- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
PA and VPC
- LIVEcommunity
- Discussions
- General Topics
- Re: PA and VPC
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-08-2021 09:57 PM
This is a pretty common configuration for anyone using a Nessus device and the Pro/Con list is really that of vPC in general on that platform. From a PAN perspective a vPC is invisible, and it has the added benefit that you can lose a chassis without an associated firewall failover.
If you have Nessus hardware, there's really no good reason not to use a vPC instead of just having each node go to one Nessus chassis.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-09-2021 01:22 PM
Hi @BPry
Thanks for the reply . can you explain what do you mean by "From a PAN perspective a vPC is invisible"
and also "you can lose a chassis without an associated firewall failover"
Second question
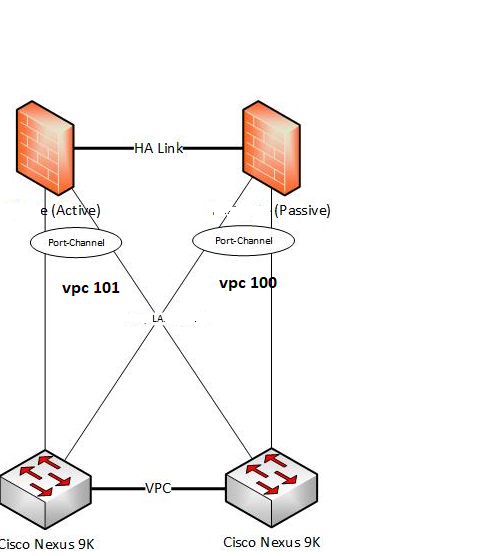
in vpc 101 since there is all ports are designated both active and passive firewall will receive traffic. (Correct me if I am wrong)
If that yes how a passive firewall handle the traffic
Thanks.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-11-2021 07:07 AM
Thanks for the reply . can you explain what do you mean by "From a PAN perspective a vPC is invisible"
You don't do anything special on the firewall when using a virtual PortChannel (vPC) versus a normal PortChannel. It's still just a simple aggregate interface from the firewalls perspective.
and also "you can lose a chassis without an associated firewall failover"
Generally for folks who don't have Nexus switches that have a similar setup, they wouldn't be able to use a vPC and would just use two regular PortChannel configurations. One firewall would be connected to one switch, and the other firewall would be connected to the other.
The downside of the above configuration is that if you lose the switch your Active firewall is operating off of, you would also trigger a firewall failover. That's not an issue with your vPC configuration, because if one of your Nexus switches goes down the firewall still has the leg to the other switch to operate off of.
Second question
in vpc 101 since there is all ports are designated both active and passive firewall will receive traffic. (Correct me if I am wrong)
If that yes how a passive firewall handle the traffic
VPC 100 is going to your passive/secondary firewall and VPC 101 is going to your Active/Primary firewall correct? When your firewall is in a Passive state, it drops all traffic that it receives. So with you using an Aggregate interface, you'll actually want to run LACP and enable LACP pre-negotitation so that your passive firewall sends LACP messages to bring the AE link up to allow faster failover. The passive firewall will drop any actual traffic that it receives, but the LACP messages are enough to keep the vPC up to allow fast failover.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-21-2021 03:45 PM
Hi
@BPry your help to the community is always awesome. No words to comment about your help
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-21-2021 04:03 PM
Hi
The third question was about how a passive firewall handles the data traffic, In VPC the switch will send the traffic in all ports . And the passive firewall drops all traffic. That means the actual data traffic is ended nowhere ?
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-21-2021 09:24 PM
This ARTICLE goes into how the pre-negotiation feature actually works for the Passive firewall. The feature effectively allows LACP/LLDP to actually pre-negotiate the connection to allow for faster failovers.
If you don't enable pre-negotiation, the interface isn't actually accepting any traffic on the passive firewall. So while it's interfaces will show connected, it doesn't respond to ARP or anything like when it's in a passive or non-functional state.
- 7637 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Max number of units (aeX.Y subinterfaces) supported under a single AE interface? in Next-Generation Firewall Discussions
- Windows-Remote-Management & Implicit Use of Web-Browsing in General Topics
- Cortex XDR manager upgrade in Cortex XDR Discussions
- Activate ECMP without trafic disruption in Next-Generation Firewall Discussions
- Cortex XDR – Unable to Assign Read/Write Permissions for Mobile Device (Detected as CD-ROM) in Permanent Exceptions in Cortex XDR Discussions