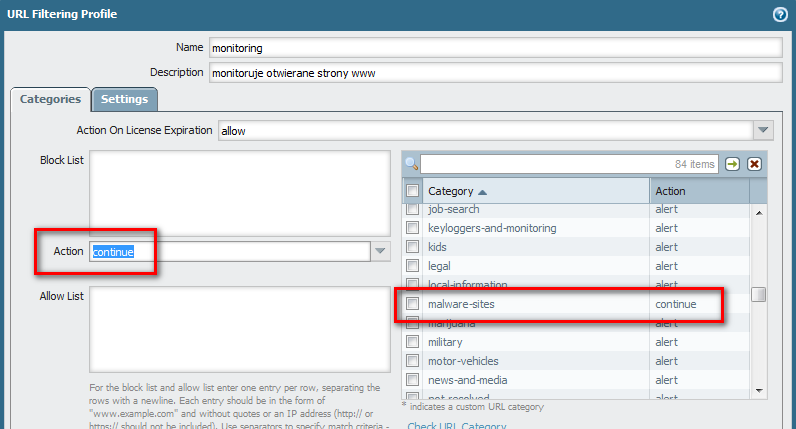
Today I found in wildfire report that someone try to download something from malware site, so I try to check is my configuration works as expected.
First of all I checked is it still a malware site:
admin@PA-200> test url sunrisebrowse.net
sunrisebrowse.net malware-sites (Base db) (I'm using BrightCloud URL Filtering)
so I started browser and I try to open "sunrisebrowse.net" after 30s or more browser wos redirected to:
and timeout was displayed in browser. I expected responce page insted of timeout...
I found the session:
| 61542 | undecided | ACTIVE FLOW ND 192.168.1.35[59936]/Lan_A/6 (192.168.1.35[59936]) |
| vsys1 | 8.34.112.54[6080]/captive-portal (127.131.1.1[6180]) |
admin@PA-200> show session id 61542
Session 61542
c2s flow:
source: 192.168.1.35 [Lan_A]
dst: 8.34.112.54
proto: 6
sport: 59936 dport: 6080
state: INIT type: FLOW
src user: unknown
dst user: unknown
s2c flow:
source: 127.131.1.1 [captive-portal]
dst: 192.168.1.35
proto: 6
sport: 6180 dport: 59936
state: INIT type: FLOW
src user: unknown
dst user: unknown
qos node: ethernet1/4.1, qos member Qid 0
match src interface: any
match src address: ('any ',)
start time : Mon Dec 8 11:26:16 2014
timeout : 30 sec
total byte count(c2s) : 206
total byte count(s2c) : 0
layer7 packet count(c2s) : 3
layer7 packet count(s2c) : 0
vsys : vsys1
application : incomplete
rule : captive-portal
session to be logged at end : False
session in session ager : False
session updated by HA peer : False
address/port translation : destination
nat-rule : NAT_Lan_A(vsys1)
layer7 processing : enabled
URL filtering enabled : False
session via prediction : True
use parent's policy : False
session via syn-cookies : False
session terminated on host : True
session traverses tunnel : False
captive portal session : True
ingress interface : ethernet1/4.1
egress interface : ethernet1/1
session QoS rule : N/A (class 4)
end-reason : aged-out
Ethernet interface for zone where is my workstation hasn't captiveportal option enabled.
Why this session is "rule : captive-portal", similar config works perfecly for wiruses, ie. when I try to downloaad Eicar sample I get responce page with warning.
What's wrong in my configuration? do I miss something?
Regards
SLawek
- Labels:
-
Configuration
-
Troubleshooting
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-08-2014 07:59 AM
Hi Slawek,
Based on the configuration you should not get captive portal page. And the redirect host ("http://8.34.112.54:6080/php/urlblock.php...) itself is IP address of sunrisebrowse.net, that is not expected either. Could you please confirm, what is the redirect host or ip you have configured under Captive Portal settings. Also can you change the action of malware site to block, commit and access the site one more time and verify you get the same results. Thank you.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-08-2014 09:29 AM
Before I post here this problem I tryed to chage action to block - same resoults
CP IP is 192.168.110.1 thats is a gatway IP of diffrenet zone/network than my workstation network.
Regards
SLawek
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-08-2014 11:56 AM
Your management profile on ethernet1/4.1 is set to Ping_Only.
Try activating "Response Pages" on the Management profile.
The connection you see is trying to go to 6080. That is the Captive Portal Response Page port.
As you can see on the Management Profile Help file:
The Response Pages check box controls whether the ports used to serve captive portal and URL filtering response pages are open on Layer 3 interfaces. Ports 6080 and 6081 are left open if this setting is enabled.
Let us know if that helped.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-08-2014 11:58 PM
How You can expain that on the same workstation Response Page is shoing properply when I try to download Eicar sample?
I changed profile for this interface (added response pages) but it dosn't help me, so I think is time for support...
Regards
Slawek
- 5010 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Palo Alto for email security in Next-Generation Firewall Discussions
- Newsletter: Cloud Delivered Security Services, Oct-2025 in Advanced Threat Prevention Discussions
- Cortex XDR triggers Code 10 on USB Audio despite exception - Vendor not selectable, need per-device allow without vendor or something in Cortex XDR Discussions
- Struggling to Unset Virtual Router from Interface via API – Manual Works, API Always Fails in General Topics
- Quarantined File Automatically Moved to Allow List from Block List after File Restore Action in Cortex XDR Discussions