- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Persistent issue with APP-ID Reliability
- LIVEcommunity
- Discussions
- General Topics
- Persistent issue with APP-ID Reliability
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Persistent issue with APP-ID Reliability
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-29-2019 10:24 AM - edited 10-29-2019 10:25 AM
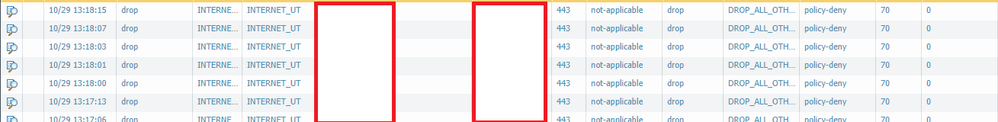
Hello all. I have had an issue with PANOS since 7.0 (Currently I am on 9.0.2-h2) where the application id feature is not reliable in security rules. I can add a rule and for example lets say I allow ssl to 10.1.1.1 from 10.2.1.1 no user restrictions and just add the ssl application and commit. Then I try to access https on 10.1.1.1 from 10.2.1.1 and the traffic will be allowed. Then an hour later I try again and this time it will drop. When I go into monitor. Below is legitimate traffic being dropped because the application is "not-applicable"
In order to resolve this what I have to do is clone the rule and place it below or above and remove the applications and set it to any then set service to select and choose 443. I have so many redundant rules because of this and I am sick of doing it. Does anyone else have this problem or is it just me?
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-30-2019 05:56 AM
Hi @scottoliver ,
Do you get any more information in the log details ?
Not-applicable usually means that the Palo Alto device has received data that will be discarded because the port or service that the traffic is coming in on is not allowed, or there is no rule or policy allowing that port or service:
Not-applicable in Traffic Logs
Cheers !
-Kiwi.
Cheers,
Kiwi
Please help out other users and “Accept as Solution” if a post helps solve your problem !
Read more about how and why to accept solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-31-2019 02:49 PM
Still no resolution on this I have opened ticket but no fixes yet
- 3039 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!