- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
New PA user and currently concerned
- LIVEcommunity
- Discussions
- General Topics
- New PA user and currently concerned
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
New PA user and currently concerned
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-25-2017 02:52 PM
Hi
I am a new PA user, purchased a pa-850 and 2 x PA5220's
Adding these to my OSPF network, i have setup a policy "network protocols" that allows OSPF.
But for some reason in my log, I get OSPF time out session and aged out sessions and sessions that have 0 bytes.
So I contact support. after 2-3 weeks, they bring it up in their lab and I am told this is normal behaviour.
If its normal why do they need to lab it up, it should be in the documentation yes
Also for a next gen FW that doesn't understand OSPF, wow...... I am really reconsidering my choice in PA...
So is this standard for OSPF connections.
To be clear I believe the OSPF connection is okay, atleast from my other routers point of view, its just the way that the PA are logging it, I believe I haven't as yet put them into any situation where they could cause a problem ...
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-01-2017 02:36 PM
I have to dissagree, I am seeing OSPF traffic in my traffic log, which is why I brought it to the tac attention.
I get that the PA is different, but I would presume that a next gen system, that has all this smarts in it would atleast understand the OSPF protocol.
A session should easily be follow, the OSPF deamon seems to be able to do it.
Having said that, the OSPF network does seem to be stable my adjancy stats show long periods of time.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-01-2017 03:37 PM - edited 08-01-2017 03:38 PM
Where/how are you seeing OSPF entries in the Traffic log? Do you have Security Policies in place to allow OSPF traffic, or something?
All of our PA firewalls are confgured to use OSPF for routing, but none of them have Security Policies for allowing OSPF traffic (with default deny enabled), and none of them show OSPF entries in the Traffic log. The only entries are in the System log.
We're running PanOS 6.1.x, so things may be different in newer versions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-01-2017 04:12 PM
Yes I do have policies in place..
Thats interesting, i could see that happening.
Now I need to test this some how... sigh..
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-03-2017 01:43 PM
So i tested and when i removed the policies it stop the OSPF from creating neighour association with the other routers
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-03-2017 02:26 PM
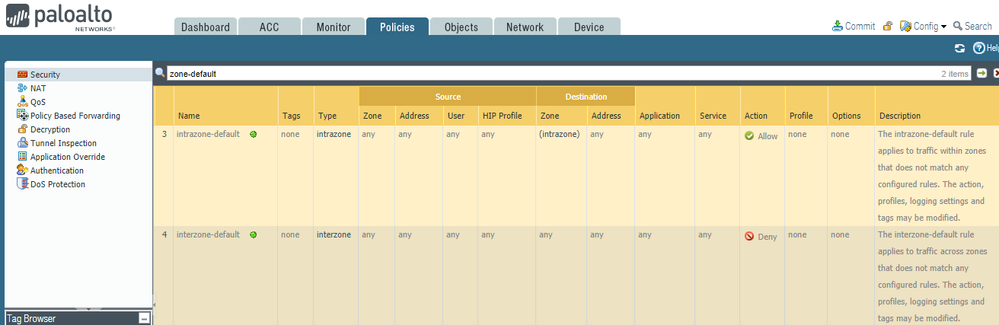
Palo Alto Networks firewalls have 2 implicit/default security rules that are always at the end of the policy. In recent PAN-OS versions, they are highlighted in yellow and can be modified. In older PAN-OS versions, they are not visible. In all cases, their behavior can be overridden by adding explicit firewall rules above.
the default intrazone-default rule permits traffic within the same zone, without logging or security profiles.
intrazone means "within the same zone". This rule permits "trust" to "trust" traffic. If you're running OSPF on the inside of your network, and the firewall is participating in OSPF, the source of the OSPF traffic is trust, and the destination is also trust. This traffic matches the intrazone-default rule WITHOUT LOGGING. So if you're running OSPF and not seeing logs, that's why.
If you'd like to see logs for OSPF traffic, you have a few choices:
1.) create an explicit security policy that permits OSPF from trust to trust, with logging.
2.) create an explicit security policy that permits all trust to trust, with logging
3.) modify the implicit/default intrazone policy and enable logging.
The last rule is the interzone-default rule, which means "between different zones". This rule denies all traffic between zones, without logging.
If your 3rd-to-last security rule is "deny any any with logging", that will override both of the implicit/default rules. This breaks OSPF, BGP, IPSEC, SSLVPN, Captive Portal, etc. and anything else that is to/from the same zone. I believe this is the main reason why Palo Alto Networks made those implicit rules visible and editable.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-03-2017 03:26 PM
I had a rule a #2, basically said any to any OSPF allow.
But the issue was it was logging lots of what seems like erronous messages in the traffic log.
sessions expiring with 0 bytes or session ageing out ..
I would have thought if the OSPF router understands ospf session the firewall would to..
Anyway
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-03-2017 04:42 PM
I'd be interested in seeing the logs you're describing.
It might help to think of it this way. The "traffic log" is a log of the packets permitted or denied by the "traffic enforcement module". The only things you'll see here are uninteresting "firewall sessions" that say "OSPF is running between these two systems".
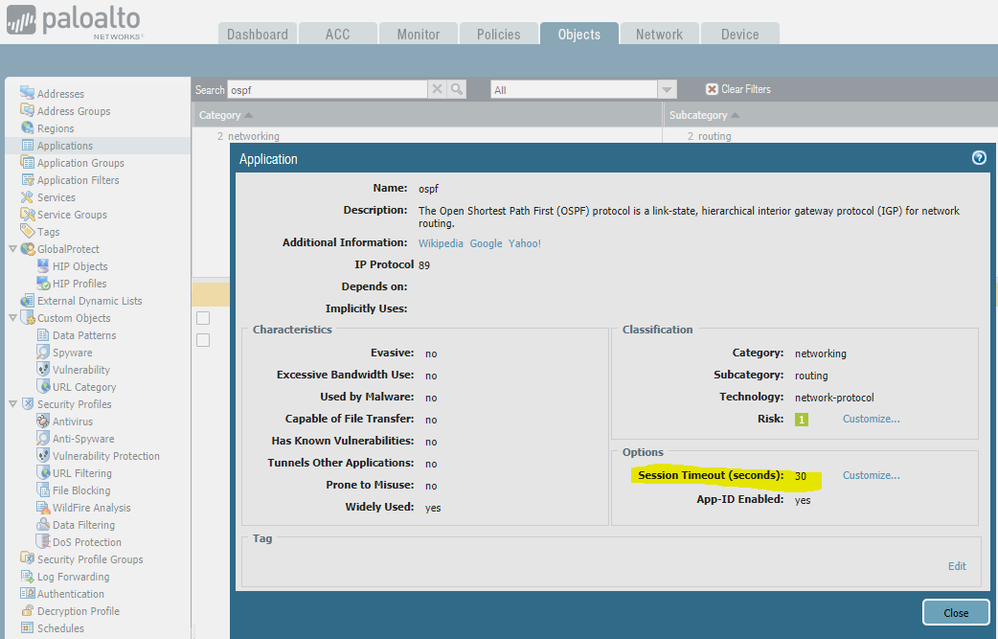
The App-ID definition for OSPF has a built-in timeout of 30 seconds. This means that 30 seconds after not seeing any OSPF traffic, the session is expected to age out.
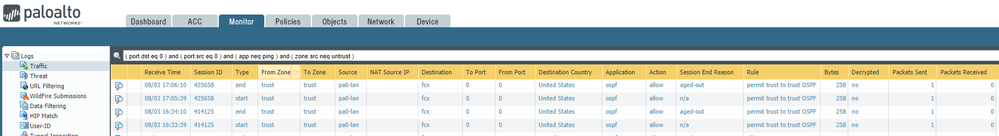
With an "OSPF allow" security policy, log at session start, and log at session end, here's what you'd expect to see in the traffic log:
The bottom log is the session start log - so there's not "session end reason" yet. At the time the session started, there was 1 packet sent. 30 seconds later, the session ages-out per the App-ID definition mentioned above. In a steady state, OSPF sends periodic updates in intervals from 30 to 60 minutes. You may get more or less logging detail depending on things like broadcast vs p2p, etc.
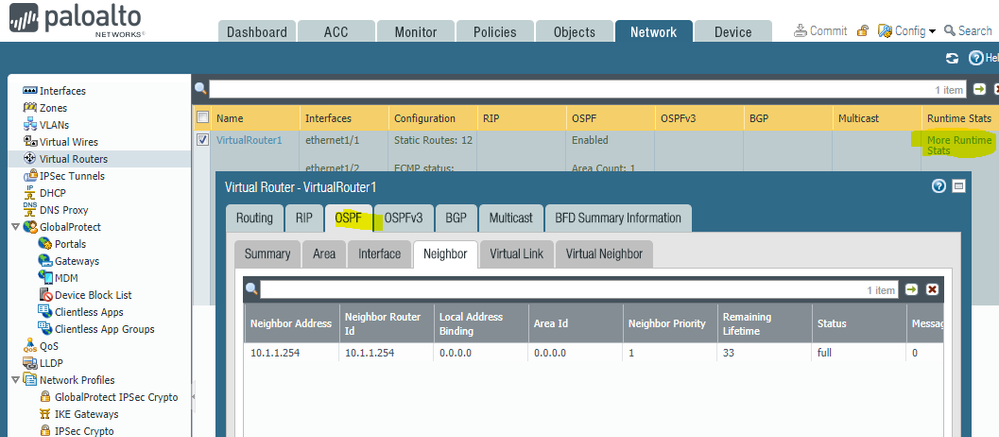
In the GUI, you can see quite a few statistics for OSPF in the Virtual Routers / Runtime Stats section:
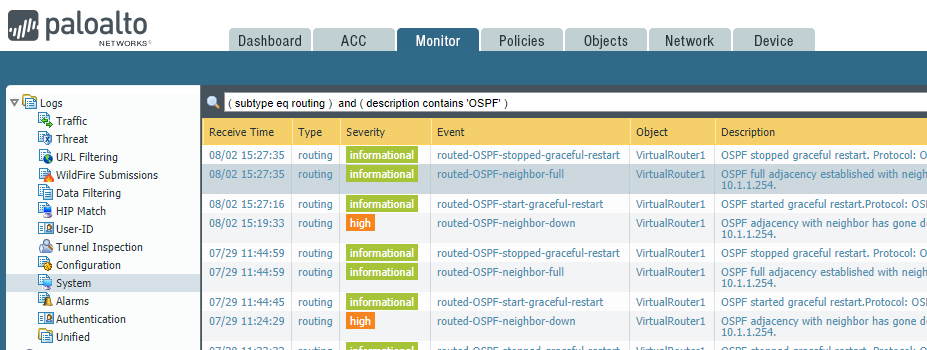
The runtime stats show the current state of all routing protocols (including OSPF), but the system logs mentioned earlier, contain a history of the OSPF processes and state:
Finally, there are also quite a few CLI-based commands to provide additional insight into the OSPF state:
admin@pa0-black_knight(active)> find command keyword ospf show routing route destination <ip/netmask> interface <value> nexthop <ip/netmask> type <static|connect|bgp|ospf|rip> virtual-router <value > count <1-524288> ecmp <yes|no> afi <both|ipv4|ipv6> safi <both|unicast|multicast> show routing protocol redist ospf virtual-router <value> show routing protocol redist ospfv3 virtual-router <value> show routing protocol ospf summary virtual-router <value> show routing protocol ospf area virtual-router <value> show routing protocol ospf interface virtual-router <value> show routing protocol ospf virt-link virtual-router <value> show routing protocol ospf neighbor virtual-router <value> show routing protocol ospf virt-neighbor virtual-router <value> show routing protocol ospf lsdb virtual-router <value> show routing protocol ospf dumplsdb virtual-router <value> show routing protocol ospf graceful-restart virtual-router <value> show routing protocol ospfv3 summary virtual-router <value> show routing protocol ospfv3 area virtual-router <value> show routing protocol ospfv3 interface brief <yes|no> virtual-router <value> show routing protocol ospfv3 virt-link virtual-router <value> show routing protocol ospfv3 neighbor brief <yes|no> virtual-router <value> show routing protocol ospfv3 virt-neighbor brief <yes|no> virtual-router <value> show routing protocol ospfv3 lsdb scope <link-local|area-local|as-local|all> adv-rtr <ip/netmask> area-id <ip/netmask> lsa-id <ip/netmask> hexdump <yes|no> filter-type-area <inter-area-prefix|inter-area-router|intra-area-prefix|network|router|nssa> virtual-router <value> show routing protocol ospfv3 dumplsdb scope <link-local|area-local|as-local|all> adv-rtr <ip/netmask> area-id <ip/netmask> lsa-id <ip/netma sk> hexdump <yes|no> filter-type-area <inter-area-prefix|inter-area-router|intra-area-prefix|network|router|nssa> virtual-router <value> show routing protocol ospfv3 graceful-restart virtual-router <value> debug device-server dump idmgr type ospfv3-virtual-link id <1-4095> debug device-server dump idmgr type ospfv3-virtual-link name <value> debug device-server dump idmgr type ospfv3-virtual-link all debug lpmgrd dump idmgr type ospfv3-virtual-link id <1-4095> debug lpmgrd dump idmgr type ospfv3-virtual-link name <value> debug lpmgrd dump idmgr type ospfv3-virtual-link all debug routing pcap ospf on virtualrouter <value> debug routing pcap ospf off debug routing pcap ospf delete debug routing pcap ospf view debug routing pcap ospfv3 on virtualrouter <value> debug routing pcap ospfv3 off debug routing pcap ospfv3 delete debug routing pcap ospfv3 view admin@pa0-black_knight(active)>
So, if you're looking for detail on how OSPF is working, the system logs, virtual router stats, and CLI commands are your best bet.
Hopefully that helps clear up some of the confusion. I'd be happy to look at your OSPF traffic logs if this doesn't clear things up.
- 9306 Views
- 21 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Security Policy with Destination Criteria in Strata Cloud Manager
- WTH is process 'touch' and hwy is it showing zombie? in General Topics
- User-ID mapping log is empty in General Topics
- Install XDR agent for unmanaged PC in remote users in Cortex XDR Discussions
- Getting 'Unidentified network' when connected to Global Protect - 6.2.8 in GlobalProtect Discussions