- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Problem connecting SSH
- LIVEcommunity
- Discussions
- General Topics
- Re: Problem connecting SSH
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-16-2014 07:24 AM
I have a vpn configured (PA<->PA) to manage my FWs.
The problem is that when I open a ssh to the FW ip LAN (10.105.0.7), session ssh runs successfully and I can connect to the FW. But if I open ssh to the management ip 10.98.200.16 ssh remains frozen.
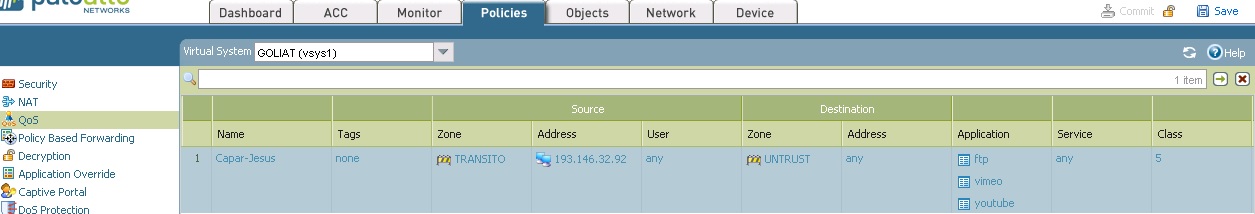
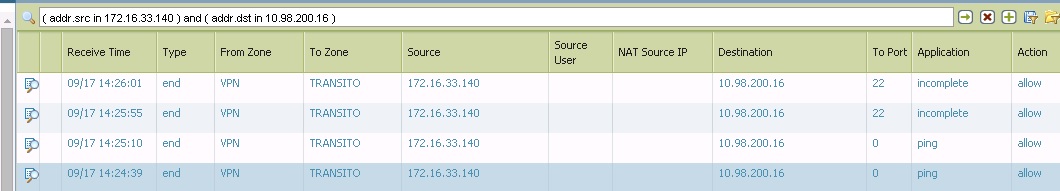
Looking at the log monitor, when i try the LAN ip i can see how the PA recognise the Application SSH, but trying with the management ip the FW is not recognising correctly and it shows INCOMPLETE.
Looking also at session browser when I run ssh session to the LAN ip, FW is not applying a Qos policy but is i try with management IP the FW is applying a Qos rule when it shouldnt do it.
Why this strange behavior between ssh in LAN ip and management IP.
I attached all the tests.
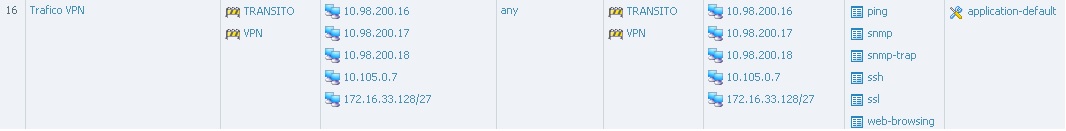
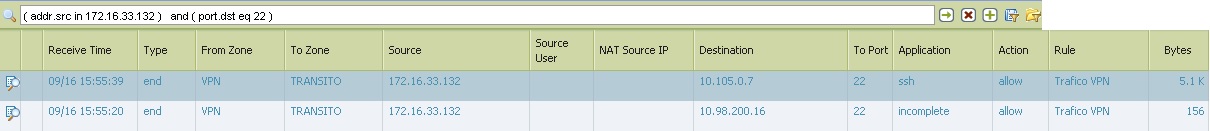
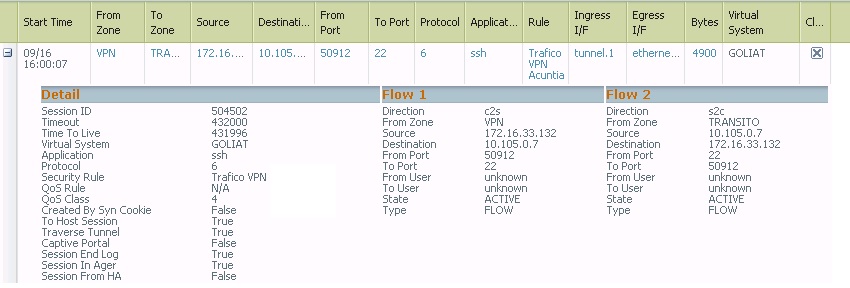
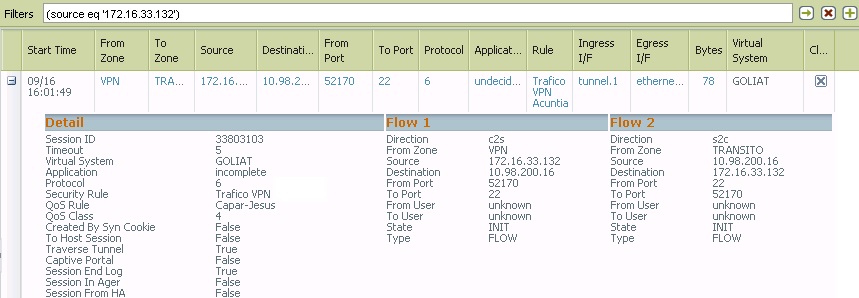
- Labels:
-
Configuration
-
Troubleshooting
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-16-2014 12:09 PM
HI COS,
It seems Management interface has not even seen SYN Packet. It proves SYN is dropped on Data plane.
Did you see any drop packet in capture, if NO than final thing is to do flow basics.
Follow bellow instructions for flow basics, if its not used with care than it can crash firewall. Let me know for any question.
Packet Capture, Debug Flow-basic and Counter Commands
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-16-2014 12:22 PM
Hi COS
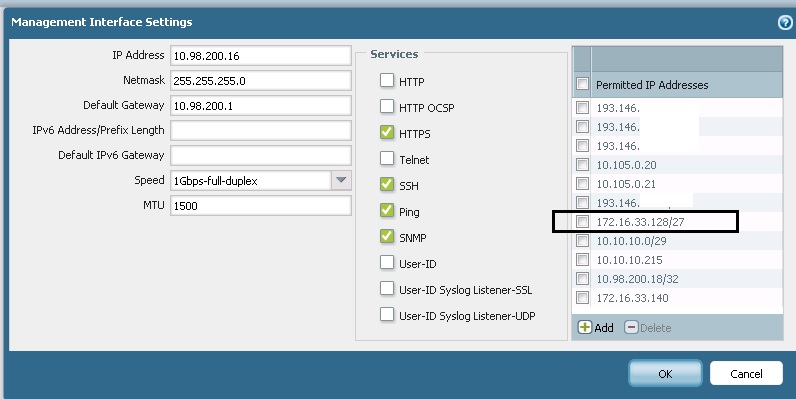
Could you please verify if there are any set permitted IP addresses defined under management interface settings?
And if the source IP from which you are doing SSH is in that permit IP address list ?
Hope it helps !
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-16-2014 12:28 PM
Yes, the ip 172.16.33.132 is allowed.
Ill do this debug tomorrow. Please confirm this config (filter), it could crash using this short filter????
- debug dataplane packet-diag set filter on
- debug dataplane packet-diag set filter match source 172.16.33.132 destination 10.98.200.16
- debug dataplane packet-diag set log feature flow basic
debug dataplane packet-diag set log on
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-16-2014 12:36 PM
Hi COS,
NOTE: I strongly encourage to contact TAC for flow basics, unless you are confortable.
Debug appears good to me. Make sure you disable logging once you try to access firewall. Use following command for it.
debug dataplane packet-diag set log off
Following command to view output of flow basics.
less dp0-log pan_packet_diag.log
Then following commands to disable everything
debug dataplane packet-diag set log off
debug dataplane packet-diag set filter off
debug dataplane packet-diag clear log log
Refer following guide for details.
Packet Based Troubleshooting - Configuring Packet Captures and Debug Logs
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-16-2014 01:10 PM
Hello COS,
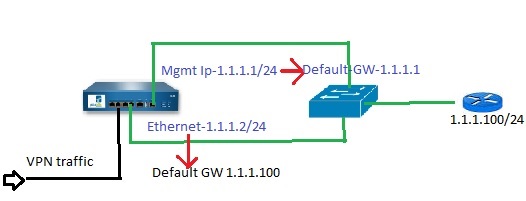
Only for routing info, mgmt interface has the default gateway, but service route is for firewall services. For mgmt access, the mgmt interface will have to respond which will only happen if there is a default gateway. You have 2 options here.
For example: Option-1
If you want to keep Mgmt and physical interface in the same broadcast domain:
Mgmt interface IP-1.1.1.1/24
Data-plane Ethernet interface IP- 1.1.1.2/24
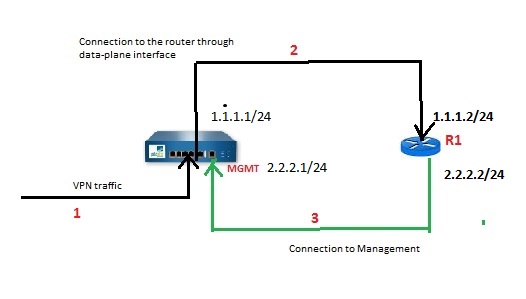
For example: Option-2
If you want to keep Mgmt and physical interface in 2 different broadcast domain:
Mgmt interface IP-2.2.2.1/24 Default gateway- R1(2.2.2.2)
Data-plane Ethernet interface IP- 1.1.1.2/24 Default gateway- R1 (1.1.1.2)
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-16-2014 01:19 PM
Hello Hardik,
Try to understand the flow of the packet here. The packet is received in PAN FW's data-plane interface and sending directly to the mgmt interface IP. How could the mgmt interface will send back the response..? service route is for firewall services not for SSH. We need to have a L-2 loop if both Mgmt and data-plane interfaces are belongs same broadcast domain else, need to re route the traffic through a L-3 device.
You may test this, if you have bandwidth.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-16-2014 01:25 PM
Hi HULK,
I didnt find any info which confirms its a L2 loop. If its L2 loop than atleast SYN/ACK should have been seen on the management interface.
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-16-2014 01:30 PM
Hello Hardik,
It's not a L-2 loop, but you have to create a loop to make it work. Why the management interface will respond to it's data-plane traffic....? service route is for firewall services not for SSH.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-16-2014 01:42 PM
I think you might be right. All I wanted was to do flow basics to find out root cause for drop packets. Thats worth testing.
I didnt realize that MAnagement and Data port are in same LAN.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-17-2014 05:31 AM
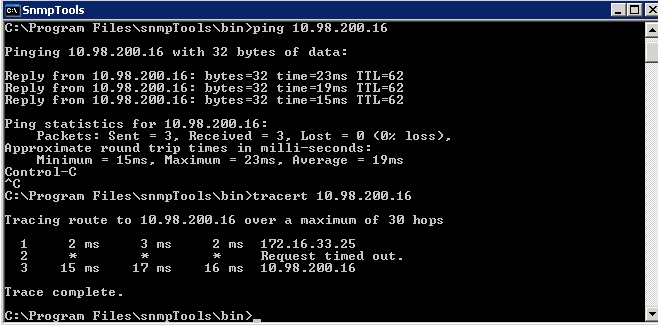
Yes, but if it was a routing problem the management ip would not respond to ping. I can ping the management inteface and do a trcert succesfull.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-17-2014 06:33 AM
Hello COS,
Yes, you are correct. You do not have any routing problem here. Since, the firewall will not be able to send SSH packets from a data-plane interface to management interface directly. Ping and traceroute ( both uses ICMP) is part of firewall service to reach managaement plane through a service route. But for SSH, web-browsing etc, you have to apply above mentioned Option-1 or Option-2.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-17-2014 07:26 AM
Yes.
In the LAN eth1/22.250 is configured OSPF and the FW s sending the traffic to 10.98.200.16 throguh this interface by OSPF.
I think OSPF routers should know how to arrive to the management ip (10.98.200.16), because 10.98.200.0/24 is running over OSPF.
what do you recomend me to do??
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-17-2014 07:32 AM
Hello COS,
Do you have a Layer-3 device in place. So, you can re-route all packets for destination: 10.98.200.16 to a L-3 device and that device will send to the management interface of the PAN firewall through an another connected interface ( Layer-3 device to Mangement Interface).
Thanks.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-17-2014 08:08 AM
Its my client´s network i only give support to FW Palo Alto, i dont know exactly what is behing PA in the client side. I am guided by Palo Alto config.
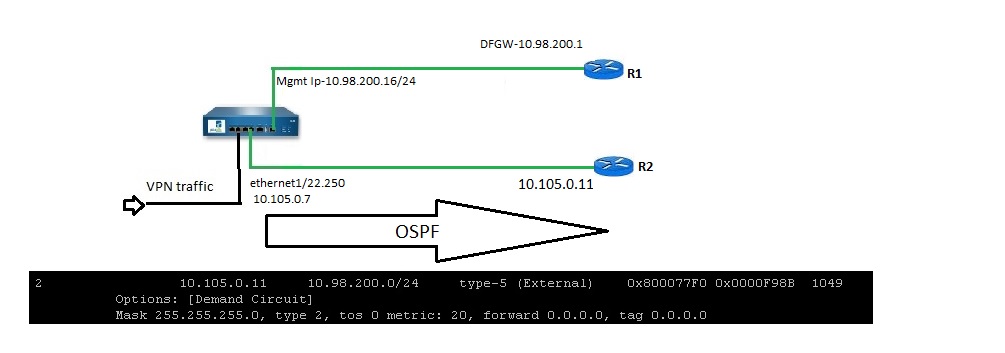
I suppose its something like this. OSPF speaking between L3 devices. i suppose in this case R1 and R2 should speaking OSPF to reach IP 10.98.200.16 to the MGMT interface.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-17-2014 08:21 AM
Hello COS,
You are absolutely correct. You may use a single L-3 device i.e R-1 and connect ethernet-1/22.250 in one interface (10.105.0.11)and mgmt in another interface (10.98..200.1). You can use any routing protocol, since static will be easier![]() .
.
Hope this helps.
Thanks
- 20312 Views
- 29 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Network connection unreachable on MAC OS newer version 15.3.2 o higher in General Topics
- User Removed From LDAP Authentication Group Still Able to Connect to VPN in GlobalProtect Discussions
- About UIA SSL connection in Next-Generation Firewall Discussions
- Azure to OnPrem Connectivity issue in Next-Generation Firewall Discussions
- Discord voice chat no longer connecting after PA-440 install in General Topics



