- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Need to allow service for Ping application
- LIVEcommunity
- Discussions
- General Topics
- Re: Need to allow service for Ping application
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Need to allow service for Ping application
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-27-2019 12:35 AM
Hi Team
We have configured the one Destination NAT policy. My requirement is Ping the NAT IP (Public IP) from the external network.
I have configured one security policy with application as 'ping' and service as 'any'.
For the above configuration, I can able to ping the Public IP from the external network. But I want to allow the specific service for Ping application.
Note : If I configured the service as "any or application-default", I can able to ping from the external network. If I mention particular service, I couldn't able to ping from the external network.
My question is, What is the service need to allow only for PIng application?
If you need any further information, please let me know.
Regards
Mohammed Asik
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-27-2019 11:56 AM
The correct way to enable all applications, is to use the service of "application-default".
So change from service of "any" to "application-default"
Thanks
Steve
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-28-2019 12:02 AM
Hi Steve
I had already configured as application default and I could able to ping from external network.
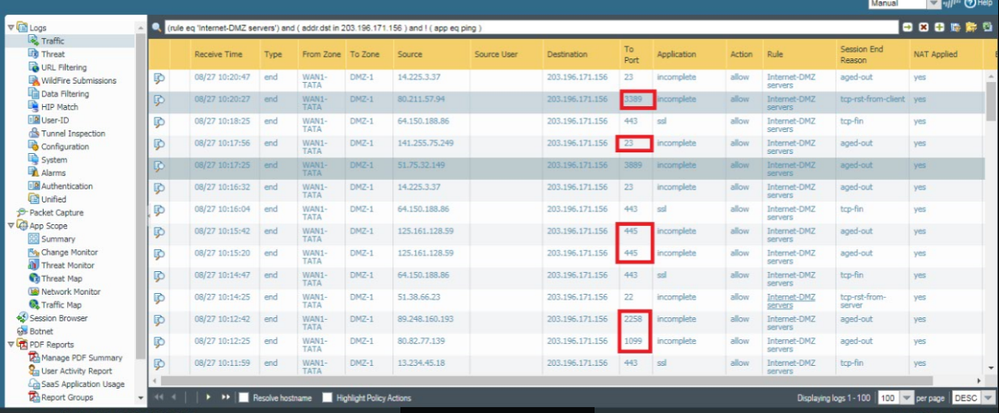
But the issue is, we are receiving the lot of unwanted ports hit the server. Due to this, Server load become high. So that only we want to mention the particular the ports in service.
I want to block the unwanted port hit from firewall itself which will not hit the server.
Could you suggest me?
Regards
Mohammed Asik
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-28-2019 12:22 AM
Hi Mohammed,
Seem you are on public IP range on both your wan and your DMZ. then if you just want to allowed ping. You should only have security rule like
from zone: WAN1-TATA
To zone DMZ-1
To IP 203.196.171.56
Application: ping
Service: Application default
Action: Allow
Your Internet-DMZServers rule should be TO LARGE 🙂
Incomplete mean, syn arrive to your server and your server never answer.
Rgds
V.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-28-2019 01:21 AM
Hi Vince
Incomplete mean, syn arrive to your server and your server never answer.
Yes you're correct, the syn arrived to the server. My requirement is syn should not reach the server, it should block from firewall.
How can we achieve it ?
Regards
Mohammed Asik
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-28-2019 01:26 AM
Hi,
No reason for syn on port TCP/445 to arrive on your server if you don't want it.
But it seem your security rule allow it.
what your security rule look like ??
Allow only app on application-default.
V.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-28-2019 02:22 AM
Hi Vince
Yes, In security rule I have allowed the application Ping , SSL, FTP and service as Application-default.
Since the unwanted ports are hit the server without allowing the mentioned port
Regards
Mohammed
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-28-2019 02:38 AM
Hi,
You have to know that before beeing able to indifty a complete app, your firewall nedd to first allow session's first packet.
Mean allowing syn / syn-ack /ack + first apcket.
At the beginning session identification is based on 5-tuple (source zone, source IP subnet, destination zone, destination IP subnet, destination port). Mean, based on this criterim, session match first security rule which allow these packet.
If your rule is on top, it can explain strange traffic in your log.
look: https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClS9CAK
Rgds
V.
- 28547 Views
- 8 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Palo Alto Networks PA- 450 Next‑Generation Firewall to maintain uninterrupted BSNL SIP trunk services in the event of a primary internet link failure. in Next-Generation Firewall Discussions
- Boradsign application not working when GP is connected in GlobalProtect Discussions
- GRPC status UNAVAILABLE in intelligent offload in VM-Series in the Private Cloud
- TELAM SERVICES IS STOPPED - CORTEX XDR in Cortex XDR Discussions
- Outlook and mapi-over-http in General Topics