- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
reconfigure DNS and PAN3020 firewall
- LIVEcommunity
- Discussions
- General Topics
- Re: reconfigure DNS and PAN3020 firewall
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
reconfigure DNS and PAN3020 firewall
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-30-2014 02:33 PM
Currently i two AD dns zones in on my DNS server (windows):
mycompanydom.com - internal domain
mycompanyplan.com - external domain where all our internet webservers and web applications live.
my A records in mycompanyplan.com point to internal non routable IPaddress for each internal server so the traffic does not go out the firewall and back in. We also have 3 IPSEC VPN tunnels where the dns zone information is replicated to. My problem that i run into is if a tunnel goes down then my users in those sites cannot get to the services they need because their dns query is resolving to a non routable internal IP and trying to go down the tunnel vs resolving to the external IP.
I would like to remove that zone completely from my DNS infrastructure and that way all dns queries to mycompanyplan.com resolve to the external IP's instead. My 3 satellite offices would route out their firewall to the external IP vs currently routing down the vpn tunnels. Is there a way to configure the PAN3020's in my HQ where all of my inbound web services reside to see the traffic and have it loop back without having to go out the external interfaces only to come back in? Not sure if i am making sense while writing this, so if you need clarification please let me know.
Maybe a another way to say this is, if a company has inbound web servers how is everyone setting up DNS and routing traffic when those web servers are in the same office but have need to be accessible externally? Is there a way to prevent that traffic from leaving the firewall only to come back in?
- Labels:
-
Networking
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-30-2014 02:36 PM
Sounds like you need to configure a U-Turn NAT Policy. You can access internal resources via a public IP address or public pointing A record. By using this link you will access the same A record that you would from the external and you will have access to the services. Use this link below and I have attached screenshots as well.
U-TURN NAT POLICY
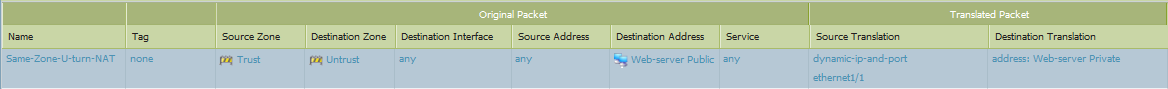
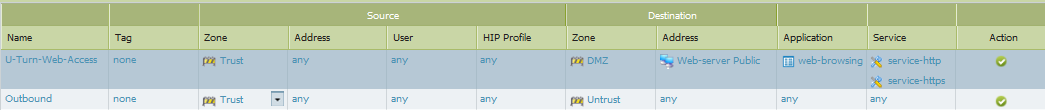
SECURITY POLICY:
your security policy will vary based on your needs
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-30-2014 03:30 PM
Hello EDS admin,
Based on description U-Turn NAT will help in this scenario. But still few information is unclear.
Following Two Sentences are contradictory: Please clarify.
mycompanyplan.com - external domain where all our internet webservers and web applications live.
my A records in mycompanyplan.com point to internal non routable IPaddress for each internal server so the traffic does not go out the firewall and back in
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-30-2014 03:33 PM
Hi EDSAdmin,
You can use public IP address across the tunnel. If traffic flows through Tunnel than NAT it to Private IP address.
If tunnel is down and its going through regular internet link than also server will be accessible through public IP.
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-30-2014 03:37 PM
Indeed, we will need a U-Turn NAT configuration here.
In addition to the NAT documents provided above, here is a good illustration of how the Palo Alto appliance handles NAT and why the U-Turn NAT rules will have to be configured in a specific way that may not make sense at first.
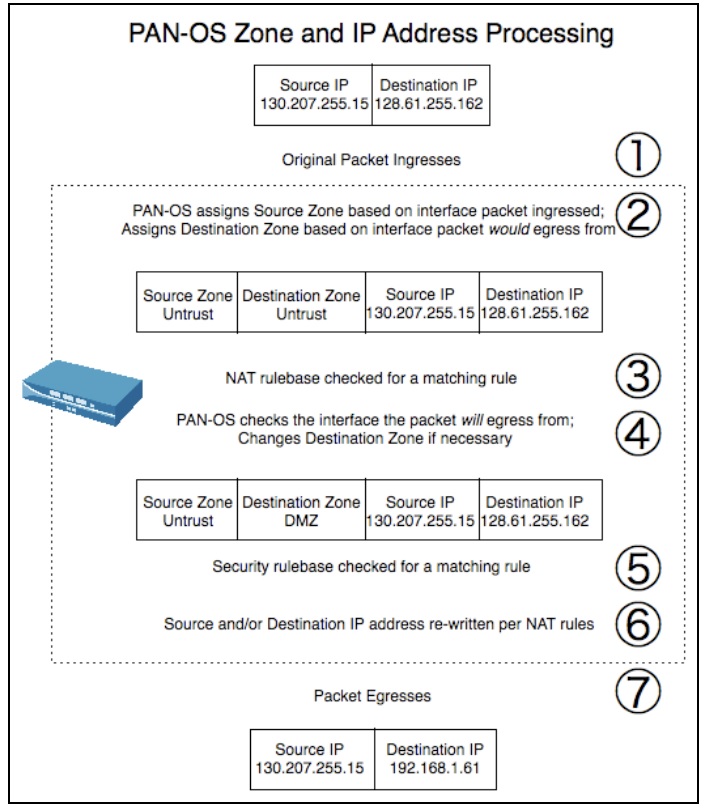
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-30-2014 03:40 PM
In addition to my above NAT examples, here is our example of how to configure the U-Turn NAT.
Please let us know if you have any questions.
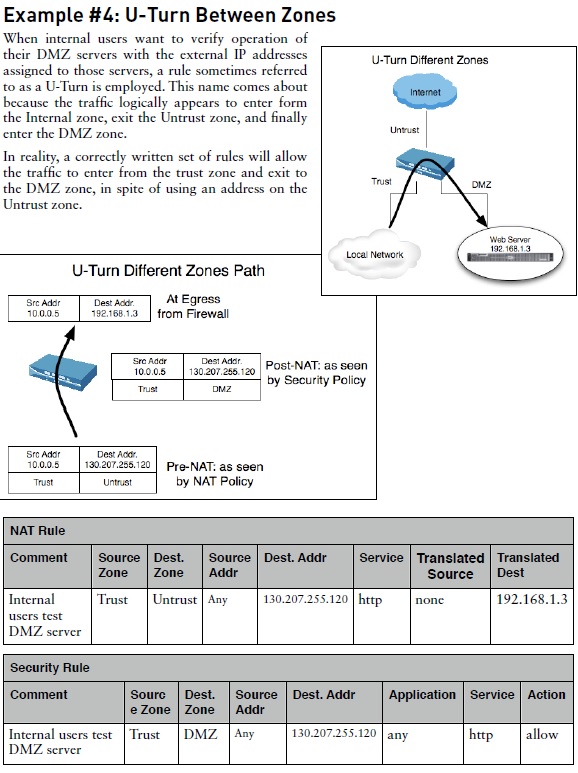
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-30-2014 11:13 PM
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-01-2014 08:40 PM
in the two sentences that you mentioned to clarify.
the a records i am referring to that point to non routable IP addresses, what i meant was the A records in my windows DNS server. i have zone there that is called mycompanyplan.com. in that zone all of my webservers A records have internal non routable ips for each webserver so they do not go out the firewall. what i want to do is delete that zone and only have my A records that are configured on network solutions and then as you guys have pointed out setup a u-turn rules.
Will i need a NAT and security rule for each web server, or can i do like jperry posted which from the way i am reading it allows one run to cover all my servers.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-01-2014 08:43 PM
hshah wrote:
Hi EDSAdmin,
You can use public IP address across the tunnel. If traffic flows through Tunnel than NAT it to Private IP address.
If tunnel is down and its going through regular internet link than also server will be accessible through public IP.
Regards,
Hardik Shah
how would i set this up? would this be instead of the u-turn or in addition to adding the u-turn? what is the best practice/preferred method?
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-01-2014 10:45 PM
Yes you will need a Uturn NAT and security rule for each server to allow this to one. Because with out the U-Turn NAT rule you will not be able to route to the A record on the Public IP address and without the Security Policy you will not be able to allow traffic to your server. If you already have a security policy for your server then you don't need an additional security policy. Let me know if you have further questions
Also are you using Exchange Outlook anywhere? Is your internal domain name the same as you external domain name? If so that could be interesting and U-turn NAT may be the best solution but let me know the details. If you are using Exchange 2010 I have deployed that in multiple scenarios as well is 2007 and below. Let me know when you can.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-02-2014 06:59 AM
Hello EDS Admin,
Following is easiest implementation for IPsec hosts. BELIEVE ME. THINK OVER THIS.
Hi EDSAdmin,
You can use public IP address across the tunnel. If traffic flows through Tunnel than NAT it to Private IP address.
If tunnel is down and its going through regular internet link than also server will be accessible through public IP.
Regards,
Hardik Shah
- 5149 Views
- 10 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- User-id with GP client certificate authentication in GlobalProtect Discussions
- Listing Backup GlobalProtect Portal in GlobalProtect Discussions
- restoring an NGFW from factory default in Next-Generation Firewall Discussions
- Adding SAML authentication profile from second AzureAD to existing gateway in GlobalProtect Discussions
- Panorama upgrade to 10.1.3-h in Panorama Discussions



