- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
SCCM management of remote GP Windows clients
- LIVEcommunity
- Discussions
- General Topics
- Re: SCCM management of remote GP Windows clients
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-25-2020 05:15 AM
We just deployed and started using GlobalProtect 5.1.1 to support the work-from-home COVID-19 initiative for thousands of remote workers. Everything is working well but my SCCM guys can't manage any of the remote clients to push patches or software updates. Our internal DNS resolves the host names to the last LAN address of the host, not the IP pool address. The same things happens with Cisco AnyConnect clients. I don't know anything about AD or SCCM. Is SCCM management of remote hosts doable and if so, how are you doing it?
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-25-2020 06:49 AM
Yes, this is completely possible. We are doing this today the same as you. All we had to do was create a policy allowing traffic from our "trusted" zone, to the "global protect" zone. There's lists of ports out on the web for the various SCCM functions. For example, for remote control here's the ports required per-microsoft:
1. Port 135 - TCP
2. Port 3389 - TCP
3. Port 2701 - TCP/UDP
4. Port 2702 - TCP/UDP
I believe patching uses 445 for SMB transfers. So depending on what you want to do there's multiple things you'll have to allow.
A couple of other things to keep in mind with AD/SCCM is 1. DNS will take time to update after clients connect. So your techs might have to ask the user for the IP and use this in the remote control client of SCCM. 2. AD Sites and Services, and SCCM boundary groups need to include your VPN ranges for the SCCM clients to check in properly and be managed. This also helps them control which SCCM distribution point serves the patches/apps to clients so you can know where traffic is coming from.
https://www.linkedin.com/in/zachary-biles-a5097532/
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-25-2020 06:49 AM
Yes, this is completely possible. We are doing this today the same as you. All we had to do was create a policy allowing traffic from our "trusted" zone, to the "global protect" zone. There's lists of ports out on the web for the various SCCM functions. For example, for remote control here's the ports required per-microsoft:
1. Port 135 - TCP
2. Port 3389 - TCP
3. Port 2701 - TCP/UDP
4. Port 2702 - TCP/UDP
I believe patching uses 445 for SMB transfers. So depending on what you want to do there's multiple things you'll have to allow.
A couple of other things to keep in mind with AD/SCCM is 1. DNS will take time to update after clients connect. So your techs might have to ask the user for the IP and use this in the remote control client of SCCM. 2. AD Sites and Services, and SCCM boundary groups need to include your VPN ranges for the SCCM clients to check in properly and be managed. This also helps them control which SCCM distribution point serves the patches/apps to clients so you can know where traffic is coming from.
https://www.linkedin.com/in/zachary-biles-a5097532/
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-25-2020 10:04 AM
Thanks, Zach. I've allowed the traffic and will have my SCCM guys test.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-25-2020 10:47 AM
Zach, your fix worked! THANKS!
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-25-2020 11:04 AM
Good deal, glad I could help!
https://www.linkedin.com/in/zachary-biles-a5097532/
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-29-2020 03:43 AM
Hi Nelson, apart from the Palo Rules, anything specific you had to do on SCCM? We released patches over a week ago to a test collection, and the devices which are still "on-prem" received the updates, however the devices (users working from home that are connected via Global Protect) are not receiving the updates. All rules and comms to our sccm server are configured and working. Boundary groups within SCCM are also good. Anything I a missing?
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-29-2020 07:10 AM
ColonelHawx, I had to go to my SCCM and DNS folks to give you a proper answer. SCCM guys say if your boundaries are good that's all you have to do there. My DNS people sent me this: "Because VCUHS.mcvh-vcu.edu [which is the domain of our user PCs] is also used by servers, we don’t allow every device using that domain to register with DNS. I had to add the Global Protect pool to the list of networks that are allowed to register [with our Infoblox DNS servers]." SCCM could not resolve PCs names to IP addresses until this change was made. That made it all work.
I hope this helps!
Pete
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-01-2020 05:57 AM
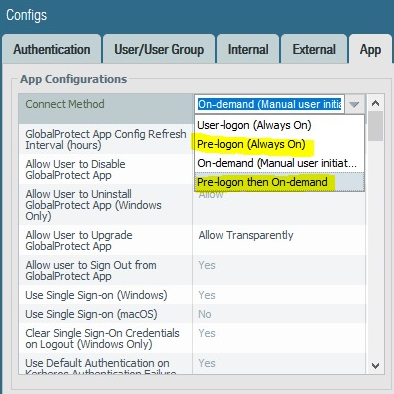
Thanks for the reply. Before I create a new Thread for help... Did you configure your GlobalProtect with pre-logon connection method or user-logon? Someone mentioned on a Palo FB forum, that pre-logon should be set for SCCM to work seamlessly.
Thanks...
PS: Are you by any chance seeing any "aged-out" traffic from your GP Client (Source) to SCCM Server (Destination)?
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-18-2020 03:13 AM
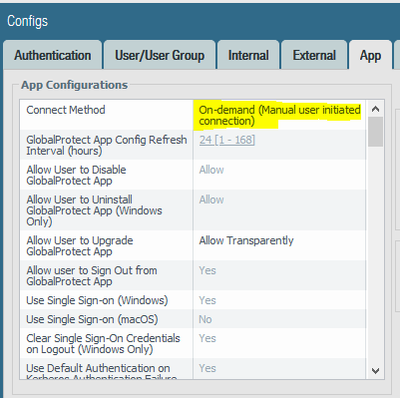
Sorry, ColonelHawx, did not see your previous post. Connection Method is "On-demand (Manual user initiated connection)."
Pete
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-18-2020 03:26 AM
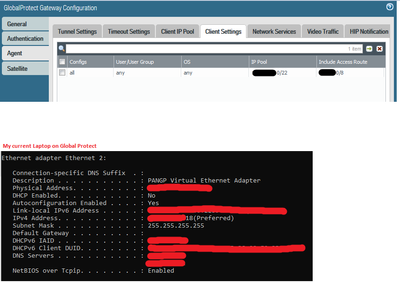
Thanks for this info... It def helps... So we have the EXACT same setting applied. But what really baffles me is that we just tested by deploying a VM within the same subnet as our GP Clients & Primary SCCM server and it worked and received ALL applications and software deployments. But the GP Clients are still not getting it. Can I ask what Version of SCCM you are on? 1910 or 2002? Also, is there anything specific you had done/applied on your Palo GP Config? Our clients are using a /22 range and below is a snapshot of a device using Global Protect.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-18-2020 04:23 AM
SCCM version is 1910. Your GP settings look pretty much the same although we're set up so that our users have to be in a particular AD group. In the HIP profile we specify that the clients must be members of the domain. I'm not seeing any material difference.
Pete
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-18-2020 04:44 AM
Thanks for the help Pete... Yeah we are also using HIP profiles with clients being member of the Domain, having AV etc etc... Will try to figure out whats going on...
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-18-2020 09:26 PM - edited 06-19-2020 08:17 AM
Let us know what you find to fix your issue.
Next week we are also doing Global protect always on connection method for few users to Test it and will see how sccm works
Help the community: Like helpful comments and mark solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-16-2020 05:27 AM - last edited on 07-16-2020 02:24 PM by jdelio
Hi
Why we require Group Policy
For various tasks such as communicating with Active Directory Discovery, Remote administration and WMI connectivity, we require these policies.
There are 3 types of settings we require:
- To Ping Client Workstations (By default this communication is blocked if Firewall is enabled)
- To connect to Clients Admin$ Share
- To connect to clients WMI ( as SCCM heavily relies on WMI repository to store all policies, deployments and other tasks)
Default Behavior of client ( before creating Group Policy)
a. By default, we cannot ping the client workstations in case the firewall is enabled. Even though the machine is switched on and connected on the same network, we will not receive the Ping response.
b. We are not able to connect to the admin$ share of the client (ie clients “c:\windows” directory). This is required for various tasks including SCCM client push installation was setup files over the network copies under client’s c:\windows directory.
c. Inbound remote administration is disabled by default, which means we cannot connect to clients WMI repository remotely. This is mandatory to install SCCM client and to download and save several SCCM policies, deployments & tasks. If we try connecting to clients WMI by using wettest (inbuilt tool on Windows), we will get error “0x800706ba“
Thanks in Advance
Lavanya Sreepada
- 1 accepted solution
- 25495 Views
- 15 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Getting 'Unidentified network' when connected to Global Protect - 6.2.8 in GlobalProtect Discussions
- GlobalProtect VPN Client windows 11 crash in GlobalProtect Discussions
- GlobalProtect client takes extra time to disconnect in GlobalProtect Discussions
- Cortex XDR triggers Code 10 on USB Audio despite exception - Vendor not selectable, need per-device allow without vendor or something in Cortex XDR Discussions
- SPlit tunneling issue on GlobalProtect in GlobalProtect Discussions