- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Panorama Managed Devices names missing in HA peer, and show as disconnected when they're not!
- LIVEcommunity
- Discussions
- General Topics
- Panorama Managed Devices names missing in HA peer, and show as disconnected when they're not!
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Panorama Managed Devices names missing in HA peer, and show as disconnected when they're not!
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-11-2020 08:24 AM
Hi,
I'm using Panorama 8.1.13 to manage 60 or so firewalls. Mostly PA-220s with a few PA-5220. These firewalls are in a number of templated device groups.
Both Panoramas are M100 appliances. The Managed Devices are correct on the primary Pano. The Device Names and Serial Numbers are correct, and they are in the correct device groups.
My problem is with the HA peer. The managed devices on the secondary peer show some of the PA-5220s names are missing. The name is shown as the serial number. These firewalls or virtual systems are shown as disconnected, but on the primary, they are not disconnected.
Do I need to change the HA to the secondary, delete the firewalls that are in error, and re-add them using their serial numbers? Will that resolve the names and connect status? Will this cause me problems with pushing changes?
Thanks,
Ambi
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-11-2020 08:32 AM
Hi @Ambidexter6
In the Individual firewalls, the IP address of the Peer Panorama might be missing on the devices which are being displayed as disconnected. Can you check it out.
Thanks.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-11-2020 08:47 AM
Hi,
Thanks for your suggestion!
Unfortunately, the two panorama servers are defined in the Panorama Settings dialog. We're enabling push, with 240 second timeouts and a 25 SSL retry count.
I might want to see if deleting the secondary's IP in a firewall then adding it again makes it work. The problem with this is the Panorama servers are defined by template. So I'd need to override it, the revert it. That may be more than I want to do.
Is there a CLI command to show the status of connections to the Panorama peers...both on Panorama to see the firewalls, and the firewalls to see both Panoramas?
Thanks,
Ambi
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-11-2020 08:55 AM
On the firewall, you can check the status of connection to the panoramas by this command - "show panorama-status" in user-exec mode.
On the Panorama, you can check by these commands - "show devices all"/"show devices connected" in user-exec mode.
Hope this helps.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-11-2020 09:42 AM
Hi @Ambidexter6 ,
I had also went through the same issue we restarted 'management-server' process on affected gateway and post it gateway started showing connected.
You can try with this.
NOTE - Trying this shouldn't create any impact on dataplane.
Hope it helps you!
Mayur
Check out my YouTube channel - https://www.youtube.com/@NetworkTalks
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-19-2020 06:49 AM
Hi,
I finally figured this out!
The issue is that the management interface on all the firewalls needs to have the "Permitted IP Addresses" which defines which IPs can permit SSH, SNMP, ping, etc.
This is located in Panorama -> Setup -> Interfaces -> Management -> Permitted IP Addresses.
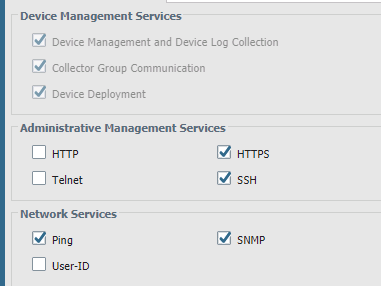
The thing that made me finally figure this out was the "Device Management Services" section:
That section isn't in every firewall, just Panorama, whereas the othere sections (Administrative Management Services, and Network Services) are in every firewall.
But how could I not see that the firewalls were all in the permitted list? That's easy. We've got over 70 firewalls, and the page these go into on Panorama (or any firewall) only scrolls. It does not page, it does not allow import/export, and you can't resize the window. So, unless you show them in the CLI, there's no way to really know for sure that they're in there.
For example, I can't export them, and I can't template them, so I have the 70 firewalls, as well as IPs for any user, monitoring device, SNMP manager, syslog machine, etc. defined here, so I have at least 100 devices.
Now, the list is templated for the firewalls themselves...that is to say, each firewall's individual list of permitted IPs is identical as they all use the "Base" template for such settings. But for Panorama, it's all manual.
So what I needed to do was screen-shot the 5 pages of firewalls from the working, primary Panorama, and do the same thing with the Secondary. Then, highlight which was missing on each side (if there was something missing from the Primary, it would show up).
Now, this could be easier by using the CLI, but I dissuade casual users of Panorama from SSH-ing into it, so I wanted to document the procedure with the GUI. And it works, but it's smelly.
Thanks for your assistance!
Regards,
Ambi
- 8328 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Few Objects are missing on firewall while Migrate a Multi-vSYS enabled Firewall HA Pair to Panorama Management in Panorama Discussions
- static route with path monitor down not removing BGP route in General Topics
- XML API Results for Custom Report Not Matching Data From Panorama GUI in General Topics
- Python: panos opstate in General Topics
- [API] - User-ID in General Topics