- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
ms-update and MS Internet Explorer root CA
- LIVEcommunity
- Discussions
- General Topics
- ms-update and MS Internet Explorer root CA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-22-2013 07:46 AM
Hi,
In my company, we explicitely block the application ms-update to control workstations update policy.
But I realized that MS internet explorer tries to update its "root list sequence number" at each HTTPS connection.
The file that MS IE tries to access is at :
www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootseq.txt
In your opinion, what would be the best approach to block ms-update except this Internet Explorer access ?
Thanks.
- Labels:
-
App-ID
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-22-2013 08:38 AM
Hi
You can create a custom application based on the url information.
and create a security rule that allow this application and place it above the rule which deny the windows update.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-22-2013 08:38 AM
Hi
You can create a custom application based on the url information.
and create a security rule that allow this application and place it above the rule which deny the windows update.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-23-2013 07:51 AM
Hi,
Thanks for the tip. It works as expected.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-13-2014 08:13 AM
Hello Mattieb,
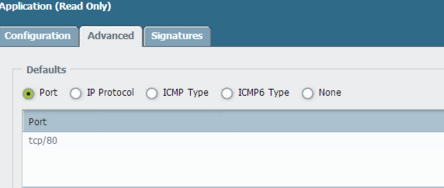
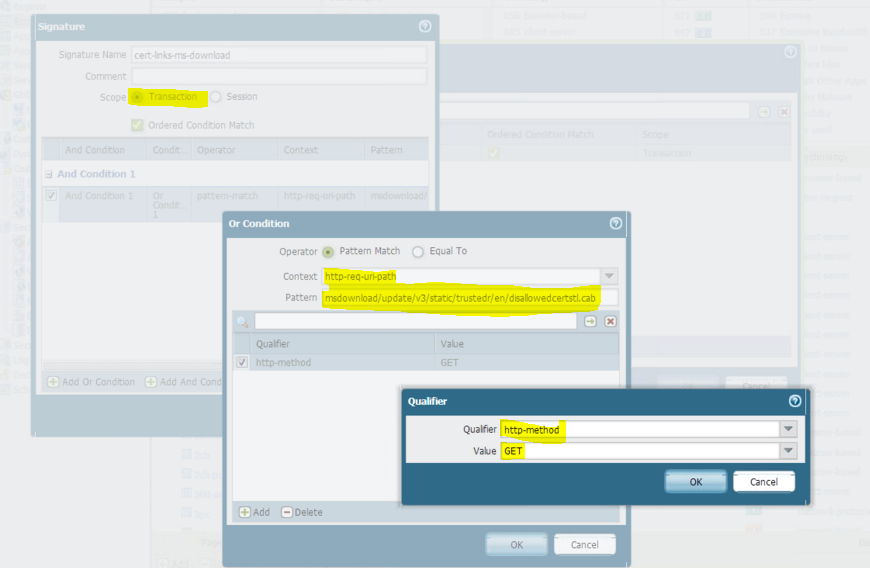
Have seen similar issue and I want to share some screenshots in creating a custom app just to make it easy if some one faces the issue.
Steps:
1> Create custom app. 2> Apply in a security rule before the rule which blocks MS-Update APP rule. 3> Clear any existing matching sessions so the new sessions to hit the new app.
Wireshark info:
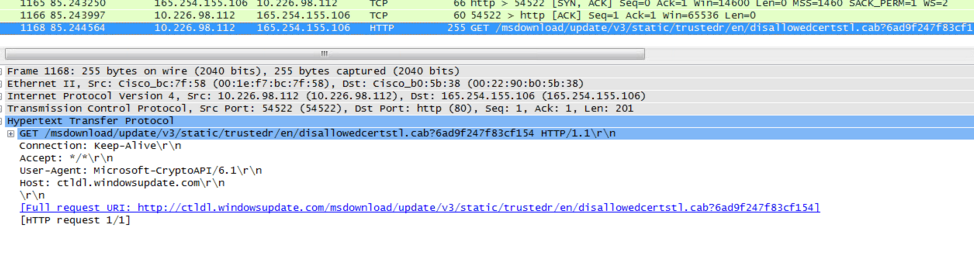
- 1 accepted solution
- 3789 Views
- 3 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Windows copy slow in Prisma SD-WAN Discussions
- Block IE in General Topics
- GP uses Microsoft Account connected to Windows 11 User | Can't declare actual VPN User in GlobalProtect Discussions
- Cortex Endpoint Isolation - Allowing Microsoft Intune in Cortex XDR Discussions
- Captive Portal not working on Google Chrome, Edge, Firefox on PAN-OS 10.1.0 in General Topics



