- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Need some guidance on the VM series implementation
- LIVEcommunity
- Discussions
- General Topics
- Re: Need some guidance on the VM series implementation
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Need some guidance on the VM series implementation
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-27-2020 12:35 AM
Hi there,
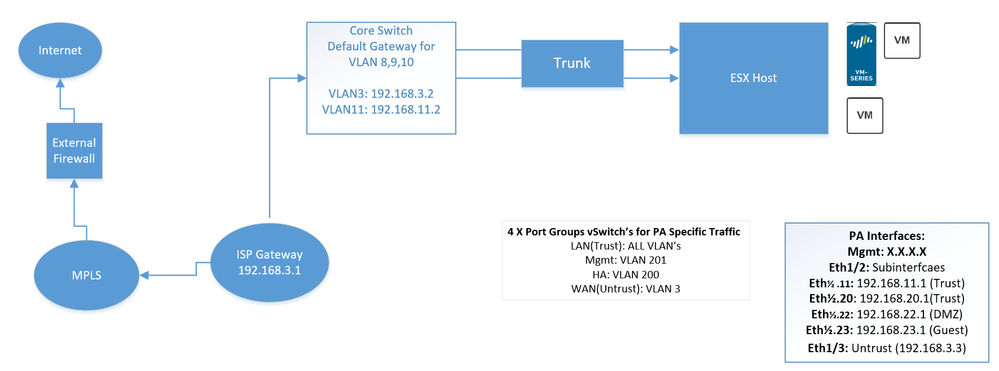
I have inherited the current network and need some help in replacing the firewall for like to like. We have a MPLS network connecting all our offices and an external firewall managed by the ISP. Traffic from all sites go out via the external firewall. I am replacing an old ASA with the PA-VM Series firewall as an internal firewall in one of our offices and experiencing issues with return traffic. Our core switch does routing for some of the vlans (subinterfaces on the core switch) and ASA does routing some of the vlans (subinterfaces for DMZ, guest,contractors vlans).
We have multiple ESX hosts and I am installing 2 PA instances on 2 different hosts in Active Passive set up. I have set up the PA's and added port groups on the ESX hosts and subinterfaces in the PA as explained in the diagram. I have a default route on the core switch to send all traffic to subinterface ( Eth1/2.11) as I want all traffic to out via PA. On the PA, I have a default route to Eth1/3 and also a static route to internal VLANS (to make PA aware of the rest of the VLAN's) This is still in testing mode and I would eventually enable RIP on the PA as the core switch runs RIP.
I also have a NO NAT policy because it's an internal firewall and a security policy to allow outbound traffic.
Issue: I can see traffic going out the untrust interface but firewall is dropping the return traffic. Packet capture shows that the return traffic ends up on the trust interface Eth1/2.11 and hence the packets are being dropped.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-27-2020 02:24 PM
Yes the core switch has layer 3 interfaces for VLAN3 and VLAN 11 as shown in the diagram ? The packet captures were done with the source IP of 192.168.20.10 from a VM on VLAN 20 which has gateway as another subinterface (192.168.20.1) on the firewall. Diagram updated. (VLAN 20 does not have a layer3 interface on the core)
The capture shows packet flow from the VM to its gateway 192.168.20.1 (Trust) out to Untrust and the Gateway (192.168.3.1)
Return traffic from 192.168.3.1 hits the core switch and is going back via the trusted interface 192.168.11.1 (VLAN 11) following the default route which is being dropped by firewall.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-28-2020 02:08 PM
Hello,
Check the traffic logs as you may have missed a policy?
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-28-2020 02:20 PM
Sounds like there is some asymmetric routing in the environment.
Are there any routes (static or dynamic) on the core switch to 192.168.20.0/24 or perhaps a summary route.
A traceroute from 192.168.20.10 and another traceroute from the destination should help identify any asymmetric routing paths in the environment.
- 3432 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Request Advice – BGP Failover Route-Based IPsec VPN With WatchGuard (WG) in Next-Generation Firewall Discussions
- Newsletter: Cloud Delivered Security Services, Aug-Sep, 2025 in Advanced WildFire Discussions
- Need to know different metrics part of network_point_metrics_bw API in Prisma SD-WAN Discussions
- Palo Alto VM-Series in Azure DMZ - AVS in VM-Series in the Public Cloud
- Fuel Workshop - Watch Now: Managing Your Palo Alto Networks Assets and User Accounts in General Topics